
iQoncept - Fotolia
Compliance automation prevents regulation audit snafus
Many IT organizations address compliance issues manually, even though Puppet, Fugue and other tools can enforce configurations that comply with regulations and even provide an audit trail.
While IT organizations are catching on to the benefits of infrastructure as code, the majority haven't achieved compliance automation, despite a swath of available tools for the job.
IT automation software and tool pipelines help programmatically build code and integrate software. They also configure and deploy virtual infrastructure. Infrastructure as code exploits the inherent programmability and malleability of virtual servers, storage and networks -- also known as software-defined infrastructure -- to increase operational efficiency, repeatability and agility.
When virtual infrastructure configuration and deployment specifications are encapsulated as just another piece of code, it enables more than mere process automation. IT organizations can subject infrastructure as code to the gamut of software development best practices, including automated code validation, policy or usage enforcement, and security checks to infrastructure configurations.
In 2017, configuration management company Chef polled more than 640 IT professionals on compliance practices, concerns and problem resolution practices. Chef's compliance automation software, InSpec, makes the vendor an interested party in the area, but the results of the poll coordinated with data on other areas of enterprise IT and illuminated the state of compliance governance and automation in most organizations.
Of organizations polled, 74% use manual processes to assess software for compliance with internal standards. When they detect violations or security vulnerabilities, half of respondents fix the problem manually, which makes compliance problem resolution take days or even weeks. Slightly more than half of the organizations that use compliance automation software are still early in their deployment: These practices only cover a quarter of their systems.
Most organizations have yet to consider the benefits or capabilities of compliance automation software, and furthermore, that automating configuration, security and regulatory policies for compliance is just the beginning of many DevOps approaches to IT management. There's no lack of tools to support compliance automation, but they primarily appeal to organizations that already automate software development, systems integration, infrastructure deployment and other DevOps processes via pipelines.
A selection of compliance automation tools
Organizations should evaluate compliance automation software as part of a move to infrastructure as code and DevOps. These tools share common capabilities, with differentiating features.
Chef InSpec. The relative youth of compliance automation is shown in that the most mature tool for compliance automation tools is less than three years old. InSpec debuted in 2016 as a tool for code testing, infrastructure and application verification, and compliance analysis. InSpec turns compliance policies and test procedures into Ruby-based code. It has an active community on GitHub that improves the core product and its utility through compliance profile development.
Profiles are sets of tests that use rules or configuration assertions pulled from the appropriate compliance document. For example, the InSpec community has developed a lengthy profile based on Center for Internet Security (CIS) benchmarks that others have modified to meet the standards within a particular company or industry, such as financial services. InSpec produces compliance reports accessible from a central management dashboard.
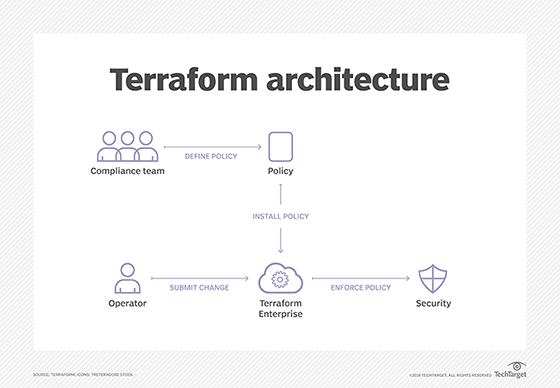
InSpec typically runs from a central server against multiple remote systems, such as VM instances on AWS, Microsoft Azure or a VMware vSphere environment, and can be incorporated into automated deployment and configuration systems, such as Chef Automate or HashiCorp Terraform, to ensure complete coverage of systems and applications within an organization.
InSpec is available for all major Linux versions, along with FreeBSD, macOS, Windows -- which requires PowerShell -- IBM AIX, HP-UX and Oracle Solaris.
