Common Vulnerability Scoring System (CVSS)
What is the Common Vulnerability Scoring System (CVSS)?
The Common Vulnerability Scoring System (CVSS) is a public framework for rating the severity and characteristics of security vulnerabilities in information systems. It provides a numerical score ranging from 0 to 10 to indicate the severity of a vulnerability, with 10 being the most severe.
CVSS is vendor-neutral, enabling an organization to score its IT vulnerabilities across a wide range of software products -- from operating systems and databases to web applications -- using the same scoring framework.
The CVSS framework is maintained by the Forum of Incident Response and Security Teams (FIRST), a global nonprofit organization consisting of more than 500 members.
Who should use CVSS?
IT managers and information security teams commonly use CVSS as part of a vulnerability management program to provide a point of comparison between vulnerabilities and to prioritize their remediation. Application vendors and security vendors also use CVSS to prioritize security tests or to ensure that known vulnerabilities are removed during development. CVSS has been adopted by organizations, industries and government groups, such as the Department of Homeland Security's (DHS) Cybersecurity and Infrastructure Security Agency. Vendors such as Cisco, Oracle, Qualsys and SAP also generate CVSS scores to communicate the severity of vulnerabilities found in their products. CVSS can also be used by organizations to prioritize responses within their environments.
Why do organizations adopt CVSS?
Historically, vendors used their own methods for scoring software vulnerabilities, often without detailing how their scores were calculated. This created a conundrum for systems admins: Should they fix a vulnerability with a severity of high first or one with a severity rating of five?
To address this problem, CVSS simplifies the generation of consistent scores that reflect the severity and effects of vulnerabilities in an IT environment. CVSS also provides the following:
- Establishes an open framework. Organizations have full access to the CVSS parameters used to generate scores, providing everyone with a clear understanding of the rationale and differences behind any vulnerability scores. This makes it easier for security teams to gauge the effect of the vulnerabilities on their systems and prioritize which vulnerabilities to fix first.
- Mitigates vulnerabilities in development. Software developers can use CVSS scores to prioritize security tests and ensure known and serious vulnerabilities are removed or mitigated during development.
- Meets security standards. CVSS can help organizations meet the security requirements of various standards. For example, the presence of unpatched vulnerabilities with a CVSS score of four or higher has an adverse effect on Payment Card Industry Data Security Standard compliance.
- Promotes consistent and transparent communication. The goal of developing CVSS is to encourage clear and consistent communication. It provides organizations with a transparent and standardized way to communicate the seriousness of vulnerabilities, enabling them to prioritize the most important ones.
History of CVSS
The U.S. National Infrastructure Advisory Council (NIAC) first introduced CVSS in 2005, but FIRST now owns and manages it. NIAC developed CVSS to simplify the generation of consistent scores that could accurately reflect the existing security risks and vulnerabilities in a specific IT environment.
FIRST sponsors and supports the CVSS Special Interest Group (SIG), which is made up of various organizations and individuals who help promote and refine the framework.
The CVSS SIG provided most of the research and feedback on the initial design of CVSS and helped test and refine the formulas used in later versions.
CVSS versions
CVSS v2 was released in 2007 and was seen as a significant improvement over the original version. It had fewer inconsistencies, provided additional granularity and more accurately reflected the true properties of IT vulnerabilities, despite the wide variety of vulnerable systems and types.
CVSS 3.0, released in June 2015, introduced scoring changes that more accurately reflected the reality of vulnerabilities encountered in the wild. For example, the update introduced changes such as the privileges required to successfully exploit a vulnerability and the opportunities it gives a cyberattacker who successfully uses it.
CVSS version 3.1 was released in June 2019. The changes in this version focused on clarifying and improving the standard. This version doesn't create any new CVSS metrics or metric values and doesn't make major changes to the formulas.
The most recent version is 4.0 which was released on Nov. 1, 2023, and provides various improvements, including the following:
- Finer granularity in base metrics.
- Removal of downstream scoring ambiguity.
- Simplification of threat metrics and improved scoring effect.
- Supplemental attributes for vulnerability response.
