
Getty Images/iStockphoto
How to deploy Windows LAPS for tighter security
Microsoft improved the feature that automates local administrator password management in Windows Server and the client OS. This tutorial explains the updates and how to set it up.
Local administrator passwords are challenging from a security standpoint, but an updated feature in Windows can reduce the worry associated with this administrative need.
Nearly every Windows device contains a local administrator account -- that's a basic security problem. These accounts are necessary for an admin to log in to the device to correct a problem connecting to AD. Organizations that want more security around these credentials can use the Windows Local Administrator Password Solution (LAPS), which automates password management of the local administrator account to keep the environment more secure. Microsoft updated this feature in April 2023 to make it a native part of the Windows OS. This article covers improvements made in Windows LAPS, methods to deploy it and considerations when migrating from the earlier LAPS version.
What is Windows LAPS?
Windows LAPS automatically manages and rotates the local administrator password on domain-joined Windows devices for Windows Server and the client OS. Microsoft developed the security measure to protect organizations from various attacks, such as pass the hash.
Local administrator password rotation is critical because, if an attacker accesses a nonmanaged local administrator password, they could use it to breach all domain-joined devices. Worse still, these passwords tend to be static, so an attacker could potentially use them to gain permanent access to an organization's resources.
Windows LAPS generates complex passwords for the local administrator account and rotates them on a schedule from seven to 365 days based on the configuration.
When admins need to access a device, they get the current password from AD or the cloud-based identity and access management platform Microsoft Entra ID, formerly known as Azure Active Directory. The admin then logs in as the local administrator. For added security, Windows LAPS can rotate the password automatically after use.
Since April 2024, Microsoft integrated Windows LAPS with the Windows OS.
What's new with Windows LAPS?
Microsoft has made significant enhancements to Windows LAPS in recent years. The company deprecated its earlier version -- the company refers to this as legacy Microsoft LAPS -- as of Windows 11 23H2 in favor of this update.
Here are some of the enhancements in Windows LAPS:
- Windows LAPS manages accounts automatically. Normally, Windows LAPS functions in manual mode. This enables the administrator to control all aspects of the local administrator account except for the password. When using automatic account management, Windows LAPS automates certain configuration details. Specifically, the account is made a member of the local administrators group, and the "password not required" and "password never expires" flags are disabled. The account description is also modified to indicate that Windows LAPS controls the account.
- Besides generating passwords, Windows LAPS can also create passphrases. Depending on the complexity setting, passphrases can consist of long words, short words or short words with unique prefixes.
- Microsoft introduced OS image rollback detection for Windows LAPS. If the admin reverted a system to a prior state by restoring a backup or applying a Hyper-V snapshot, that could lead to a password mismatch. Windows LAPS handles this problem by detecting the issue and forcing an immediate password rotation.
- Windows LAPS stores local administrator passwords in AD and Microsoft Entra ID. Legacy Microsoft LAPS only worked with AD.
- Windows LAPS protects against additional threats, including pass-the-hash attacks.
- Windows LAPS supports Azure's role-based access control.
- Windows LAPS supports the password encryption and password history.
- Windows LAPS automates the management and storage of passwords for the Directory Services Restore Mode account on the domain controller.
What are Windows LAPS limitations?
Windows LAPS and legacy Microsoft LAPS cannot manage the same account on the same machine. Microsoft recommends switching systems to Windows LAPS. However, there are some considerations:
- Because Windows LAPS has a learning curve, Microsoft offers a legacy Microsoft LAPS emulation mode to ease the transition period.
- Another option is to use both legacy Microsoft LAPS and Windows LAPS side by side until you are comfortable with the new version.
- If you decide to use both security features on the same machine, then you need to create an additional local administrator account on managed devices with a different name for use with the Windows LAPS policies.
What are Windows LAPS prerequisites?
Windows LAPS works on the following Windows OSes with the April 11, 2023, update or later installed:
- Windows 11 23H2.
- Windows 11 22H2.
- Windows 11 21H2.
- Windows 10.
- Windows Server 23H2.
- Windows Server 2022.
- Windows Server 2019.
Windows Server 2025, released in November 2024, also supports Windows LAPS.
Microsoft includes Windows LAPS as part of the Windows OS -- added through Windows Update -- rather than requiring a separate download.
Key differences between Windows LAPS and legacy Microsoft LAPS
There are several key differences between Windows LAPS and legacy Microsoft LAPS, including the following:
- Windows LAPS is built into Windows 11, starting with 22H2, and Windows Server 2022 with updates and newer versions of Windows.
- Windows LAPS supports Microsoft Entra ID and AD. Legacy Microsoft LAPS only worked with AD.
- Legacy Microsoft LAPS was a standalone tool and required standalone Group Policy settings.
- Although legacy Microsoft LAPS is still supported, Microsoft has deprecated it. Microsoft recommends adopting Windows LAPS, regardless of infrastructure arrangement.
How to migrate from legacy Microsoft LAPS
Before you can migrate from legacy Microsoft LAPS, some prep work is necessary. You start by identifying the machines using the legacy version and then verifying they run an OS that is compatible with Windows LAPS. It's also a good idea to ensure those systems have the latest patches.
Next, prepare the AD infrastructure. You must update the schema -- the definition of the structure of the database -- because Windows LAPS adds new attributes to AD. Back up the AD environment, and then extend the schema using the Update-LapsADSchema cmdlet. You might need to apply some permissions using the Set-LapsADComputerSelfPermission cmdlet, which gives the computer account the ability to update Windows LAPS password attributes and also enables password rotation.