Red Hat Ansible. Ansible is a popular alternative to Chef for system configuration and deployment automation and can also validate compliance if an organization runs standard Ansible playbooks against systems in check, but don't change mode via the -check flag. The result is a list of any changes that Ansible would make to bring the target system into compliance with the playbook, which should be written to adhere to the organization's requirements. Ansible also runs checks on applications. For example, Ansible can query if the correct processes take place, whether any unneeded network ports are open or if the application returns the correct response to a particular operation or query.
Administrators can use Ansible to install the system and application via a playbook. Should problems arise, the admin merely reruns the relevant playbook without the -check flag. Ansible can also detect configuration drift with its scheduler and recheck and reapply standard playbooks at regular intervals.
Puppet. Admins can configure Puppet for compliance automation, wherein the tool continually monitors for relevant configuration policies and automatically triggers requisite changes to bring out-of-spec systems back into line. Puppet uses a set of manifests that describe a system's desired state instead of the particular steps to configure it. The system manifest should reflect security, configuration and other standards so that, when Puppet rescans a system, it can automatically bring it back into compliance with its original, compliant manifest.
Puppet specifies resources, their desired condition and dependencies, so the manifest and resource catalog are simultaneously automation instructions and a compliance document suitable for audits. When a Puppet manifest describes an ideal system compliant with relevant regulations, security policies and internal best practices, it becomes the standard against which operational systems are measured for compliance, as well as the vehicle by which Puppet fixes noncompliant systems.
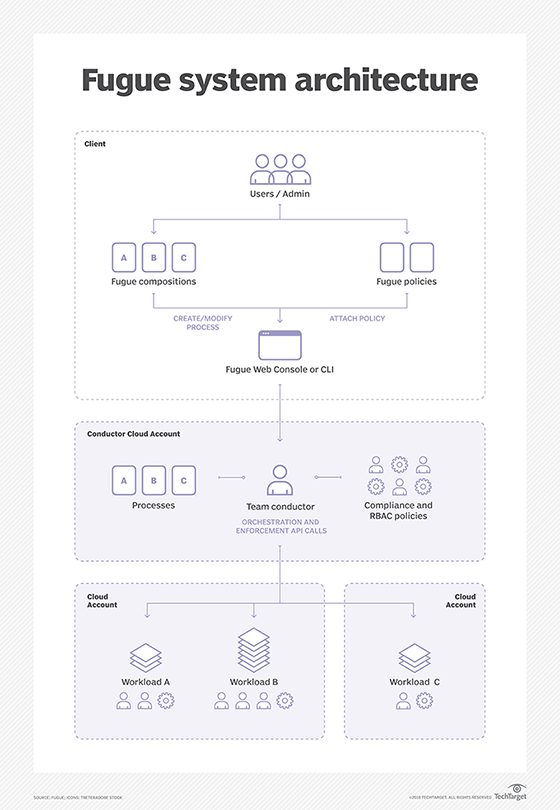
Fugue. Fugue is a startup founded in 2013 as Luminal to automate AWS deployments but then pivoted to compliance automation and service management. Similar to Puppet, Fugue provisions systems in accordance with documented policies and standards from master code that describes the ideal configuration.
Fugue configurations are built in a proprietary domain-specific language called Ludwig. At time of publication, Fugue only works with AWS resources but plans to expand services to other cloud platforms and APIs.
Compliance automation recommendations
To automate system and application compliance with established standards and regulations presupposes the use of configuration management and infrastructure as code software. Incorporate standardization and audited compliance in the evaluation, testing and eventual rollout of an infrastructure as code system; don't attempt to apply them after the fact.
Use cases for compliance automation vary by organization, but the need is most acute in highly regulated industries, such as healthcare. Compliance automation helps ensure that only approved system images deploy, containing the latest patches and secure configuration. After deployment, compliance automation software can scan systems regularly to identify and fix those that drift from approved configurations and create audit reports to document compliance with various standards, such as CIS.







