
New vulnerability rating framework aims to fill in CVSS gaps
The CVSS vulnerability scale doesn't always give a clear picture of the risk of a vulnerability, but experts hope the emerging standard called EPSS will provide more clarity.
Every week, administrators around the world use the ratings from the Common Vulnerability Scoring System, or CVSS, to decide what patches and vulnerabilities should be a priority for testing and installation on their managed systems.
Organizations such as the Mitre Crop. and the National Institute of Standards and Technology assign vulnerabilities a CVSS number ranging from 1-10 based on a number of criteria, including the extent of access a vulnerability allows, how it can be targeted and what the complexity of a potential exploit would entail. The most serious of the vulnerabilities, remote access without authentication, can often achieve scores higher than 9.
While the CVSS scale has proven to be a useful tool for assessing the potential risk a vulnerability could pose in the wild, experts have long said the open source framework has its shortcomings, and a recently created system is carrying hope for giving admins a better idea of what flaws they need to patch and when.
Introduced in 2005, CVSS was created for a much different threat landscape. With the flow of CVE-listed bugs still modest, the idea of getting patches installed at their release or shortly after was still a realistic prospect for many administrators.
In the 17 years since, however, the number of vulnerabilities being reported has skyrocketed, while attacks have grown and matured. Under these circumstances, simply having a CVSS no longer gives administrators enough information about what is and is not a serious threat.
Most notably, experts say, CVSS displays only the severity of the flaw, not the real-world danger of an attack. For example, a vulnerability with a CVSS score of 9.8 would be seen as the top priority for patching, despite a vulnerability with a score 6.4 being actively exploited in the wild already.
Researchers have found that in many cases, relying solely on CVSS can place networks at risk.
"In the 2000s things were different, we were all very naïve," said Sasha Romanosky, one of the co-authors of the CVSS framework and a senior policy researcher at RAND Corporation. "Nation-state actors and APTs were not really a thing. We figured naively that could capture risk."
To better help defenders manage the deluge of vulnerability reports and increasingly nefarious attackers, Romanosky and others decided a new framework was needed.
Enter EPSS
At the 2019 Black Hat conference, Romanosky joined a team of experts from the Cyentia Institute, Kenna Security and Virginia Tech University in releasing their design for a new framework that would be able to help defenders gauge the risk a given bug poses for imminent exploitation in the wild.
Known as the Exploit Prediction Scoring System (EPSS) the new framework seeks to use real-world analysis of traffic and logs to help assign a risk rating for vulnerabilities as they are disclosed. The formula seeks to assign each CVE-listed flaw value between 0-1 representing the probably that it will be subject to attack.
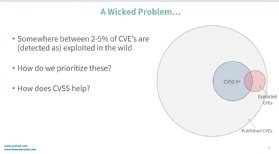
"CVSS only describes the vulnerability using six (in the base case) metrics, but EPSS gathers dozens of variables and runs them through a model to see if that variable is indicative of the vulnerability actually being used to exploit a machine," Michael Roytman, Kenna Security chief data scientist and EPSS co-author, told SearchSecurity in an email.
"Think of this as the difference between what could happen (CVSS) and what is likely to happen (EPSS)."
Jay Jacobs, Cytentia co-founder and one of the authors of the EPSS proposal, said that the sheer volume of data being collected by modern enterprise security providers, such as Cisco's Kenna Security, is key to the framework. By looking at the traffic logs and incident reports created by thousands of companies around the planet, it becomes possible to gauge what flaws are in the cross-hairs of criminals and predict which CVEs are most likely to be targeted.
"We had access to a lot of data about vulnerabilities," Jacobs told SearchSecurity. "It opened up so many interesting things, we could take a look at vulnerabilities that were in corporate environments."
A supplement, not a replacement
One thing that the EPSS authors have stressed is that the framework is not designed to serve as a wholesale replacement for the CVSS format. The framework only gauges one specific risk factor -- exploit likelihood -- associated with a given CVE entry.
Rather, they hope that EPSS scores can be used alongside those of CVSS to help administrators sort out which patches should be top priorities based on the likelihood of attack, and which can be addressed later as they are probably not going to face immediate exploits.
"It is based on probability, and probability is a confusing concept," Jacobs explained. "I hope people treat it like a support mechanism, not a decision direction."
The coming months are shaping up to be critical for EPSS and its backers. The project has been entrusted to the Forum of Incident Response and Security Teams or FIRST, an industry organization formed in 1990 that oversees the CVSS framework. EPSS is tentatively set to debut around the end of February if all goes well.
That first major release will also include APIs that will bring what EPSS' creators hope will be a deluge of data from users and vendors. Unlike other projects that can become overwhelmed and bogged down with large amounts of data, the EPSS framework was created to become more effective as hundreds of contributing vendors and organizations feed in their own attack data.
"I would encourage other security vendors -- particularly the vulnerability scanning and endpoint security technologies -- to contribute their data to the effort as well," Roytman said.
"In a world where data is necessary to maintain the security of our most valuable digital resources, we as vendors should all be contributing data to help increase the effectiveness of open source projects like EPSS."







