
momius - stock.adobe.com
Email enigma: Why is Canada hit with so many phishing attacks?
Canada has become an increasingly popular target for phishing attacks, according to several security vendors, but the reasons for the increase remain a mystery.
While multiple reports show Canada is increasingly targeted in phishing attacks, experts aren't sure what's behind the increase.
According to the "RSA Quarterly Fraud Report: Q1 2020," 66% of all phishing attacks observed during that time period were directed at users in Canada. It was the second quarter in a row that Canada was targeted by two-thirds of phishing activity, and the fifth quarter in a row where the country was by far the most popular target.
In a "Canadian Internet Registration Authority" survey, which surveyed 1,985 Canadians who owned a ".ca" domain between November 2017 and January 2018, including personal and business websites, 85% received a phishing email. In 2019, PhishLabs published its top most targeted countries for phishing attacks, which found that Canada saw a substantial rise in phishing volume starting from April 2018, pushing it into second place overall. In addition, a 2020 threat intel report by Check Point Software Technologies determined that 96% of attacks on Canadian users were email-based, which was well above the global average.
Despite the data, it's unclear why Canada has become such a popular target for phishing attacks. On one hand, it's typical for threat actors to target users in developed nations with high levels of internet connectivity and technology usage.
"Canada is an attractive target for cybercriminals due to a variety of reasons, including finance, natural resources, digital technology and telecommunications," a spokesperson for the Canadian Centre for Cyber Security said in an email to SearchSecurity.
Lotem Finkelsteen, Check Point threat intelligence group manager, said threat actors are known to follow the money, and Canada has a good economy with thriving businesses.
But that doesn't explain why Canada, with a population of under 40 million people, has received such a higher volume of phishing emails compared to other developed nations. According to RSA's research, the U.S. was second on the list of most targeted nations with just 7% of phishing attacks during the quarter. Threat researchers have several theories as to why Canada appears to be so heavily phished, but none of the theories have been confirmed, and even RSA itself hasn't offered a definitive explanation for the abnormally high activity.
The theories
A notable theory revolves around massive phishing campaigns that target interconnected Canadian banks, which would inflate the numbers. Daniel Cohen, RSA's head of anti-fraud products, said many of the phishing attacks on Canada target Interac, a payment service provider that is used by the majority of Canadian financial institutions. With a single campaign focused on Interac, he said, cybercriminals can potentially affect numerous banks in the country.
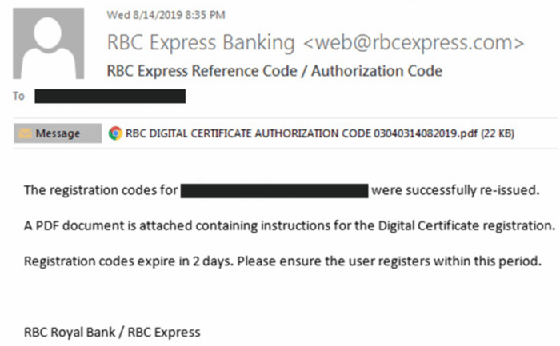
Threat researchers have in the past observed major phishing campaigns that target Interac. In 2019, Check Point detected the new phishing campaign that impersonated the Royal Bank of Canada. The attack sent legitimate-looking emails containing a PDF attachment to multiple organizations and victims from Canada. Check Point tracked more than 300 look-alike domains that hosted phishing websites for 14 banks that use Interac.
Another theory is that much of the phishing activity is being generated within Canada. For example, Finkelsteen said Check Point believes that threat actors behind the 2019 campaign were actually from Canada.
"The threat actor (or actors) really knew the market in Canada -- knew what banking services were available -- from credit cards to loans. They were familiar with the day-to-day business life in Canada and by understanding this, they were able to target companies in there and then always change the phishing pages by changing the logo or icon," Finkelsteen said via email. "They quickly adapted and changed their webpage. Because of this, we had a long list of phishing websites and different pages each time."
Check Point said the trend of more phishing attacks originating in Canada was first observed by its research team in 2019, and the trend has continued this year.
"We see that threat actors attacking Canada are actually Canadians, which is very unusual. Once you have threat actors that are working within the country, you're obviously more vulnerable to phishing attacks. In Canada, they speak French and English and have their own words and terminology, so someone is familiar with the day to day there," Finkelsteen said.
Overall, more phishing attacks occur in English because it's more commonly used in the business world.
"Globally, we see its 80%, but for Canada it's 96% of attacks that are email-based. That goes back the last six months," Finkelsteen said. "One out of every five attacks originated in Canada."
PhishLabs has also seen a rise in attacks coming from Canada; last year the vendor saw a 170% increase in phishing activity in the country. But RSA's Q1 report showed nearly 60% of phishing attacks originated in the U.S., while Canada was seventh on the list of hosting countries.
There's also a theory that the data might be off. While PhishLabs' research last year showed Canada was second on the list of most-phished countries, the U.S. was the overwhelming leader with 84% of targets. PhishLabs said their observations were inconsistent with RSA's findings.
"We suspect it is due to the particular way they measure attack volume," a spokesperson for PhishLabs said in an email to SearchSecurity. "While we do not know the exact details, we suspect RSA's data as it pertains to Canada is inflated due to counting each brand involved in a multibrand phishing attack as individual attacks. This would have a major impact on volume."
Phishing flood
Another theory suggested cybercriminals have seen a higher success rate targeting Canadian users and, as a result, have focused more of their efforts on the country. Daniel Tobok, CEO of Canada-based incident response company Cytelligence, has observed a rapid increase in phishing attacks over the last five years.
"It's been a very big problem in Canada," Tobok said. "Phishing has become quite a tool for cybercriminals. It accounts for 76% of all attacks that lead to ransomware today. People have realized they can put up firewalls and other protections to keep the bad guys away, but they are still vulnerable to click on links, and click on emails."
The pandemic-fueled remote workforce has increased these attacks, Tobok said, because users are no longer protected.
"With outdated passwords on firmware or routers -- we gave the bad guys an early Christmas," Tobok said. "In general, I do think we're more easygoing in Canada and gullible and less suspecting."
On average, Cytelligence handles 100 investigations a month in Canada and the U.S. When it comes to phishing attacks, Tobok said it's a 60/40 split in favor of Canada. However, much of that may be attributed to the bigger population and number of companies in the U.S.
"Criminals and other malicious cyberthreat actors -- many of which operate outside of Canada's borders -- take advantage of security gaps, low cybersecurity awareness, and technological developments in an effort to compromise cyber systems," a spokesperson for the Canadian Centre for Cyber Security said in an email to SearchSecurity.
Tobok said Canadian companies, as well as multinational corporations with a presence in the country, should devote more time and energy into educating users. "What we see is that they have an increased profile and an increase in threats," he said.
Threat actors often try to take advantage of a lack of communication between regional offices, as well as the lack of familiarity between employees, and exploit users' patience and tolerance, he said. Security awareness training can help employees detect, for example, a fraudulent corporate request for data or funds.
"Email security [technology] is important, but awareness training is critical," Tobok said. "You need to be a little paranoid and cautious and really question some of the emails."