Next, decide if you want to allow coexistence between legacy Microsoft LAPS and Windows LAPS or if you want to perform a cutover migration. At a minimum, you must enable and configure the Windows LAPS Group Policy settings. If you disable legacy Microsoft LAPS, then you must set the legacy Microsoft LAPS Group Policy settings to "not configured." Only do this after you have verified Windows LAPS is working.
Next, verify that passwords are being stored correctly with the following PowerShell command.
Get-LapsADPassword -Identity <ComputerName>Next, delete the machine's local administrator password and expiration data in AD with the following command.
Set-ADComputer -Identity "ComputerName" -Clear "ms-Mcs-AdmPwd","ms-Mcs-AdmPwdExpirationTime"To remove these attributes from multiple machines in an organizational unit (OU), adapt the following PowerShell command to your infrastructure.
Get-ADComputer -Filter * -SearchBase "OU=Computers,DC=domain,DC=com" | Set-ADComputer -Clear "ms-Mcs-AdmPwd","ms-Mcs-AdmPwdExpirationTime"How to deploy Windows LAPS
There are two options to deploy Windows LAPS. The first is to use Intune to create a LAPS policy that admins push to managed Windows devices.
The other option is to push LAPS settings to managed devices using Group Policy, which is only appropriate when managing domain-joined Windows devices.
How to create the Intune policy for Windows LAPS
From the Microsoft Intune admin center, go to the Endpoint security tab to create the policy for Windows LAPS.
Click on Account protection and then the Create Policy link.
The interface displays a prompt to choose a platform and a profile.
Set the platform to Windows and the profile to Local Admin Password Solution (Windows LAPS).
Click Create.
When prompted, give the profile a name.
Click Next to move to the Configuration settings screen.
Specify the desired backup directory, password length and complexity requirements, and other relevant settings.
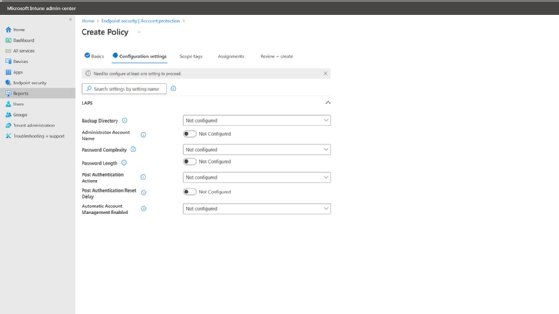
Click Next to advance to the Scope Tags tab.
Select a custom scope tag -- if one exists -- or the default one.
Click Next to open the Assignments tab.
Select the group to which you want to apply the policy.
Set the Target Type to Include or Exclude, depending on whether you want the group included in the policy.
Click Next to advance to the Review + Create screen.
Take a moment to review the settings shown on this screen. If everything looks good, click the Create button to build the policy.
How to set up Group Policy for Windows LAPS
You can use Group Policy settings to push Windows LAPS settings to domain-joined devices, but you must first prepare AD by extending the schema to support Windows LAPS and provide the necessary permissions.
It's a good idea to back up AD to roll back the changes if necessary.
Next, open an elevated PowerShell session on your domain controller, and then enter the following command to update the AD schema.
Update-LapsADSchema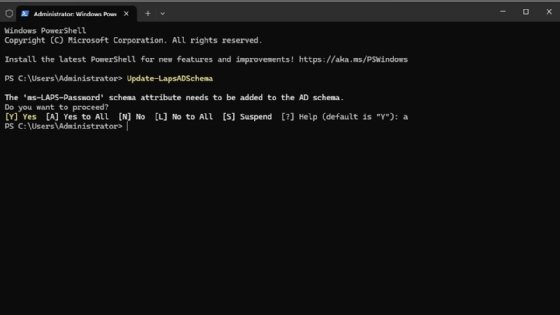
If an error about the command not being recognized appears, check that the server has all available updates, and confirm its role as a domain controller.
Next, configure Windows LAPS.
Grant the domain-joined computers permission to use Windows LAPS. The easiest way is to grant permission to the Computers container in AD. The command syntax varies depending on your AD structure. In the case of a single domain forest with the name poseylab.com, the PowerShell command is the following.
Set-LapsADComputerSelfPermission -Identity "CN=Computers,DC=poseylab,DC=com"Use Group Policy Management Editor to find the LAPS-related Group Policy settings in the Computer Configuration > Policies > Administrative Templates > System > LAPS section.
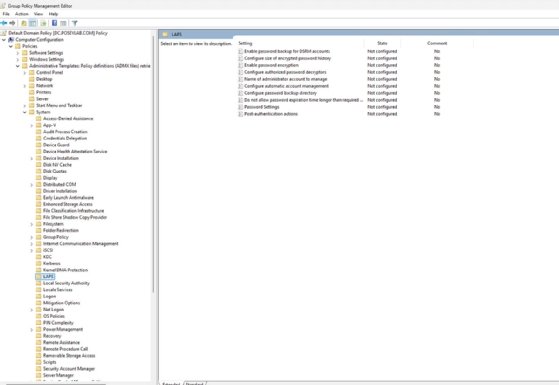
Configure the policy settings to meet your organization's needs.
Passwords for local administrator accounts are not going away, so the updated Windows LAPS is Microsoft's attempt to make the best of the situation. This automated process is an improvement on the legacy Microsoft LAPS system, so it is worthwhile to see if it works for your organization.
Brien Posey is a former 22-time Microsoft MVP and a commercial astronaut candidate. In his more than 30 years in IT, he has served as a lead network engineer for the U.S. Department of Defense and a network administrator for some of the largest insurance companies in America.









