
Query event logs with PowerShell to find malicious activity
Every action on a Windows Server system gets recorded, so don't get caught by an avoidable security incident. Learn how to find potential security problems in event logs.
Suspicious activity in your Windows environment should not be a surprise when reports of questionable incidents are available right at your fingertips.
PowerShell is an excellent tool for scripting almost any process within Windows Server. Microsoft's server OS fully supports PowerShell both locally and remotely for everything from configuration to retrieving the event viewer logs. You can also learn to filter the logs with PowerShell to separate potentially problematic events from standard logged actions.
Anatomy of the Windows event log
The Windows event viewer consists of three core logs named application, security and system. Each log stores specific entry types to make it easy to identify the entries quickly. For example, if you need to review security failures when logging into Windows, you would first check the security log. You can also access the application or feature-specific logs within the event viewer for different workloads, such as Active Directory Federated Services (ADFS).
The event logs store many events, from standard information to critical issues and problems. Many of the entries within the event logs are for information only; however, when an application such as on-premises SharePoint Server fails, multiple events are recorded to both the application and system logs for the administrator to investigate.
Understanding the difference between regular logged entries and unknown or even malicious log entries is an essential task. If we monitor the event logs correctly, we can identify the entry types and separate the two types.
What are regular logged entries?
Regular logged entries could be anything that happens within either an application, the operating system or external action that communicates with the server. For example, standard entries found in the security log relate to the authentication of accounts directly onto the server.
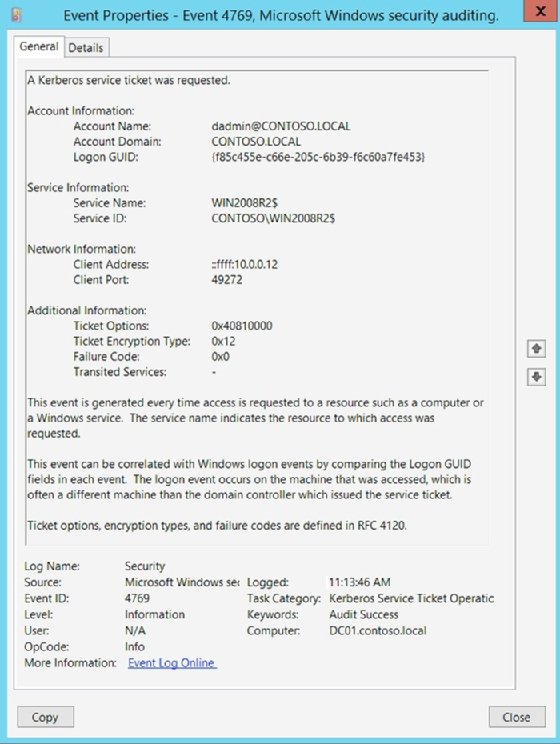
The security log records critical user actions such as account management, logons, logoffs and object access. Logging these events helps detect potential security problems and provide evidence for further investigation.
What are unknown or malicious logged entries?
Most entries within the event logs are not critical. However, specific actions could hint at a potential security breach or malicious activity. For example, an entry for an end-user account that has been added to a sensitive security group or many failed logon attempts are suspicious and should be explored. Another entry type labeled as unknown in the event log can be difficult to fully understand without scrutiny.
The event log entries provide an XML definition of information captured and used to create the event. Within the XML, you can diagnose why a specific action was logged. The XML contains more information not shown within the regular details from the standard user interface.
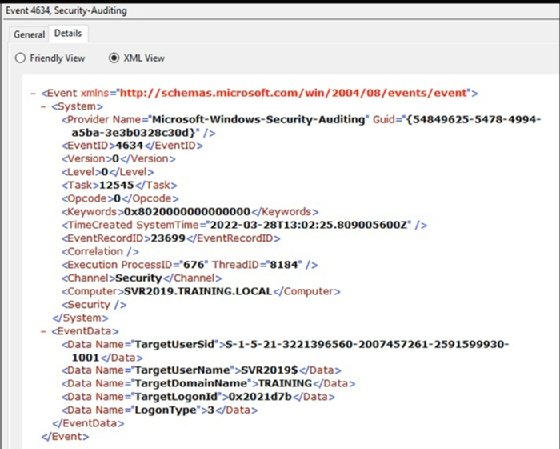
Records of malicious entries performed directly or remotely on the targeted machine contain information related to several actions: permission elevation, removal or deletion of specific information, repetition of the same action, sustained activity for an extended period or execution of an unusual task.
