End-users are increasingly relying on web browsers as their primary access to corporate applications and data. The most commonly used web browsers are Google Chrome, Mozilla Firefox, Microsoft Edge, and Apple Safari. Due to advances in technology, security, and internet speeds, browsers can provide several advantages in a corporate environment compared to PC and mobile operating systems. Yet browser security remains a major issue among IT professionals charged with managing security patches, updates, and policies as part of an overall end-user computing (EUC) strategy. As businesses accelerate the adoption of applications accessed through web browsers, and IT continues to improve support and security for multiple browsers, enterprises may one day treat browsers as the de facto operating system in a corporate environment.
Insight
-
-
The significant performance and bandwidth advantages of 5G cellular networks have numerous implications for businesses as well as consumers. 5G has the potential to deliver reliable connections for hybrid work and collaboration strategies while enabling augmented reality and other multimedia applications to run on a wider range of endpoints and locations. To realize these opportunities, IT leaders should consider 5G integral to their network infrastructure plans and strategies.
-
Forgive me for the blatant cheesiness of the title, but in this case, using the term hacking is sort of relevant…bear with me…
No doubt that working in cybersecurity is really THE thing to do right now. The opportunities seem endless. But exactly what paths can you pursue when entering a field that is constantly evolving?
I had the opportunity to discuss one path with Gisela Hinojosa, a pentester at Cobalt. For those not in the know – like me – I thought…huh? Pentesting? Perhaps a simple, albeit naïve, way of understanding what is pentesting (or penetration testing) could be hacking. As a pentester, you attempt to expose potential security vulnerabilities. Basically, you are hacking for legitimate reasons.
As you will hear during our conversation, Gisela worked in software testing before she uncovered this specific path. As she was exploring different options, her husband asked what she always wanted to do. She replied that she wanted to hack, but who would pay her to do that? Turns out that companies do to bolster their security posture before any bad actors have the chance.
What exactly does it take to find a pentesting position? Watch this video and find out what worked for Gisela.
Please visit Enterprise Strategy Group’s Women in Cybersecurity page, where you can also find a link to the full audio interview with Gisela, view past episodes, and join us to hear more inspiring stories in future shows.
-
ESG conducted a comprehensive online survey of IT and cybersecurity professionals from private- and public-sector organizations in North America (United States and Canada) and Western Europe (UK, France, and Germany) between December 21, 2021 and January 10, 2022. To qualify for this survey, respondents were required to be IT and cybersecurity professionals involved with the technology and processes associated with protecting against ransomware.
This Complete Survey Results presentation focuses on understanding the proactive and reactive measures organizations have in place to defend against the growing ransomware threat, and identifying the priorities and plans associated with mitigating the ransomware threat in the coming 12-18 months.
-
This episode of Women in Cybersecurity showcases Brittany Greenfield, the founder and CEO of Wabbi. While Brittany started her career with a degree in biotechnology, working in business process and marketing roles, she turned her focus to cybersecurity, knowing how critical it is in the fabric of technology. Today she leads a company integrating security into software development. Check out our video below.
Growing up in Washington D.C., Brittany had an impression of cybersecurity as how agencies protected the country against foreign enemies. She went to Duke University earning a self-designed interdisciplinary degree in biotechnology, spanning economics, entrepreneurship, public policy, and medical sciences. From there, she spent the first part of her career in the ERP space, and later earned an MBA from MIT Sloane School of Management.
She turned to cybersecurity when she took a role at Cisco helping them build their Internet of Things (IoT) platform.
You can’t talk IoT and not talk cyber. I realized cyber is such a fundamental piece of the digital fabric that powers our lives today, I need to get into it.
She got into the endpoint space, and became frustrated that too many solutions focused on perimeter security, when she felt that the problems need to be solved within. From there, she decided to found Wabbi to help developers efficiently incorporate security into their processes, getting the right security information to developers at the right time.
Tune in to the video, and don’t miss the full podcast, as we discuss key issues, including why women make good leaders. Also, since Wabbi is in my coverage area of cloud and application security, we discuss some of the challenges for organizations trying to scale their security programs with the speed of modern software development.
Learn more about her company Wabbi, and if you’re heading to RSA next week, visit their booth and get a demo! You can also follow her on twitter.
Please visit Enterprise Strategy Group’s Women in Cybersecurity page, where you can also find a link to the full audio interview with Brittany, view past episodes, and join us to hear more inspiring stories in future shows.
