Getty Images/iStockphoto
How to join Linux to an Active Directory domain
This tutorial explains the benefits of this integration, how to connect Linux systems to the Microsoft directory service and how to troubleshoot authentication issues.
As more organizations adopt multi-platform environments, the role of the Windows sysadmin is evolving.
Microsoft administrators in those organizations are now responsible for managing Linux systems alongside the traditional Windows infrastructure. This responsibility can be daunting, but integrating Linux systems into Active Directory (AD) can alleviate some of this anxiety by providing a unified authentication and identity management approach. This article will explain why this integration can benefit the organization, some of the typical challenges that occur when adding Linux machines to Active Directory and how to perform troubleshooting from Linux systems.
Why join Linux machines to Active Directory?
1. Centralized user management
One of the primary reasons to integrate Linux machines with Active Directory is centralized user management. Organizations can use existing user accounts, groups and security policies. Administrators can manage user permissions, authentication and policies from a single point, streamlining operations and minimizing administrative overhead.
2. Enhanced security compliance
Active Directory offers enterprise-grade security features such as password policies, multifactor authentication, group policies and account lockout thresholds.
Extending Active Directory to Linux systems ensures consistent security enforcement and compliance across Windows and Linux systems, reducing vulnerabilities and enhancing overall security posture.
3. Resource management
Domain-joined Linux machines simplify resource management, allowing users to access shared resources such as file shares and printers without needing multiple accounts. This can improve productivity by providing seamless access to shared resources across platforms, fostering a more cohesive user experience.
Note that Linux machines cannot use Group Policy Object (GPO) policies and Windows-centric management tools, even after they are domain-joined.
Challenges for Windows sysadmins
Many Windows admins prefer a graphical user interface (GUI) for system management. However, Linux system administration relies heavily on command-line interface (CLI) operations. This transition can be challenging, as many straightforward tasks in a GUI-based tool, such as Active Directory Users and Computers (ADUC), may require more complex commands in Linux.
Linux and Windows use different file systems, which can lead to confusion. For example, Linux uses a hierarchical file system starting from the root directory (/), while Windows uses drive letters. Permissions also differ significantly: Linux employs a user/group/other permission model, while Windows uses Access Control Lists (ACLs) that allow for more granular permission settings but with more complexity.
In Windows, user and group management is often handled through AD, which provides a straightforward model for assigning permissions. In contrast, standard, out-of-the-box Linux employs a simpler model, with users and groups defined in files. Understanding these differences at the conceptual level is crucial for effective management and troubleshooting.
Active Directory pre-flight checks
Follow this checklist of items to verify before attempting to set up Linux on Active Directory. Finishing this advance work will help avoid troublesome issues later.
- Verify connectivity: Use ping to check basic connectivity between the server and Linux clients. Ensure the required ports are open on the server. Rather than disabling firewalls, configure them to allow specific traffic from Linux clients to the server.
- DNS configuration: Make sure your client can perform an nslookup on the Active Directory server's fully qualified domain name (FQDN). It is vital to have the correct time set and synced across all the servers. Set up servers to use the same local DNS server to avoid complex DNS issues.
- Time synchronization: Ensure correct time settings and synchronization across all servers involved. Time discrepancies can cause authentication failures and other critical issues.
Configure SSSD for Active Directory integration
The System Security Services Daemon (SSSD) is a key component for connecting Linux systems with Active Directory. SSSD offers the integration functionality from Linux to several back-end authentication mechanisms, with particularly strong support for Active Directory domains. This enables seamless authentication between Linux systems and enterprise directory services
The following guide explains how to set up and configure SSSD on an Ubuntu VM to interact with a Windows 2019 Active Directory domain controller.
Install required packages
First, install the following packages: sssd-ad, sssd-tools, realmd and adcli. You can install them using the Ubuntu package manager.
sudo apt update
sudo apt install -y sssd-ad sssd-tools realmd adcli cifs-utils
Discover the Active Directory domain
The realm command to discover and verify the Active Directory domain depends on proper DNS and Kerberos functionality.
sudo realm -v discover Active Directory.tttest.local
If successful, the Linux system will find and gather information about the Active Directory domain.
