
adimas - Fotolia
New spear phishing campaign targets oil and gas industry
Bitdefender researchers identified new spear phishing campaigns against the oil and gas industry that include emails with no typos and perfect usage of industry terminology.
What if there was a phishing email that even the most prepared user could fall for?
Researchers at antimalware vendor Bitdefender identified new spear phishing campaigns against the oil and gas industry that include emails with no typos, perfect usage of industry terminology and references to real industry events. The malware contained in both campaigns is the Agent Tesla spyware Trojan.
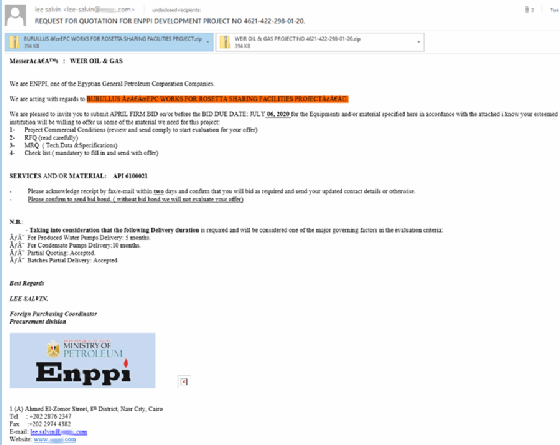
The campaigns impersonate either a well-known Egyptian engineering contractor, Enppi, or an unnamed shipment company. The Bitdefender report stated that the largest number of malicious reports, or detections of the malware, came from the U.S., Malaysia and Iran. The day with the most reports was March 31, totaling at 107.
"The impersonated engineering contractor … has experience in onshore and offshore projects in oil and gas, with attackers abusing its reputation to target the energy industry in Malaysia, the United States, Iran, South Africa, Oman and Turkey, among others, based on Bitdefender telemetry," the Bitdefender report said. "The second campaign, impersonating the shipment company, used legitimate information about a chemical/oil tanker, plus industry jargon, to make the email believable when targeting victims from the Philippines."
Liviu Arsene, global cybersecurity analyst for Bitdefender as well as the author of the report, told SearchSecurity the oil and gas campaigns were most likely so well-executed for one of two reasons.
"It could be that someone had some background in the industry, but the way these cybercriminal organizations operate is they have various individuals with various talents," Arsene said. "So they either use knowledge from individuals that have previously successfully breached oil and gas companies and they can leverage on that past experience and jargon, or they simply managed to monitor the communication between someone who works in oil and gas and another individual that they're in interaction with."
The campaigns come at a time when the COVID-19 pandemic has lowered oil prices severely in recent weeks. "However," the Bitdefender article notes, "a disruptive dispute over oil production between Russia and Saudi Arabia ended with an agreement at the recent meeting between the OPEC+ alliance and the Group of 20 nations, aiming to slash oil production output and balance prices."
The Agent Tesla spyware is notable because unlike the expertly designed email campaigns the malware is attached to, it's not the most sophisticated or complex piece of malware in the wild. But using a common and relatively simple type of malware has its advantages, Arsene said.
"It's something that you can get off the dark web and you don't have to customize it in any way," he said. "It makes it easier to deploy, so it makes attribution a lot more difficult. It's not something custom you can attribute to state-sponsored actors or a cybercriminal group, so that makes it difficult during an investigation to find out what was the actual goal."
Bitdefender did not attribute the spear phishing campaigns to any particular APT group or nation, though the report did say the likely motive was intelligence gathering to see how certain nations were handling the falling price of oil. Regardless of the motive, Arsene said there are likely to be similar campaigns as the year progresses.
"Whether the attackers are state-sponsored or advanced groups, I think the ultimate goal remains the same, which is to cover their tracks using known, existing infrastructure that has been proven to work to carry out their own agenda, specific agenda. I think this is something we're going to be seeing a lot this year."