-
ESG conducted a comprehensive online survey of IT and cybersecurity professionals from private- and public-sector organizations in North America (United States and Canada) between December 14, 2021 and December 28, 2021. To qualify for this survey, respondents were required to be IT and cybersecurity professionals focusing on identity and access management programs, projects, processes, solutions/platforms, and services.
This Complete Survey Results presentation focuses how organizations are currently monitoring and protecting identities in terms of the breadth of identity products, platforms, and technologies supporting current business operations, as well as how that is expected to evolve over time.
-
From frequent attacks on critical systems to major data recovery issues and financial impacts, ransomware consequences refuse to be ignored.
See the data behind these trends and more with this Enterprise Strategy Group Infographic, 2022 Ransomware Landscape.
-
The ransomware threat is a top-of-mind issue for so many organizations; however, few feel totally prepared for an attack. Without an industry reference architecture or blueprint for ransomware protection, organizations are building their own strategies and processes to respond. But with ransomware protection included with so many different security and data protection solutions, many are confused about the scope of what is to be included, who is responsible for the implementation, and who needs to be involved in the conversation.
In order to connect the dots between those organizations that feel most prepared and the specific strategies and plans they are using to get there, with an eye on defining best practices, ESG surveyed 620 IT and cybersecurity professionals personally involved with the technology and processes associated with protecting against ransomware attacks at midmarket and enterprise organizations in North America and Western Europe.
For more information on this research, please visit www.esg-global.com/ransomware.
-
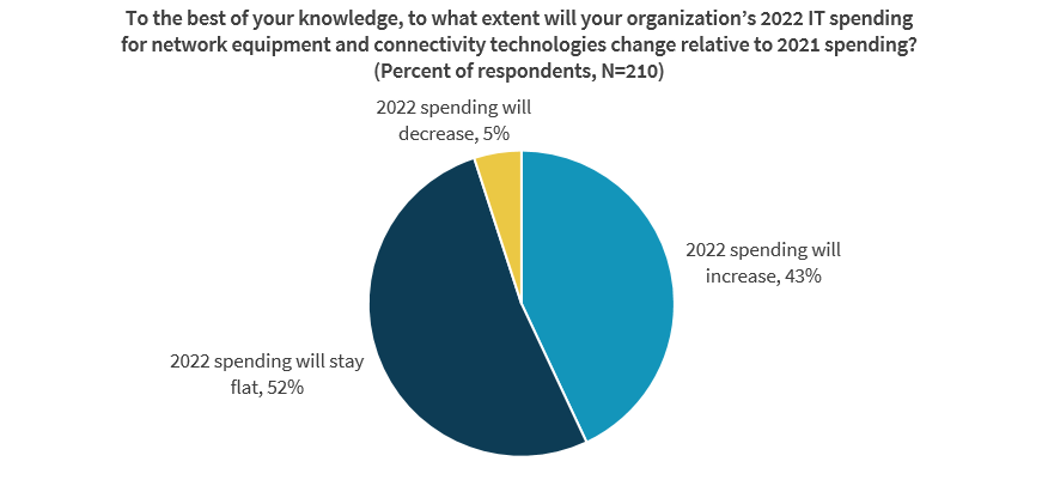
Enterprise Strategy Group’s annual technology spending intentions report for 2022 surveyed 706 senior IT decision-makers at midmarket (i.e., 100 to 999 employees) and enterprise (i.e., 1,000 or more employees) organizations across North America, Western Europe and Asia Pacific. From an overall perspective, the good news is that 62% of organizations plan to increase overall IT spending. As part of that research, respondents with purchasing influence or authority for networking products and services were asked about their organization’s spending plans in this area over the next 12 months. The data indicates that 52% are expected to maintain the prior year’s budget levels and 43% will increase spending. Only 5% will shrink their networking budget.
 Given that modern IT environments are highly distributed and complex, ESG also asked respondents to identify the areas where their organization would make the most significant investments in its network infrastructure over the next 12 to 18 months.
Given that modern IT environments are highly distributed and complex, ESG also asked respondents to identify the areas where their organization would make the most significant investments in its network infrastructure over the next 12 to 18 months.More than one-third (38%) of organizations will provide additional training to their networking staff on modern IT operations best practices; 36% will deploy cloud-based network management solutions; and 35% will deploy AI/ML for network self-healing and optimization capabilities. The responses largely confirm the demand for technologies highlighted in a 2021 ESG research report on network modernization.
As organizations modernize their IT and application environments, they recognize that doing so requires training network staff to ensure the network can support these new IT operations and best practices. The faster growth of closely related IT priorities — many driven by post-COVID-19 hybrid work environments — including cybersecurity and distributing applications to the cloud or edge, suggests that network infrastructure will continue to play a vital role in enabling these environments.
