Generative AI (GenAI) use is on the strategic charter of business lines across organizations and industries. Recent research by TechTarget’s Enterprise Strategy Group found that the space of business intelligence (BI) is no different, with decision-makers planning for robust GenAI usage that promises to boost engagement in analytics tools that supply crucial business insights.
Insight
-
-
My role as research analyst involves a lot thinking about and studying what matters most to networking professionals, and how the changing technology and business landscape affects them. This regularly includes direct research and dialogue with practitioners to investigate what is causing the greatest challenges day to day, and how they are coping.
One of the most exciting parts of research is finding best practices that can be shared with the networking community to help everyone. Such was the case with a recent project I had the pleasure of supporting, when TechTarget’s Enterprise Strategy Group conducted the research and analysis process for the “2024/25 State of the Network Study” on behalf of Viavi Solutions. If you’d like to get into the specifics, you can check out the full study results, but following here are a few of what I found to be the most compelling insights.
First, the study examined the growing trend of using observability for monitoring and operating IT infrastructures. Applying observability principles to network monitoring, also known as network observability, turns out to be pretty valuable. Organizations that adopted a comprehensive observability strategy, rather than an ad hoc approach within each functional area, were surprised by the benefits. For instance, the number of participants who saw a significant drop in mean time to detect incidents over the past 12 months was 3.5 times higher for those who adopted observability as a strategic initiative. There was also widespread recognition that adopting observability as a strategy improved collaboration between network and security teams, improved compliance, and even accelerated product development cycles.
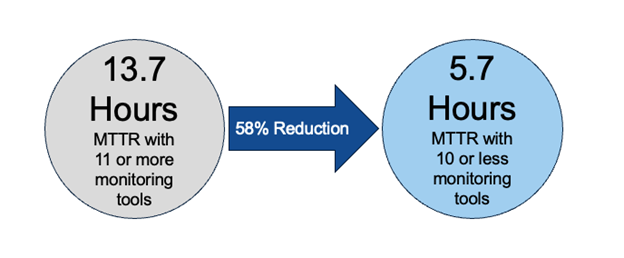
One of the bigger challenges for teams implementing an observability strategy is managing an often-bloated monitoring tools stack. Study participants reported using an average of 10 tools for various aspects of network monitoring, with some using over 20. Consolidation is essential, and there was nearly universal consensus (93% affirmative) of participants intending to reduce tool counts. We found compelling evidence of consolidation’s positive impact. For those shops using more than 10 tools, the average reported mean time to repair (MTTR) was 13.7 hours, while those using 10 or fewer reported an average MTTR of 5.7 hours—a 58% reduction. The takeaway is that fewer tools means lower MTTR, so go forth and consolidate whenever and wherever you can.

The study also explored how teams were dealing with hybrid environments. While cloud service providers and cloud-focused architects and engineers bear the primary responsibility for monitoring and managing application performance in the cloud, networking teams are also involved, even if they aren’t taking point—their perspective remains highly valuable. Nearly everyone (97%) agreed that for cloud environments, packet capture remains important, and over three-quarters valued flow-level data such as NetFlow, sFlow, IPFIX, and various flow logs. The bottom line here is that traditional network monitoring techniques still make sense in cloud and hybrid environments.
Finally, we checked in on the ongoing close relationship between networking and security. As cybersecurity threats continue to grow, collaboration between networking and security teams becomes increasingly important. As it turns out, observability helps drive this too. We found that teams embracing observability as a strategy were 15%-35% more active across various types of NetOps/SecOps collaboration, including improved collaborative workflows, tools alignment, goals alignment, collaboration frequency, and creating hybrid roles. This need for collaboration, along with the benefits of observability, is laying the groundwork for advanced security practices, such as continuous threat exposure management (CTEM). CTEM emerged as one of the top methods for addressing threat exposure among study participants’ organizations—particularly for dynamic and complex infrastructures, such as hybrid cloud.
The key takeaway here is that observability strategies are worth the effort. They benefit everything from networking engineering and operations to network-security collaboration through a range of improved viewpoints and outcomes. Teams should continue consolidating tools and applying traditional monitoring approaches across their hybrid environments, while embracing observability across the board. The payoff? Better efficiency, less downtime, and a stronger security posture.