A sign of malicious activity is an event ID that doesn't match the event or explain what is happening. For example, an event ID of 4104 relates to a PowerShell execution, which might not appear suspicious. If you look at the details for the event, you can see the PowerShell code to determine its intent.
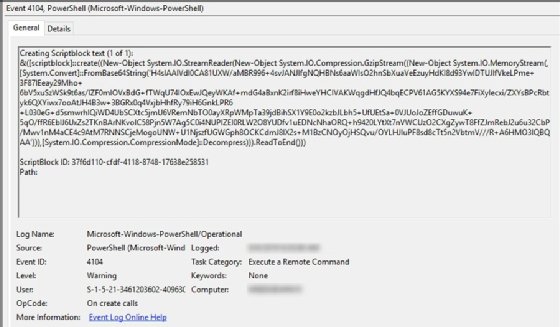
The screenshot shows the script attempts to download other malicious PowerShell code to perform a phishing attack.
Query event logs to find malicious log entries
To help with investigations, we will use PowerShell to retrieve log entries and filter them. You collect malicious logged entries the same way as any other entries, though the filtering might differ. To understand what actions to fetch, you need to know the standard event IDs to monitor.
You also need to categorize event IDs by their type to make it easier to understand what to retrieve and, if required, hunt for during an analysis. The following four categories cover most event ID types worth checking, but you can expand this list as needed.
- Services. This event type covers installation of services, termination of services and starting and stopping services.
- Scheduled tasks. This event type refers to adding, removing, updating and deleting scheduled tasks.
- Account management. This entails creating new accounts, enabling existing accounts, password resets and group membership changes.
- Event log manipulation. This includes clearing of any event log, with a preference for the security audit log.
Some example event IDs for each category are:
- Services
- 4697: A service was installed in the system.
- 7034: The service terminated unexpectedly.
- 7045: A new service was created on the local Windows machine.
- Scheduled tasks
- 106: The user registered a new scheduled task.
- 4702: A scheduled task was updated.
- 4699: A scheduled task was deleted.
- Account management
- 4720: A user account was created.
- 4724: An attempt was made to reset an account password.
- 4782: Password hash access.
- Event log manipulation
- 1100: Event log service shutdown.
- 104: Log file cleared.
- 1102: Security audit log cleared.
Depending on the server workload, you could add many more event IDs. For example, Microsoft provides a list of nearly 400 event IDs to monitor in Active Directory. For the purposes of this tutorial, the goal is to target specific event IDs related to malicious actions.
The first PowerShell code example below filters the event log entries using specific event IDs. In this example, event ID 4104 refers to the execution of a remote command using PowerShell.
The second PowerShell example queries an exported event log for the phrase "PowerShell."
# Retrieve Potentially Malicious PowerShell Event Log Entries using Event ID
$id = "4104"
$events = Get-WinEvent -FilterHashtable @{ Path='C:\Users\Administrator\Downloads\pwsh.evtx'; Id=$id }
$events | Select ID, Message
# Query Event Log Entries to Retrieve Malicious PowerShell Commands
$events = Get-WinEvent -Path 'C:\Users\Administrator\Downloads\pwsh.evtx' | Where-Object {$_.Message -like '*PowerShell*'}
$events | Select ID, Message
These are simple commands that retrieve specific entries that might be malicious because they involve PowerShell. You can customize the filter for other keywords such as ScriptBlock, Mimikatz and Python.exe or a PowerShell function name such as Invoke-Expression.
It is more critical than ever to monitor event logs for potentially malicious activities to help you mitigate issues and be more proactive with security.







