
rvlsoft - Fotolia
Using the Office 365 Recommended Configuration Analyzer
Learn how this free PowerShell-based utility digs into your Office 365 security setup and offers guidance for administrators looking to stop the latest online threats.
Online threats keep evolving, making it difficult for Office 365 administrators to tighten up security on the tenant.
To help with this effort, Microsoft provides several ways to identify security gaps in the existing Office 365 setup and configuration. One tool is the Office 365 Recommended Configuration Analyzer that provides valuable recommendations on how to best configure Microsoft Defender for Office 365, formerly called Office 365 Advanced Threat Protection, and Exchange Online Protection.
Best practice analyzers are a set of tools that Microsoft provides for several of their key server products and services, such as Exchange, Active Directory, SQL and Office 365. These tools scan the environment configuration settings and then provide a report consisting of recommendations to align the system with Microsoft best practices. Given that security looms large for IT, Microsoft introduced the Office 365 Recommended Configuration Analyzer -- sometimes referred to as ORCA -- to provide feedback to administrators for their Exchange Online settings and flag any areas that may need adjusting to improve the overall security and protection of their email environment.
ORCA is a PowerShell module designed to work with any Office 365 tenant with at least Exchange Online as part of the subscription plan. The analyzer focuses on highlighting security and protection settings within the tenant related to email and general tenant settings. Using the tool requires administrative access, either the global or Exchange admin role, to the Exchange Online subscription and some familiarity with PowerShell.
To get started with the Office 365 Recommended Configuration Analyzer, run the following commands from PowerShell:
- Start PowerShell as an administrator from a machine connected to the internet
- Install the ORCA module using the following command: install-module -name orca
- Connect to Exchange Online PowerShell with the Connect-ExchangeOnline command
- After a successful login into the environment, execute the following command: Get-ORCAReport
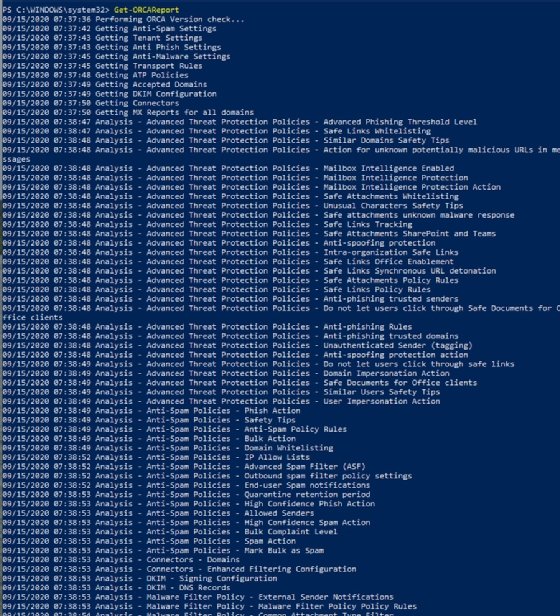
After the ORCA PowerShell cmdlet runs, it generates an HTML report that is saved on the user's computer. The path to the file is at the end of PowerShell text.
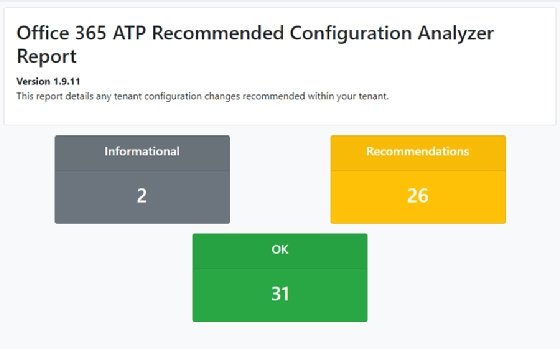
The Office 365 Recommended Configuration Analyzer checks eight areas: Anti-Spam Policies, Advanced Threat Protection Policies, DKIM, Malware Filter Policy, Transport Rules, Zero-hour Auto Purge, Tenant Settings and Connectors.
For each of the sections, the ORCA report provides details and makes recommendations based on what it detected during the scan of the tenant and its configuration. Microsoft also provides links with more details about suggested changes and links in the Office 365 admin portal where to make the modifications.
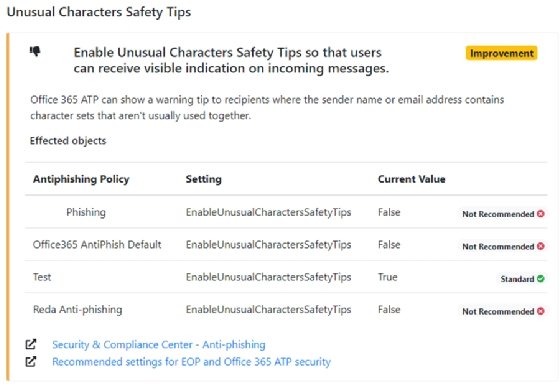
When best practices and necessity collide
Office 365 administrators benefit from using these best practices reports to provide valuable insights into potential issues with the tenant configuration that could pose risks for end users. However, the report can produce false positives.
In some areas, IT may have intentionally configured the system to allow for some settings, even when the ORCA report marks them as not recommended. For example, IT might have added specific domain names to the allowlist to permit email that would otherwise have been blocked by the antispam filter. This is a common scenario when using tools such as KnowBe4, Phish Insight and Gophish that send a fake email to test their user vulnerabilities. These services require some domain names to be on the allowlist, which the Office 365 Recommended Configuration Analyzer might flag.
Another possible false positive is the use of SMTP relay connectors. Administrators will set these up on an on-premises Exchange Server to let legacy systems that do not support sending email through Office 365 use a local relay server for outbound email.
IT leaders recognize the importance of security, whether it relates to hosted services in the cloud or workloads in the data center. With ever-growing threats from bad actors and the increase in remote workers accessing corporate data from personal devices, IT administrators need to use every available tool to continuously assess their protection levels. Microsoft's own security assessment utilities, such as ORCA, are recommended because the company has access to all the back-end environments and can offer informed guidance to protect Office 365 customers.






