
kras99 - stock.adobe.com
Who is responsible for secure remote access management?
The pandemic exposed the need for a strong secure remote access strategy. Now, organizations need to figure out which team must make it happen.
The COVID-19 pandemic put a spotlight on enterprise technology professionals, especially security professionals, and the resiliency of cybersecurity processes, tools and technologies. For the most part, they passed with flying colors. However, many companies have yet to scrutinize how cybersecurity teams are organized and how they should be organized. Specifically, which group is responsible for managing secure remote access? And, if it's possible to determine, which group should be managing secure remote access?
Nemertes asked these questions -- in a slightly different form -- in our "Beyond SASE" cybersecurity research study released in May. We included 157 participants from the U.S. and Canada and drilled into a host of operational and technology areas, focused specifically around Secure Access Service Edge (SASE) and its adjacent technologies, including software-defined perimeter (SDP).
We asked, among other things, who selects, implements and operates these technology areas. We also defined a success metric we call SIPI, or serious incident per incident, as the percentage of security incidents that are serious, where serious is defined as having an impact on employees, customers or business operations or requiring alerting external parties, e.g., law enforcement. Those with the lowest SIPIs -- the fewest serious incidents per security incident -- are considered the most successful.
We selected the 21% of companies with SIPIs of 2% or less as the "success group." Then, we looked at what the successful companies -- again, by the SIPI metric -- are doing that differs from what less successful companies are doing.
Secure remote access is a capability rather than a technology, so we didn't examine it directly. Instead, we looked at the technologies that enable secure remote access. In the technologies we studied, SASE and SDP are most typically used to enable secure remote access.
Cybersecurity teams lead the way
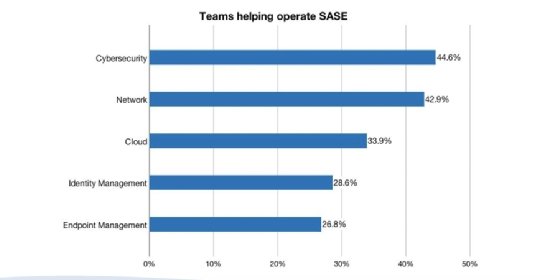
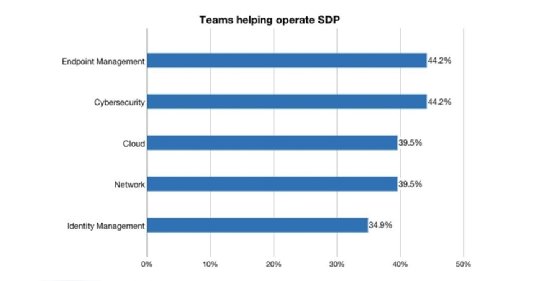
The results are intriguing. With both SASE and SDP, for participants overall, cybersecurity teams are the most common teams cited by participants to select, build and manage these technologies. Note that we asked participants to select all teams that were involved in each function. The majority of participants reported a mix of teams -- rather than a single team -- so the percentages don't necessarily add up to 100%. See Figures 1 and 2.
However, when we compared the success group to all others, we found significant differences between successful companies and those not in the success group.
Specifically, for SDP, within the success group, the team most commonly cited by participants as involved in managing SDP was the cloud team; the cloud team was 25% more likely to be selected by successful organizations. For all others -- those not in the success group -- the endpoint management team was most common.
Network, endpoint teams not secure remote access go-tos
Moreover, it's worth looking at which teams were less likely to be at successful organizations. Interestingly, the network team was 47% less likely to be involved in managing SDP in the success groups, and the endpoint team was 25% less likely.
For SASE, within the success group, the team most commonly cited by participants as involved in managing SASE was the cybersecurity team, which was also the case for all others -- those not in the success group. However, the next most commonly cited team for successful organizations was the identity management team, which ranked last for the less successful organizations. Moreover, the successful organizations were 77% less likely to have the cloud team involved in running SASE and 41% less likely to have the network team doing so.
What to make of all of this? The big takeaway, other than to have the cybersecurity team involved, is that the right mix of teams depends in part on how you're implementing secure remote access. If you're using SASE, try having the identity management teams involved; if you're using SDP, consider looping in the cloud team.







