How can you deal with all the new macOS security controls?
How to deal with KEXT whitelisting and TCC controls, and how to stay up to date on the latest developments.
We have been conditioned for years, hearing “Windows is a death trap—but macOS never gets viruses, malware, or spyware, and nothing bad could ever possibly happen to it!”
The reality is that for a long time, macOS benefited from its low market share, as this made it less of a target for bad actors. However, the landscape has since changed, and the enterprise footprint is bigger. A few examples of this is are IBM’s Employee Choice program (which allow people to decide if they want to use a Mac or PC), cheaper options for Macs, and third-party vendors that are investing more resources into delivering their apps on all platforms.
With the increased enterprise adoption, Macs are being targeted at higher rates than ever before. Apple has continued to realize this, and over the last few years, has started to address the problem. As a mobility or unified endpoint management (UEM) engineer, the challenge is trying to account for these changes. We need to look at things in three stages:
- Be aware of what is coming out in each macOS patch.
- Identify new behaviors that affect user experience.
- Implement scripts or MDM payloads to make the new behaviors transparent.
Keeping up to date on patch and release information
Sometimes it can be challenging to keep up with the release schedule or know to what is coming with each patch. Here are my recommendations:
Apple Listserv
You can sign up for the Apple Listserv here. Specifically, sign up for the security updates on their main page, and you will get their security release notes when new versions come. The Listserv is a well-kept secret, but it has been a godsend to me multiple times over the years.
Apple public beta
Shortly after the yearly Worldwide Developer Conference, Apple releases the latest macOS beta. This obviously provides you with a nice preview into what’s coming, so go to beta.apple.com to sign up for the public beta. However, I cannot stress enough that you should never use your regular Mac to test betas, as that tends to put you in a bad spot eventually.
RSS feeds
It never ceases to amaze me that people forget how awesome a good RSS feed application is. My favorite one is Feedly, but there are many options like Apple News, Newsblur, Feedbin, etc. My recipe for being aware and proactive is to follow MacRumors, BGR, and 9to5Mac.
UX behaviors in High Sierra and Mojave and how to fix them
We have found a few new challenging behaviors in High Sierra and Mojave. The key ones we are focusing on are Kernel Extension (KEXT) whitelisting and the new Mojave controls for Transparency, Consent, and Control (TCC).
With any changes, it’s very important to understand what your users are seeing. The first thing that I teach anyone is to “understand how things work from A to B,” similar to understanding data flow from client to server.
Automating kernel extension whitelisting and providing a clean experience
You can read about KEXTs here, but simply put, some applications like antivirus or VPNs need to stretch the limits of the operating system.
You need to do three things to make your KEXT management transparent: Approve your MDM profile, find the KEXT IDs, and push the KEXT MDM payload. This is much easier than you think it might be.
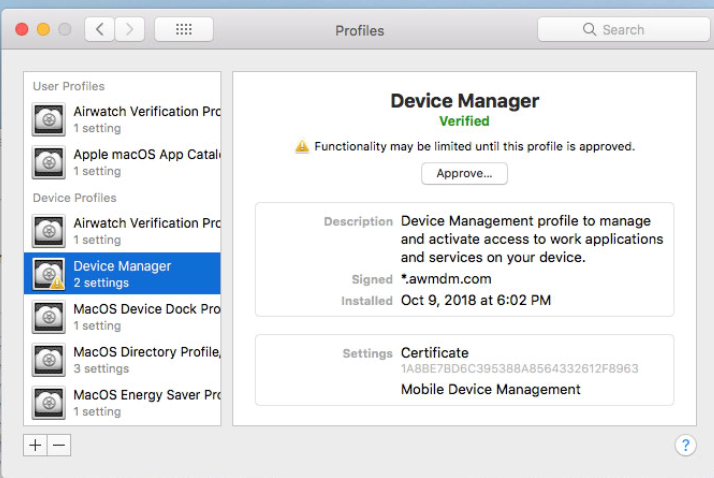
Approval is pretty easy. I’m not going to explain it in depth, but basically, if the device wasn’t enrolled via DEP, you need to click “Approve” like you can see below. This will allow you to whitelist the KEXTs.
Next, you need to find out what KEXTs you actually have on your machine. Simply run this command:
sqlite3 /var/db/SystemPolicyConfiguration/KextPolicy
You will see output like the following. The part before the vertical pipe is the Team ID, and the part after it is the App ID.