-

In the wake of the 4th annual Amazon Web Services (AWS) user conference, AWS has finally emerged as a leader in cloud infrastructure and platform services. AWS now has over 1 million active customers and year-over-year growth in EC2 instances, data transfer, and database use that is close to 100% as of 2015 Q2. AWS did $4.6 billion in revenue in 2014 and expects to see $7.3 billion by the end of 2015 which is close to 60% growth. Amazon is now adding over $1 billion in new revenue per quarter. It’s rare to see these kinds of growth rates in a business that is closing in on 10 years old. This shows the transformative effect that cloud services are having on the IT business.
But the high growth of AWS is far more than a story about being in the right place at the right time. Although AWS was a pioneer in the IaaS and PaaS market segments, plenty of vendors, including storied names like Microsoft, IBM, and Oracle, now have a strong cloud presence. Survey data also shows private cloud being a preferred path forward which is a path that AWS doesn’t support. So what is it about AWS that sets it apart from its competitors? We believe that it boils down to one factor: operational excellence.
AWS and Amazon both hold the objective of high volume and low cost as core values that are part of their DNA. While it’s easy for most vendors to make occasional efficiency claims, the growing strategic importance of IT meant that enterprises have been trained that they need to pay to play. This has been especially true since 2000 in the highest growth area of IT, which was software. Much of this software revenue was tied to proprietary products with high price tags and licensing policies that in today’s world seem punitive. While open source software products have been successful as low cost alternatives, they address a different target market due to their unique business model, which impacts their scope and performance. The net result has been an IT market that has grown weary of high prices and is ripe for disruption.
From the start, AWS has designed its data centers to deliver reliable services on demand at a low price. AWS has now perfected the process of designing, building, and operating data centers. AWS employs purpose-built servers, storage, and networks which enables them to carefully control costs while ensuring delivery of reliable on-demand services. AWS has also mastered how to manage their supply chain to make sure they are well insulated from cataclysmic events given the rate at which they now are bringing capacity online. This operational excellence also extends to how AWS develops software services. These services often have their roots in open source but are reengineered by AWS to improve performance. The result has been 516 new services launched in 2014 and 487 so far in 2015. AWS has now reached a point where from an IaaS and PaaS perspective they have comprehensive offerings with significant depth in infrastructure, security & compliance, integration, analytics, application services, mobile services, development, operations, and support.
Because all of this has been developed with a continual eye on delivering high volume at a low cost, AWS pricing sets the bar to beat in the industry. While Microsoft and Google monitor and adjust their prices to achieve parity or leadership in some cases, AWS is driving margins of 17%, meaning that it would be hard for them to lose any race to the bottom. Now that AWS has demonstrated that they can deliver reliable on-demand services worldwide, enterprises are taking notice. The number of enterprises now all in on AWS has exploded in 2015 and we see this largely as a recognition that AWS’s focus on operational excellence is a winning strategy. However, while other strategies such as product leadership and customer intimacy are also formulas for success, AWS is pursuing a strategy that is new to the IT market where there is a vast sea of pent-up demand for exactly what AWS is delivering.
-
See how IT professionals use cloud-native applications to help advance their businesses into the future with this free Enterprise Strategy Group Infographic, Distributed Cloud Series: Cloud-native Applications.
For more information or to discuss these findings with an analyst, please contact us.
-
The core tenet of a zero trust strategy is least-privilege access. Yet, organizations continue to rely on user and machine identities that are susceptible to compromise, abuse/misuse, and theft. Risk is compounded by over-permissive, static access rights that provide little to no visibility into who and what is using access and how. Vaguer is how identities are being/should be monitored and protected. Availability of modern, cloud-managed identity services is widespread. Yet organizations have been slow to pivot their security programs from traditional endpoint, network, and SecOps to an approach that focuses on identity orchestration and experiences, which is dynamic and distributed. Where there are no perimeters, a multitude of identity verification services and managed identity services exist.
In order to gain insights into these trends, ESG surveyed 488 IT and cybersecurity professionals personally responsible for identity and access management programs, projects, processes, solutions/platforms, and services at large midmarket (500 to 999 employees) and enterprise (1,000 or more employees) organizations in North America (US and Canada).

 Given that modern IT environments are highly distributed and complex, ESG also asked respondents to identify the areas where their organization would make the most significant investments in its network infrastructure over the next 12 to 18 months.
Given that modern IT environments are highly distributed and complex, ESG also asked respondents to identify the areas where their organization would make the most significant investments in its network infrastructure over the next 12 to 18 months.