
Winnti threat group rides again with IP theft campaign
A Chinese cyberespionage campaign, dubbed 'Operation CuckooBees' by Cybereason, went unnoticed for years as spies siphoned off intellectual property from companies.
A notorious Chinese hacking outfit has managed to one-up itself with a years-long cyberespionage hacking campaign that stole massive amounts of corporate data and intellectual property.
Referred to as "Operation CuckooBees" by Cybereason, the campaign ran from 2019 to 2021 and targeted technology and manufacturing companies in Asia, North America and Europe with the intent of lifting intellectual property and corporate secrets. According to a new two-part report from the threat detection vendor, the campaign was the work of Winnti, a Chinese state-sponsored advanced persistent threat (APT) group that has been active since 2010.
The Winnti group, also known as APT41, was able to hide itself for years inside a corporate network and steal a massive cache of valuable data from the target. Cybereason said the attack was noteworthy for its longevity and the amount of data collected on not only the target, but its partners and clients.
"With years to surreptitiously conduct reconnaissance and identify valuable data, it is estimated that the group managed to exfiltrate hundreds of gigabytes of information," Cybereason said in a blog post published Wednesday. "The attackers targeted intellectual property developed by the victims, including sensitive documents, blueprints, diagrams, formulas, and manufacturing-related proprietary data."
The Cybereason researchers noted that the attack was particularly nefarious in that it managed to incorporate a mixture of both zero-day vulnerabilities and known bugs that enterprises simply had not patched.
Targeting an unnamed ERP platform, the attackers infiltrated internet-facing systems using not only newly discovered exploits, but also web shell vulnerabilities that have been public info as far back as 2006.
"Winnti leveraged both known and previously undocumented malware techniques, including digitally signed kernel-level rootkits," Cybereason said. "The threat employed an elaborate, multi-stage infection chain that was critical to enabling the group to remain undetected for so long."
Once inside the network, the Winnti hackers focused on establishing persistent connections that would allow them to tap into systems even if their initial malware had been discovered, Cybereason found.
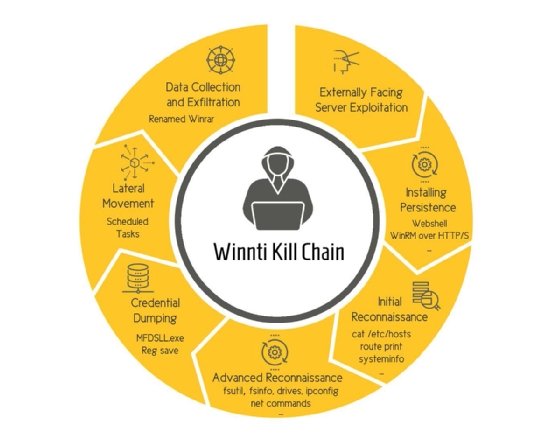
The hackers used Windows Remote Management software to allow for remote shell connections, and deployed rootkit malware that would allow them to access machines below the level of the OS and most antimalware toolkits.
From there, the Winnti hackers made use of built-in Windows commands to gather everything from network configuration details to account credentials. They then used a complex series of steps to exfiltrate the pilfered data through multiple applications and proxies.
"The malware authors chose to break the infection chain into multiple interdependent phases, where each phase relies on the previous one in order to execute correctly," Cybereason explained. "This demonstrates the thought and effort that was put into both the malware and operational security considerations, making it almost impossible to analyze unless all pieces of the puzzle are assembled in the correct order."
The researchers concluded that the sheer amount of effort and technical complexity that went into the Winnti attack shows just how highly the Chinese government values intellectual property and its value as both a private and government asset.
"Data is the currency of business today, and the line between cyber espionage and nation-state espionage has blurred," Cybereason said. "There are a variety of ways that stolen data might be used that could have significant consequences. Suffice it to say that losing gigabytes of sensitive and proprietary intellectual property is a massive hit to the bottom line and erases any competitive advantage in the marketplace."
Winnti has a history of long-term campaigns that establish persistent access to corporate networks. In 2020, the U.S. Department of Justice charged five Chinese nationals and alleged members of the APT group, accusing them of hacking more than 100 organizations across the globe.







