Manage shadow IT with Microsoft Defender for Cloud Apps
Managing shadow IT doesn't have to be a daunting task. With Microsoft Defender for Cloud Apps, users can reap the benefits of cloud, while mitigating the risks of shadow IT.
As technology continues to evolve, organizations need to be vigilant and stay ahead of emerging security threats. By taking proactive steps to manage shadow IT, organizations can ensure the safety of their cloud environment and maintain a strong security posture.
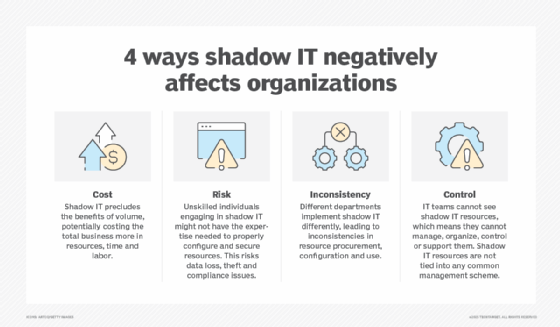
Shadow IT refers to the use of technology, applications and services in a company without the IT department's explicit consent or knowledge. This practice can encourage innovation and boost productivity by enabling employees to use familiar tools. It also brings about considerable risks and challenges.
Unapproved technology can result in data breaches, nonadherence to industry regulations and increased expenses due to overlapping or extra tools. Further, shadow IT complicates the IT department's responsibility to manage and safeguard an organization's technology infrastructure, driving the need for comprehensive visibility into all systems and applications.
To address these risks and reestablish control, IT teams must comprehend the root causes and potential outcomes of shadow IT -- and adopt practical management approaches. One strategy is to use a tool such as Microsoft Defender for Cloud Apps, a cloud access security broker that helps organizations mitigate risks and regain control over their technology environments.
In a previous article, we explored what Microsoft Defender for Cloud Apps is and how to set it up. Here, we discuss how to set policies in Defender for Cloud Apps to manage shadow IT.
Implement policies and controls to prevent shadow IT
Microsoft Defender for Cloud Apps provides a range of policies and controls that organizations can implement to prevent shadow IT and improve their cloud security posture. These policies and controls include monitoring cloud applications for unsanctioned usage, blocking access to high-risk applications, enforcing data loss prevention policies, and identifying and mitigating threats.
By using these policies and controls, organizations can reduce the risk of data breaches, ensure compliance with regulatory requirements, and gain better visibility and control over their cloud environments.
The following are a few examples of the policies and controls that Defender for Cloud Apps enables:
- Monitor cloud applications for unsanctioned usage.
- Block access to high-risk applications.
- Enforce data loss prevention policies.
- Identify and mitigate threats.
- Create and enforce user access policies.
- Monitor and manage third-party apps and services.
- Conduct regular security assessments and audits.
Best practices to manage shadow IT with Defender for Cloud Apps
To manage shadow IT with Defender for Cloud Apps effectively, organizations should follow several best practices.
Establish usage policies
It's essential to establish clear policies and guidelines around cloud application usage and communicate them clearly to employees. This step can help prevent unsanctioned use of cloud applications and ensure that employees understand their responsibilities when using company-owned devices or accessing cloud services.
Implement security controls and tools
Organizations should implement security controls and tools to detect and prevent shadow IT. Defender for Cloud Apps provides a range of features and functionalities, such as monitoring cloud applications for unsanctioned usage and enforcing data loss prevention policies.
Other best practices for managing shadow IT with Microsoft Defender for Cloud Apps include the following:
- Communicate policies and guidelines to employees.
- Regularly audit and review cloud apps for shadow IT.
- Train and educate employees on the risks of shadow IT and the importance of compliance.
- Vet and approve all third-party cloud apps and services.
- Monitor and manage third-party apps to ensure compliance with company policies and security standards.
- Regularly assess and address cloud environment vulnerabilities.
How to create policies in Microsoft Defender for Cloud Apps
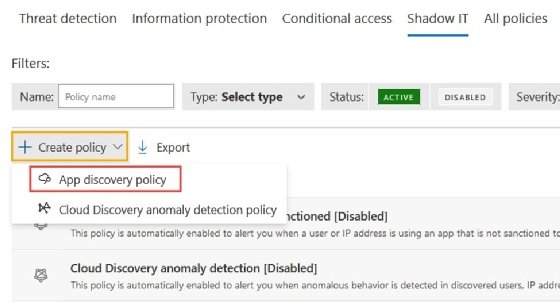
To add a policy, such as Monitoring cloud applications for unsanctioned usage, navigate to Security Center, expand the Cloud Apps section and then select Policies.
Now, follow these steps:
- Step 1. Click Policy Management.
- Step 2. Select the Shadow IT heading.
![Screenshot showing the option to set a shadow IT policy in Defender for Cloud Apps]()
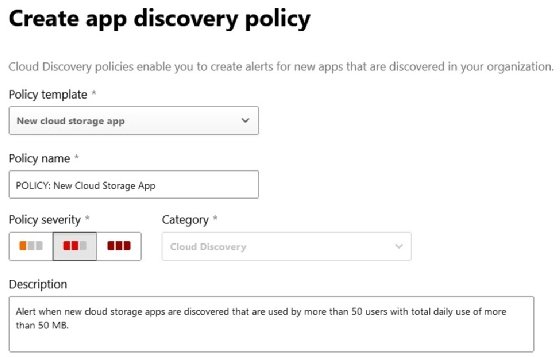
- Step 3. Click Create policy, and select App discovery policy.
![Screenshot showing the option to create an app discovery policy]()
- Step 4. Set the policy name, severity and description.
![Screenshot showing how to set up policy info in Defender for Cloud Apps]()
- Step 5. Next, make any adjustments to the query for matching applications.
![Screenshot showing how to adjust a policy]()
- Step 6. Set a trigger for the policy.
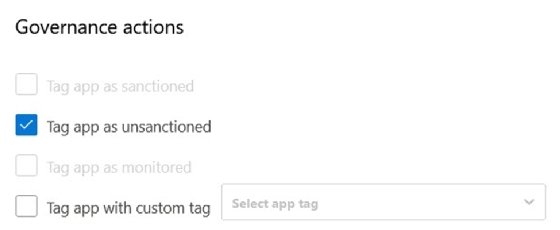
- Step 7. Finally, set the alerts and governance actions.
![Screenshot showing how to set alerts and actions in Defender for Cloud Apps]()
Once you enable the policy, Defender for Cloud Apps begins monitoring the selected cloud applications for any unsanctioned usage that violates the policy. You'll receive alerts and notifications when the tool detects this activity, enabling you to investigate and take appropriate action to mitigate any risks or security threats.