
Getty Images/iStockphoto
Learn to work with the Office 365 unified audit log
Administrators who need to check on suspicious activities in the Office 365 platform can perform a unified audit log search to help with their investigation.
It's important to understand all the Office 365 administrative tools at your disposal, particularly when they relate to security.
Administrators in charge of Microsoft Office 365 services rely on the centralized management console for details around user activities and events in the system. An added layer of surveillance in the form of the unified audit log, which provides deeper insights into the events happening in the Office 365 tenant, including admin activity. At a time where more companies are using Office 365, which consequently draws more attention from threat actors, IT workers should be more proactive and use the unified audit log to check for any suspicious activity.
The unified audit log is a valuable component to Office 365 because it helps administrators handle a wide range of requests from different departments related to users. Some examples of these requests include:
- review of file deletions or access;
- review of activities by users regarding sensitive data;
- review of user sign-in behaviors as part of a security incident;
- review of any recent administrative permission changes in the system;
- review of file deletions; and
- review of recent file downloads or extractions to external devices.
When they managed on-premises systems, administrators would have to log in to several areas, such as the Exchange admin console, central administration in SharePoint, Active Directory and file servers, to satisfy these information requests. But on Office 365, Microsoft centralized administrative activities under one management portal for Exchange Online, Yammer, Microsoft Teams, OneDrive, Power BI, Dynamics 365, Power Automate (formerly Microsoft Flow), Power Apps, Microsoft Forms, SharePoint Online, Azure Active Directory (AD), Sway and the Security and Compliance Center.
The majority of the audit requests for these services can be fulfilled by using the Office 365 unified audit logs from the security admin portal via the protection.office.com/unifiedauditlog URL. The audit log search function gives IT workers a way to narrow results using several criteria, such as the activity and a time frame.
How to perform an Office 365 unified audit log search
Officer 365 administrators must be vigilant for signs of data breaches or hacking. The Office 365 unified audit log helps audit events to identify any suspicious activities across the Microsoft services. For example, to reveal activity related to file deletions, administrators can set the date range and select delete from the Activities menu.
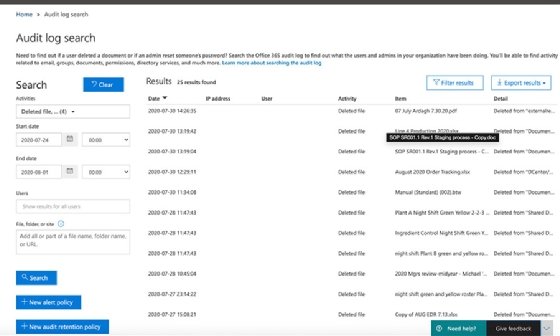
Exchange administrators can use the unified audit log for email-related audits to uncover suspicious activity, such as large amounts of deleted email. These actions can be a sign of either foul play by an employee or a hacker's attempt to hide their activity after hijacking a user's credentials.
Administrators can export audit records into a comma-separated values (CSV) file for review in Microsoft Excel or Power BI.
How to use PowerShell to search the unified audit log
Administrators who prefer to use PowerShell can also use the ExchangeOnlineManagement module, also known as the Exchange Online PowerShell V2 module, which includes the Search-UnifiedAuditLog cmdlet. Despite the name, the ExchangeOnlineManagement module uncovers events in the other Office 365 services, similar to the GUI version in the admin portal.
The cmdlet provides several parameters including the date range, user ID and text strings to define the criteria to narrow the results. The following example will search for the activities of a specific user between the start of January and end of March.
Search-UnifiedAuditLog -StartDate 1/1/2022 -EndDate 3/31/2022 -UserIds "[email protected]"
The default results setting of the Search-UnifiedAuditLog cmdlet is 100 but can be adjusted using the -ResultSize parameter, with a maximum of 5,000. For more information related to this cmdlet, check the documentation at this link.
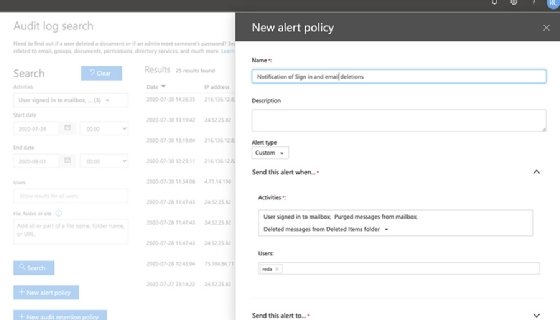
How to set up alerts to get notifications about suspicious activity
Administrators can set up alert policies to get notifications for specific user activities. The example in the screenshot sends email notifications when a user purges messages from a mailbox or deletes email from the deleted items folder. IT workers can configure alerts for other activities in the system and for all users or specific ones.
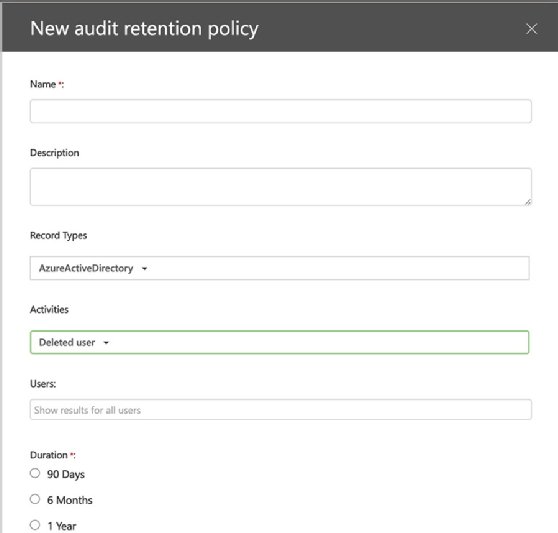
How to change the retention policy for the unified audit log
Despite the ability to access information across multiple Office 365 services, one key limitation is the length of time the unified audit log is available. Microsoft allows access to the last 90 days of audit data.
Customers who subscribe to Office 365 E5, Microsoft 365 E5 license, Microsoft 365 E5 Compliance or Microsoft 365 E5 eDiscovery with the Audit add-on license have a default setting of one year for Exchange Online, SharePoint Online and Azure Active Directory. For other customers, administrators have the option to use the audit retention policy to hold data for up to one year, but this requires the admin to manually configure those settings.
For organizations that use a Security Information and Event Management (SIEM) product, the Office 365 Management Activity API lets third-party vendors query the content of the unified audit log. Products such as Sumo Logic Cloud SIEM can input information related to Office 365 user activity and details related to network traffic, servers and system events.
The unified audit log is designed to provide some visibility into what end users do in Office 365. While it tracks several critical user activities, the unified audit log alerts should not be used as the primary tool to protect the organization from attackers. Rather, the unified audit log is meant to show the timeline of user activities and their origin to assist with investigations.






