Organizations of all sizes recognize the risk of cybersecurity threats to their businesses. This is why recent Technology Spending Intentions research from TechTarget’s Enterprise Strategy Group (ESG) [1] highlights that organizations continue to invest in improving cybersecurity. Respondents’ most-cited business initiative driving IT spending at their organizations in 2023 and the most-cited area in which they expect to increase investment in 2023 is cybersecurity. Why is that needed? Because the threat landscape is always changing and evolving. Like a never-ending game of whack-a-mole, cybersecurity professionals must adapt to new threats and tactics.
Over the last few years, the amount of encrypted traffic on the network has expanded significantly. While this is important to ensure privacy and security, it can represent a blind spot for security tools. ESG research [2] highlights that 83% of organizations have either a notable or significant concern regarding scanning encrypted traffic for threats. In fact, 68% of ESG research respondents have reported being impacted by multiple encrypted attacks.
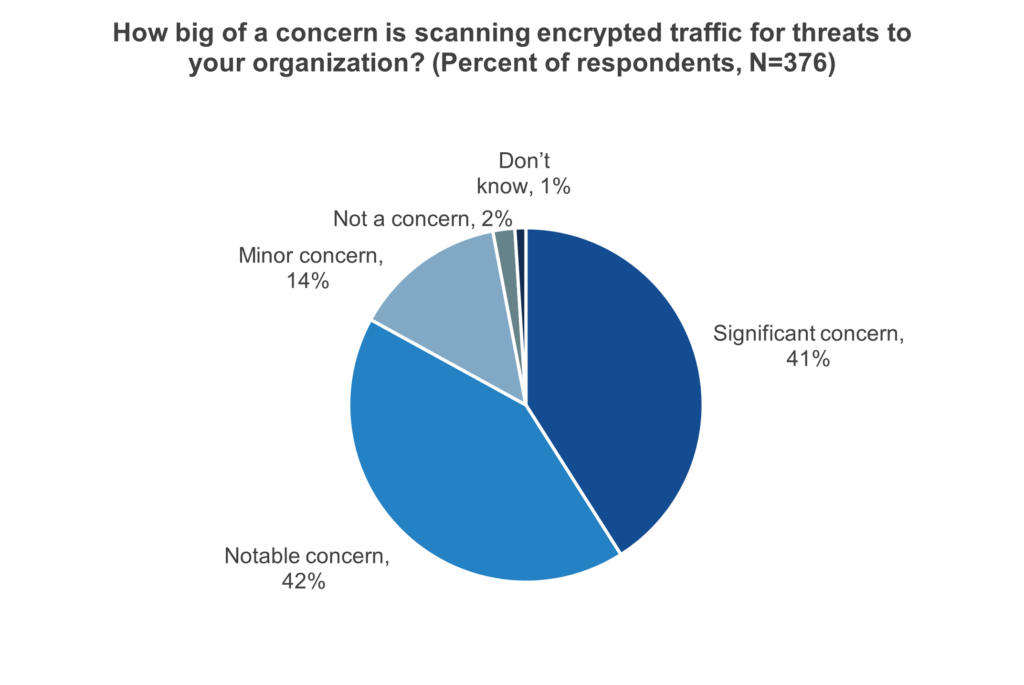
Why is this happening? Well, because most organizations lack visibility into all their encrypted traffic, with only 34% stating that they have complete visibility. There are a number of reasons organizations forgo decryption, some of the most common of which include:
- Selective decryption to avoid looking at sensitive employee information (56%).
- Performance issues with decryption (47%).
- Too expensive to decrypt all traffic (32%).
- Don’t have a lot of encrypted traffic (32%).
It will only get harder to gain visibility into encrypted traffic as new versions of Transport Layer Security (TLS 1.3 -TCP) and QUIC (UDP) rolls out. As these standards are adopted, it will become increasingly difficult to decrypt and analyze traffic.
So where does that leave organizations that are trying to stay ahead of the cyber threat curve? Well, one company that we just spoke to believes they have a solution. Gigamon, a pioneer in network visibility and intelligence that now focuses on providing deep observability pipelines, announced Precryption technology. This enables organizations to have deep visibility into encrypted traffic across virtual machines or container workloads so it can be delivered to threat detection, investigation and response tools for hybrid cloud environments. Gigamon believes this technology will eliminate blind spots and ensure organizations can inspect all encrypted traffic.
It accomplishes this by utilizing eBPF technology within the Linux kernel to capture traffic prior to encryption or just after decryption – eliminating the need for costly decryption technology or having to sniff keys. Gigamon claims that it runs independently of the application, unlike approaches that require agents. By collecting traffic prior to encryption, this approach alleviates the need to manage keys on a separate decryption tool, as well as the performance impact from decrypting network traffic.
Clearly, organizations have to work really hard to stay ahead of an ever-changing threat landscape, so It’s great to see vendors like Gigamon bringing to the market innovative solutions that deliver full visibility into encrypted traffic.
[1] Source: Enterprise Strategy Group Research Report, 2023 Technology Spending Intentions Survey, November 2022.
[2] Source: Enterprise Strategy Group Complete Survey Results, Network Threat Detection Response Trends, April 2023.