-
Organizations continue to rely on identities that are susceptible to compromise, abuse, misuse, and theft. Risk is compounded by over-permissive, static access rights that provide little to no visibility into access trends or, most importantly, who is accessing what and how they are doing so. Unfortunately, organizations have been slow to pivot their security programs to an approach that incorporates identities as a foundational aspect of their cybersecurity strategy. TechTarget’s Enterprise Strategy Group recently surveyed IT, cybersecurity, and application development professionals responsible for or involved with identity security technologies and processes to gain insights into these trends.
To learn more about these trends, download the free infographic, The State of Identity Security.
-
Organizations continue to rely on identities that are susceptible to compromise, abuse, misuse, and theft. Risk is compounded by over-permissive, static access rights that provide little to no visibility into access trends or, most importantly, who is accessing what and how they are doing so.
Despite the transformation to a dynamic, amorphous perimeter, a multitude of identity security solutions and managed identity services exist. Unfortunately, organizations have been slow to pivot their security programs to an approach that incorporates identities as a foundational aspect of their cybersecurity strategy.
However, CISOs and security professionals are beginning to understand the importance of securing identities. With a decade of evidence on the risks and a plethora of identity security solutions, identity is shifting from the domain of IT operations into cybersecurity.
To gain further insight into these trends, TechTarget’s Enterprise Strategy Group surveyed 372 IT, cybersecurity, and application development professionals at organizations in North America (US and Canada) responsible for or involved with identity security technologies and processes.
Already an Enterprise Strategy Group client? Log in to read the full report.
If you are not yet a Subscription Client but would like to learn more about accessing this report, please contact us.
-
Companies considering cloud-based contact center technologies must identify which options will best unify customer and agent experiences across live and asynchronous customer channels. At the same time, organizations need to integrate contact center-as-a-service (CCaaS) and unified communication-as-a-service (UCaaS) platforms so agents can access internal experts to help resolve customer issues. Furthermore, busy agents need AI tools to quickly search knowledgebases to provide the best service and meet quality KPIs. TechTarget’s Enterprise Strategy Group recently surveyed IT and business professionals responsible for or involved with contact center technology and processes to gain insights into these trends.
To learn more about these trends, download the free infographic, The Impact of Evolving Work Environments on Contact Center Platform Requirements.
-
Artificial intelligence and machine learning (ML) are topics frequently discussed in various contexts today, primarily regarding their impact on society and application in specific scenarios. When it comes to backup and recovery, two questions are significant: How much AI-generated data needs protection? How will backup and recovery processes adapt to take advantage of these rapidly evolving technologies? TechTarget’s Enterprise Strategy Group recently surveyed IT and data professionals familiar with and/or responsible for data protection and data science for their organization to gain insights into these trends.
To learn more about these trends, download the free infographic, Reinventing Backup and Recovery With AI and ML.
-
My TechTarget Enterprise Strategy Group colleague Jon Brown and I are collaborating on research around the concept of data resilience. This study will delve into the intersection of data security posture management, data protection, data security, and data governance. While the results will be published in the coming months, I wanted to share the core research hypothesis as we anticipate results from the field.
Sensitive Data Grows
Enterprise data stores including personal identifiable information (PII) or other sensitive data are growing significantly. Data volumes generally are rapidly growing, and cybersecurity teams struggle to identify, categorize, and secure sensitive data repositories and data flows across clouds and geographies. The research will provide some granularity around the volume of data generally and PII/sensitive data specifically, as well as where that data is located.
Tools “Fit for Purpose” vs. Platform
There is a decades-long cybersecurity industry argument about “point products vs. platform.” I’m generally of the “it is a both” camp rather than either/or for reasons that go beyond the space constraints of this blog. When it comes to the various tools involved in data resilience, such as data security posture management, data security, backup, and governance, I expect that most enterprises today are taking a“best tool for purpose” approach for the various elements of data resiliencemore thana consolidated platform approach.
Enterprise Strategy Group has done other research in various cybersecurity domains around the “point product vs. platform” dynamic, including this year’s The State of Identity Security study that showed an even split between those who wanted the best tool for identity security and those who preferred a platform approach. There is considerable value to security practitioners in a consolidated identity platform that brings together functionality like identity governance and administration along with privileged access management. Data resilience is an emerging space compared to the more mature identity and access management space, so the market dynamics will be different.