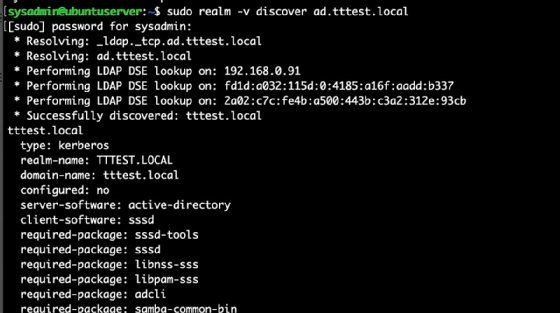
Check all dependencies
If there are errors, it is very likely a DNS issue. Issues with DNS resolution cause a large proportion of join errors. Also, check for time skew. Lastly, ensure the host name and the FQDN are correct and share the same network domain name and name server.
Join the Active Directory domain
To join the domain, use the following command:
sudo realm join --user=administrator yourdomain.com
Replace administrator with an account that permits machines to join the domain. For this tutorial, we are using the domain administrator account.
To verify the domain join, use the command:
sudo realm list
The output will show all Active Directory domains the system is connected to if properly integrated. To verify, check the ADUC tool on Windows Server. The Linux system should appear in the Computers container.
At this point, you can log in to the Linux system using Active Directory credentials. However, users must use the fully qualified login name, such as [email protected], rather than just the user name bob.
When configuring the domain configuration, the realm command will make the changes to enable basic Active Directory authentication. This same process can be used on Ubuntu Desktop with the Use Active Directory option during installation.
Be aware of sssd.conf
After joining the domain, know that the SSSD configuration file (sssd.conf) exists. You can customize it further to optimize authentication. While the basic domain join gets default settings, you may need to adjust this file for specific authentication requirements.
Configure host resolution and CIFS
To use Windows file sharing, you must configure Common Internet File System (CIFS), a network file-sharing protocol. We have already installed the required package to start the CIFS configuration.
Edit the /etc/fstab file to add entries for your Windows file shares to have them mount automatically at boot.
//server/share /mnt/mountpoint cifs credentials=/path/to/credentials,uid=1000,gid=1000 0 0
To test the mount without a reboot, run the following command:
sudo mount -a
No errors mean it was successful. If there are errors, it's usually due to formatting problems.
Be aware of some more nuanced aspects of CIFS security. You can apply Linux filesystem permissions to mounted Windows file shares. Linux uses numeric mode values to set permissions, such as 0755 for owner/full access. These permissions only apply at the share mount level, not to individual files within the Windows system. Linux permissions act as an additional filter on top of Windows ACLs, which means a file will not be accessible if the Linux permission restricts access, even if the user has access via the Windows ACL. Windows admins must learn how to adapt to this hybrid arrangement, which can lead to issues since two permission systems are in effect simultaneously.
Troubleshooting Linux integration with Active Directory
Interpret Linux system logs
One of the best tools for troubleshooting in Linux is system logs, typically located in /var/log directory. Key logs to review for problems include:
- /var/log/secure: Authentication logs that capture SSSD events.
- /var/log/messages: General system messages.
- /var/log/syslog: Comprehensive system and service messages.
Use the tail command to view logs in real time:
tail -f /var/log/secure
Get familiar with diagnostic tools
If a user cannot log in, use these diagnostic tools:
- id "username" - Check if the system recognizes a user.
- getent passwd "username" - Display user account information from Active Directory.
- sssctl - A command-line tool for SSSD that shows information about users, groups and cache status.
Key takeaways for integrating Linux with Active Directory
Integrating Linux machines into Active Directory brings several benefits, including centralized user management, consistency with security policies and compliance, and simplified resource access.
While challenges exist, particularly for Windows administrators transitioning to manage Linux systems, it's essential to learn the key differences in permission models, how to work with file-based configurations and how to use the command line for troubleshooting.
By following the outlined steps for configuring SSSD and utilizing diagnostic tools, IT teams can effectively manage a multi-platform environment that takes advantage of the strengths of both Linux and Windows systems.