
Alex - stock.adobe.com
How can users securely access Google Cloud Storage?
With security top of mind across IT, consider best practices for safe Google Cloud Storage access. Admins should be careful about assigning roles and permissions.
Google Cloud Storage places data into buckets or containers with specific rules for the type of data and the frequency of its usage. To access Google Cloud Storage, users can sign in to the specific service and account, typically through a set of screens, but should consider security best practices to keep data safe.
Google stores data as objects and encrypts it at rest and in transit. When an organization prepares to store data in a Google bucket, it must establish the lifecycle configuration for the bucket. From a security perspective, users can access buckets they create but may not have access to buckets others create. In such cases, the bucket owner must assign the requesting user a role that has the required permissions to access that bucket.
Google Cloud Storage permissions and roles
Permissions for security access are defined in identity and access management (IAM). Use combinations of permissions to create roles and grant access to specific data.
Figure 1 provides a sampling of permissions.
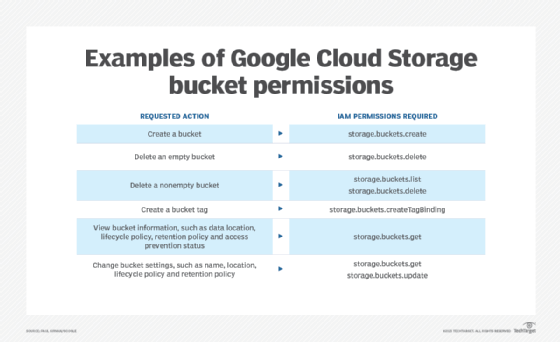
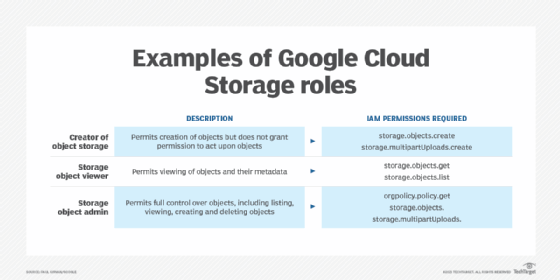
Figure 2 provides examples of roles for Google Cloud Storage users.
Security best practices to access Google Cloud Storage
Google provides a selection of best practice guides to address security for multiple situations, such as deployment guidance, configurations, architectures and settings. Users should familiarize themselves with these guides to safely use and access Google Cloud Storage. Here are some of them:
- Cloud security foundation blueprint guide. This is the starting point for building security into Google cloud deployments and includes access, structure, authentication, hierarchy of resources, networking, logging and other controls.
- Enterprise deployment best practices. This guide is designed for enterprise architects.
- Security and compliance architecture. This provides guidance on security and compliance issues and for migrating workloads to Google Cloud.
- Best practices for IAM. This site offers help on security and access controls for Google deployments.
- Security best practice checklists. These checklists provide security guidance for small, medium and large businesses that use Google Cloud services.
As with any cloud implementation, due diligence is perhaps the most important activity before starting. Research websites, blog posts and other information sources to identify good practices. Understand Google Cloud, how it is organized, its various policies, guidance on how to plan and deploy, networking elements and security measures. Also, know how to detect, analyze and manage threats.
Build a strong security posture. If the organization must comply with certain regulations, such as the EU's GDPR or HIPAA's Security and Privacy Rules, factor them into the overall security approach. Compliance with such regulations is increasingly important -- take it seriously, especially when users access Google Cloud Storage and other cloud-based resources.
To help reduce the likelihood of cyber threats, reduce the attack surface of the cloud implementation, and isolate traffic from potential external threats. Be mindful of potential security audits that inspect how the organization manages access to Google Cloud Storage. Audits examine security controls, review documented security procedures and conduct live verification with penetration tests.
Security risks for Google Cloud Storage
Google has developed a broad spectrum of security features, guidance and programming across its cloud offerings. As with all data security practices, care and preparation are essential with the understanding that, despite all reasonable preparations, unauthorized access to user data, systems and other resources is possible.
Breaches that affect well-known companies are many, and fortunately, cloud storage mitigated many of these breaches. By contrast, rogue cloud company employees with access to customer information can present a serious threat to cloud security.
Use of the security best practice resources noted above, plus consultation with technical staff, will help admins provide access to Google Cloud Storage securely and be ready for a cybersecurity event.