Data resilience, a subset of cyber resilience, is a relatively new focus for the enterprise driven by high-profile ransomware compromises, and there is a wave of new technology trying to solve this problem—hello, DSPM and cloud data protection players. While security and IT teams want to prune their portfolio of tools for various reasons—the platform approach—organizations are seeing the importance of “fit for purpose” tools that satisfy their new needs for data security and resilience, compared to broader platforms that might or might not provide robust data resilience features and capabilities.
Locating and categorizing data, both on premises and in the cloud, in a dynamic data environment with new apps such as generative AI and “shadow data” outside the purview of IT is a relatively new problem for IT and security teams with differentiated technology approaches from various vendors.
I expect the research to show a significant preference today for “best tool for the purpose” compared to the platform approach for the various elements that comprise data resilience. This will change over time as the enterprise needs evolve, technology evolves, and vendor capabilities/differentiation ebbs and flows.
DSPM Adoption Ramping
Organizations are embracing DSPM and will movein pilot/proof of concept or plan to deploy in the near term. This is a space that is primed for growth with key drivers, includingpreventing potential data breaches and facilitating deployment of generative AI. While past research has shown increasing investments in data security generally—DSPM was a top 10 priority in the Enterprise Strategy Group “2024 Technology Spending Intentions Survey”—I expect this research to provide granular details around that ramp.
Noise vs. Substance
While there are many opinions and hypotheses surrounding the state of DSPM, some of that is noise is driven by a lack of data or talking to “friendlies” who might not represent the broader market. Given how much flux and innovation is out there, it’s exciting to conduct this rigorous Enterprise Strategy Group research to shed light on DSPM and adjacent solution areas. The above hypothesis highlights explain what we’re expecting to see—and I’m looking forward to seeing the insight nuggets illuminating where enterprise IT and security teams are focusing their data resilience efforts, who is involved, and what the business drivers are. If you are in the DSPM space and interested in understanding the research, give me a shout to discuss.
-
Artificial intelligence (AI) is transforming the world of backup and recovery, bringing new opportunities and challenges for organizations that want to protect and leverage their data assets for business value. AI can help automate backup and recovery processes, improve data security and resilience, enable data reuse and insights, and optimize costs and performance. However, AI also poses new risks and concerns, including data privacy and compliance, data management and integration, ransomware attacks, and staff skill gaps.
To understand how organizations are adopting AI and machine learning in their backup and recovery strategies, TechTarget’s Enterprise Strategy Group surveyed 375 IT and data professionals familiar with and/or responsible for data protection and data science decisions for their organization.
Already an Enterprise Strategy Group client? Log in to read the full report.
If you are not yet a Subscription Client but would like to learn more about accessing this report, please contact us.
-
This Complete Survey Results presentation focuses on active archive adoption, storage platforms and locations, preferred disk types, data retention, access frequency, retrieval times, strategy elements, use cases, deployment drivers, the role of active archives in AI/machine learning (ML) initiatives, and the distribution of data used in AI/ML initiatives.
Already an Enterprise Strategy Group client? Log in to read the full report.
If you are not yet a Subscription Client but would like to learn more about accessing this report, please contact us.
-
This Complete Survey Results presentation focuses on data user trends, data classification and lineage, drivers behind data governance strategies, challenges with data governance adoption, the impact of AI on data governance, the importance of data governance elements, and investment plans.
Already an Enterprise Strategy Group client? Log in to read the full report.
If you are not yet a Subscription Client but would like to learn more about accessing this report, please contact us.
-
This Complete Survey Results presentation focuses on responsible AI maturity, prioritization, best practices, terms, outcomes, challenges, responses to issues, bias mitigation, measurements, acceptable fairness levels, data and analytics impact, and stakeholders.
Already an Enterprise Strategy Group client? Log in to read the full report.
If you are not yet a Subscription Client but would like to learn more about accessing this report, please contact us.
-
This Complete Survey Results presentation focuses on the experiences of cybersecurity professionals, including performance assessments of their cybersecurity leaders and their suggestions for what organizations can do to help cybersecurity professionals succeed.
Already an Enterprise Strategy Group client? Log in to read the full report.
If you are not yet a Subscription Client but would like to learn more about accessing this report, please contact us.