EQHXZ8M8AV|com.google.dfsfuse.filesystems.dfsfuse|1|Google, Inc.|8
Lastly, you need to make a profile and distribute it. You can go to my Github page for an example of an MDM payload that says to whitelist some Team IDs and App IDs. Once you follow these steps, you have solved this big hurdle in High Sierra seamlessly.
Automating TCC in Mojave and reducing user headaches
One of the big disappointments I ran into when I upgraded to Mojave was seeing these annoying pop-ups almost instantly:
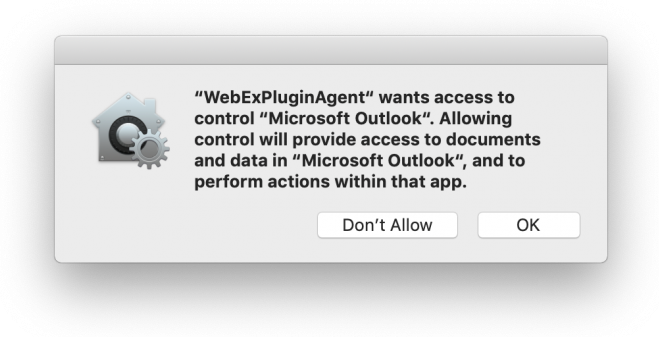
With TCC, you need to whitelist application attempts to access data in certain stock apps like Finder, Contacts, Calendar, etc. TCC also impacts your ability to allow an application like WebEx to grant remote control of your Mac to another user.
The Mojave controls are under the Security & Privacy system preferences.
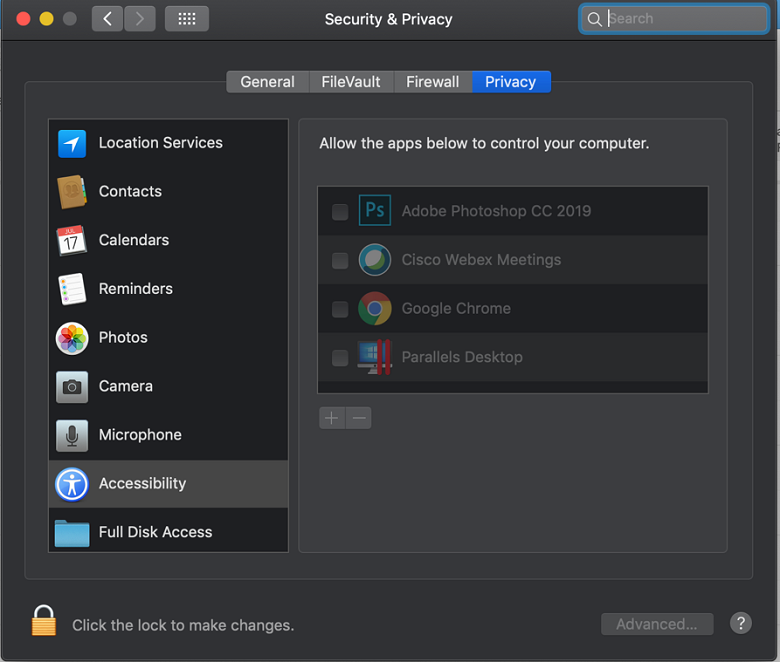
I’ve put together the AirWatch profile for standard AW Agent and Outlook functionality, as well one for WebEx Remote Control, as they can be relatively challenging to work with.
There are many other TCC controls that enable you to grant permission for third-party apps to access macOS apps, including the examples listed below.
- Address Book
- Calendar
- Reminders
- Photos
- Camera (Can only be denied)
- Microphone (Can only be denied)
- Accessibility
- PostEvent
- SystemPolicyAllFiles
- SystemPolicySysAdminFiles
- AppleEvents
These are not without their challenges, but I’m happy to share my experiences and guidance—click on my contributor profile for my contact info if you need further help.
In closing
Thanks to MDM APIs in macOS and Windows 10, we’re seeing what I believe is a revolution with the birth of unified endpoint management. Many people are starting to manage Macs with UEM, and getting rid of dedicated management platforms like Jamf. [Editor’s note: It looks like we’re all set up for a debate on this one.] As mobility engineers, many of us are now managing platforms like macOS and Windows 10 for the first time. There will be many lessons learned on the road to unified endpoint management, and this is just the beginning.







