Getty Images
MacOS malware attacks slipping through the cracks
Apple security specialist Patrick Wardle told RSA Conference 2022 attendees that some of the worst security flaws in the macOS operating system come from overlooked bits of code.
SAN FRANCISCO -- Prominent security vulnerabilities in Apple's macOS often arise from loopholes and overlooked bits of code, according to one expert.
Patrick Wardle, founder of the Objective-See Foundation and a prominent iOS and macOS security researcher, spoke about macOS threats at RSA Conference 2022 in San Francisco on Monday. Wardle told attendees that often the vulnerabilities attackers need to compromise Macs come not from tirelessly fuzzing apps and reverse engineering code, but rather from simply working in the tech giant's blind spots.
To illustrate his point, Wardle pointed to two vulnerabilities, CVE-2021-30657 and CVE-2021-30853, which both relied not on technical software vulnerabilities in the macOS operating system, but rather loopholes in the logic of the operating system that would allow applications to do things they should not.
In the case of CVE-2021-30657, an attacker would be able to bypass the security checks Apple normally provides simply by leaving out a single file. Wardle found that when certain types of applications do not contain the info.plist file, they will not be subject to the scanning tools Apple normally uses to screen out dangerous apps.
The problem, Wardle said, lay within the way macOS dealt with scripted applications. When built without the info.plist file, an application will use secondary tools to launch that will not make the normal security checks.
"In the Finder and system point of view, it is an application," Wardle explained. "Because it was missing an info.plist file, the system said no problem."
As a result, macOS malware could potentially run on a system without being caught by Apple's own security tools and checks. Wardle noted that CVE-2021-30657 was exploited as a zero-day vulnerability in the wild last year.
Similarly, CVE-2021-30853 relied on an issue in the way the macOS checks applications on launch.
With this flaw, an attacker would be able to tinker with the scripted path on an application to cause Apple's security extensions to leave key variables set as "null." When those variables are set, checks on whether an application is authorized and safe to run do not get performed and, as a result, malware could potentially go unchecked.
In both cases, the bugs would require users to download and open the applications, so an attack would rely on social engineering to an extent, making the risk less severe. Still, given the relative lack of macOS malware threats in comparison to Windows and Linux, users may be more cavalier with running untrusted apps.
Both bugs were reported to Apple last year and have since been patched.
Wardle says that the two vulnerabilities show how the macOS could potentially come under fire from malware attacks not as the result of bugs in the code, but rather loopholes in the way the logic of the macOS has evolved over decades.
"MacOS still has pretty shallow protections," Wardle said. "Both of these were not found by complex fuzzing; the flaws were found inadvertently."
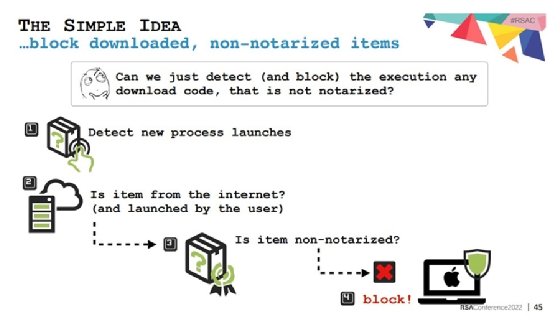
To protect against these types of script-based macOS malware, Wardle offered one simple bit of advice: Users should block any downloading of non-notarized code. Apple's notary service, which is an automated scan for malicious items and code-signing issues, allows developers to obtain a kind of stamp of approval of the software from Apple.
In addition, Wardle urged macOS users to enable automatic updates for the operating system and deploy an endpoint detection and respond product that is Mac-centric.