
Getty Images/iStockphoto
Kronos attack fallout continues with data breach disclosures
Employees at both public and private sector organizations had their data compromised during a December ransomware attack on Kronos that also took down payroll systems.
More than two months after a cyber attack hit Ultimate Kronos Group, disrupting payroll and timekeeping systems across the world, customers are still being impacted by secondary data breaches.
While ransomware caused massive issues with the Kronos Public Cloud, delaying payroll for customers in mid-December, UKG later determined that the threat actors accessed the cloud environment earlier and stole corporate data before executing the ransomware. As a result, several data breaches related to the Kronos attack have been disclosed or reported over the last two months.
The most recent victim to emerge was the athletic wear company Puma, which was notified of the incident on Jan. 10. The attack caused the information of 6,632 employees to be compromised, all of whom were notified on Feb. 3 by Kronos, according to several state Attorney General Offices that were also notified. According to the letters sent to the potential victims, it was discovered that their Social Security numbers were stolen by the threat actors.
In a statement to SearchSecurity, Puma said that no customer data was impacted and that "the incident was limited to Kronos' Private Cloud."
UKG said in a statement on Jan. 22 that "between January 4 and January 22, all affected customers in the Kronos Private Cloud were restored with safe and secure access to their core time, scheduling, and HR/payroll capabilities." However, the company did not discover the breach of Puma until Jan. 10, a month after the breach occurred.
SearchSecurity contacted UKG for further comment on customer data impacted by the attack. The company declined to comment and instead referenced the Jan. 22 statement. An additional UKG update was published on Feb. 11, which claimed "a relatively small volume of data" was exfiltrated.
"We have analyzed that data set and determined that it contained personal data of individuals associated with two of our customers," the update said. "Both affected customers have been notified."
But since the Kronos attack on Dec. 11, at least five other organizations have reported data breaches as a result, the majority of which are public services or local governments.
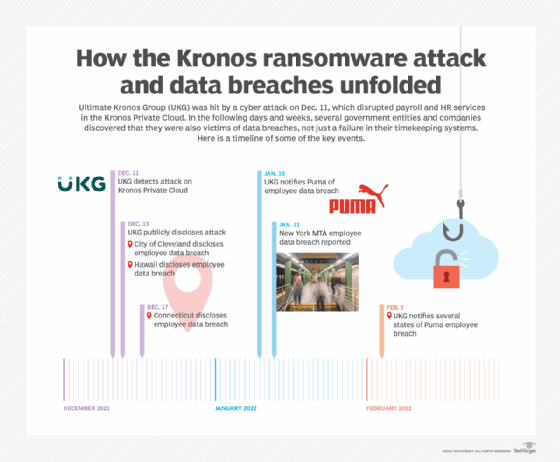
Another customer that later discovered their data had been stolen was New York's Metropolitan Transit Authority (MTA). On Jan. 13 it was reported that information on MTA employees was also compromised in the attack, which disrupted timekeeping systems.
According to an email sent to employees by the MTA's chief administrative officer Lisette Camilo, "the information accessed did not include Social Security numbers, driver's license numbers, bank or other financial institution account numbers, or biometric information." Due to the breach, current and former employees were given two free years of credit monitoring.
The city of Cleveland was one of the first public entities to report a data breach stemming from the attack on Kronos. The mayor of Cleveland at the time, Frank Jackson, announced on Dec. 13 that some of the city's employees had their information exposed, including their names, addresses and the last four digits of their Social Security numbers. The city was exposed because it, like many other companies and agencies, used Kronos' timekeeping software for employees.
Cleveland was not the only municipality to notice a data breach among its employees following the incident with Kronos.
On a larger scale, Hawaii and Connecticut each saw breaches at the state level within some of their services.
In Hawaii, both the Board of Water Supply and its Emergency Medical Services fell victim to data breaches, because of their use of Kronos' services. While it was specified that no customer data was impacted by the breach in Hawaii, employee information was compromised, and workers at both agencies were told to keep an eye on their credit and bank accounts, according to a report by KTVZ.
Connecticut government employees were also impacted by the Kronos attack. According to a December report by The Connecticut Examiner, it was initially unclear what employee data was affected in the attack because the state did not have its own backups for employee records outside of the Kronos Private Cloud.
Warren Lundquist, an IT architect with the state government, told SearchSecurity the Connecticut Department of Administrative Services (DAS) recently informed employees that only names, employee IDs and work phone numbers were at risk from the breach.
"Apparently there is a separate UKG system that houses employee personnel records, which was not at risk in this ransomware incident, according to DAS," he said.








