
Arsgera - Fotolia
DarkSide: The ransomware gang that took down a pipeline
DarkSide may be best known for the Colonial Pipeline ransomware attack, but the gang has hit dozens of organizations since last summer, presenting itself as a Robin Hood-type group.
After the U.S. Colonial oil pipeline was shut down following a ransomware attack, all eyes are on the cybercriminals who did it: a threat actor known as DarkSide.
The Colonial Pipeline ransomware attack occurred last Friday, and while no industrial control systems were compromised, multiple corporate systems were encrypted. Pipeline operations were then shut down as a precautionary measure and remain down as of this writing. The shutdown of the 5,500-mile pipeline, which is the largest of its kind in the U.S., has led to gas shortages in parts of the country -- particularly the southeastern and mid-Atlantic states.
DarkSide's first reported activity began last August, and the group's activity has generally increased in the months since. According to a new threat research blog by FireEye, the gang went from fewer than five victims per month to 20 as of April. Most victims are based in the U.S. and span across multiple business sectors.
DarkSide's ransoms, meanwhile, appear to range from hundreds of thousands to millions of dollars, and as TechTarget sister site LeMagIT pointed out, the ransomware has a high success rate.
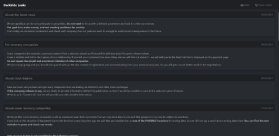
According to FireEye, DarkSide utilizes two popular fundraising techniques: ransomware as a service (RaaS) and the now-standard double-extortion model. With RaaS, DarkSide partners with other threat actors in order to deploy ransomware and sell access to victims; for the double-extortion model, the gang puts pressure on victims by both encrypting files and threatening to post stolen data on its leak site if the victim doesn't pay.
The leak site, "DarkSide Leaks," is accessible only via Tor as a .onion link. The site, which SearchSecurity accessed, includes a list of dozens of named victims -- each with their own page and gigabytes of stolen data.
The earliest post from October paints the gang as a Robin Hood-type figure, saying that the members "are targeting only large profitable organizations" and that "we think it's fair that some of the money they've paid will go to charity." They then list two charities to which they claim to have given $10,000 donations, and added, "Let's make this world a better place :)."
The most recent post, dated Monday, commented on the pipeline attack (grammatical errors left intact):
"We are apolitical, we do not participate in geopolitics, do not need to tie us with a defined government and look for other our motives. Our goal is to make money, and not creating problems for society. From today we introduce and moderation and check each company that our partners want to encrypt to avoid social consequences in the future," it read.
Though the exact origin of DarkSide isn't known, the FireEye blog makes multiple references to Russian affiliates, and a Sophos news post published Tuesday references an affiliate ad asking for Russian-speaking partners.
Emsisoft threat analyst Brett Callow told SearchSecurity that he saw a Russian origin as a possibility, albeit with a caveat.
"The devs may well be based in Russia or Eastern Europe," he said. "They have Russian speakers on their team, and the ransomware is specifically coded not to encrypt systems that use Russian or CIS languages. Such language checks or fairly commonplace in the ransomware world. The affiliates, however, could be anywhere and -- as we know from the arrest of a Canadian in connection with NetWalker attacks -- could be much, much closer to home."
The Sophos post, like the FireEye post, contains significant technical details as well as details about DarkSide. The vendor mentions that while the group has promised to stay away from certain types of organizations -- the leak site mentions funeral services, healthcare services, education, government and nonprofits -- the nature of being a ransomware gang with affiliates makes such claims questionable.
"The gang previously promised to spare healthcare organizations, as well as others involved in vaccine distribution, because of the negative attention such attacks could potentially bring from within the gang's home country," the article read. "Because of the way DarkSide operates, it's not clear how much control the keepers of the DarkSide brand have over the affiliates who do the actual work of breaking into networks and launching their ransomware."
Speaking generally about DarkSide, Callow appeared unimpressed with the gang overall.
"Besides some peculiar tactics, like making a couple of charitable donations, there's really nothing especially interesting or unusual about Darkside," Callow said. "They're vanilla cybercriminals with vanilla ransomware and got lucky in pulling off what's almost certainly the most high-profile ransomware attack of all time."
Alexander Culafi is a writer, journalist and podcaster based in Boston.