- Additional applicability to operational technology, industrial control systems and internet of things devices.
Vulnerability metrics
CVSS scores are calculated using a formula consisting of vulnerability-based metrics. A CVSS score is derived from scores in these three metric groups: Base, Temporal and Environmental. Scores range from 0 to 10, with zero representing the least severe and 10 representing the most severe.
Together, these metric groups cover the different characteristics of a vulnerability, including its effect and environmental endurance over time.
Base metrics
The Base score is the metric enterprises rely upon most. It deals with the inherent characteristics of a vulnerability -- that is, the ones that don't change over time or due to a user's environment. Public severity rankings, such as those found in the National Institute of Standards and Technology (NIST) and National Vulnerability Database, exclusively pertain to Base CVSS scores.
It's made up of the following two sets of metrics:
- Exploitability metrics, which include the following:
- Attack vector.
- Attack complexity.
- Privileges required.
- User interaction.
- Impact metrics, which include the following:
- Confidentiality impact.
- Integrity impact.
- Availability impact.
Temporal metrics
The Temporal score measures aspects of the vulnerability according to its current status. It represents properties of a vulnerability that can change over time, such as the release of an official patch.
Temporal scoring also includes the Report Confidence metric, which measures the following:
- The degree of confidence in the existence of the vulnerability.
- The credibility of the known technical details demonstrating that a vulnerability is both real and exploitable.
These metrics can decrease or increase the Base score; for example, if a patch or workaround becomes available or the vendor validates a vulnerability.
Temporal values include the following:
- Exploit code maturity.
- Remediation level.
- Report confidence.
Environmental metrics
The CVSS system's Environmental metrics let an organization refine the Base score to reflect its own environment by measuring the severity of the vulnerability. This score can be adjusted for its effect on individual systems.
Environmental metrics provide real context for vulnerabilities within an organization by considering the following factors:
- Business criticality of the asset.
- Identification of mitigating controls.
- Use of the asset in question.
The list of Environmental metric categories consists of the following:
- Collateral damage potential.
- Target distribution.
- Confidentiality requirement.
- Integrity requirement.
- Availability requirement.
How CVSS scoring works
A CVSS score can be between 0 and 10, with 10 being the most severe. To help convey CVSS scores to less technical stakeholders, FIRST maps CVSS scores to the qualitative ratings in the following image:
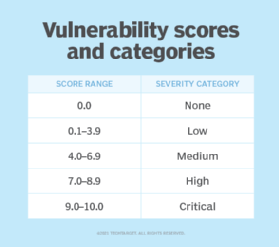
The following points are involved in calculating a CVSS score:
- Various score subgroups are combined to produce the CVSS score.
- The Base score is mandatory, while the Temporal score is optional and both are provided by the vendor or analyst.
- The end user calculates the Environmental group score, which is also optional.
- The only requirement for categorizing a vulnerability with a CVSS score is the completion of the Base score components: the Exploitability subscore, the Impact subscore and the Scope subscore. These scores are used to calculate the overall Base score using a formula that weights each subscore.
- The Temporal score is calculated by multiplying the Base score by the three metrics within the Temporal metric.
- The Environmental score is a more complex calculation. The end user recomputes the Base and Temporal scores using the five Environmental metrics to give a more accurate evaluation of the severity of a vulnerability.
CVSS vs. CVE
Common Vulnerabilities and Exposures (CVE) is a catalog of known security threats and each entry in that catalog has a corresponding CVSS score. It divides threats into two categories: vulnerabilities and exposures. The catalog, which is sponsored by DHS, is designed to standardize the way each known vulnerability or exposure is identified.
While CVE is a list of all disclosed vulnerabilities, CVSS is an overall score assigned to a vulnerability. Every CVE entry includes a unique identifier, as listed in the NIST National Vulnerability Database.
CVE identifiers are formatted as follows:
CVE-[Four-Digit Year]-[Sequential Identifier]
For example, the CVE identifier for the Heartbleed vulnerability is CVE-2014-0160, and the CVE identifier for the Log4j vulnerability is CVE-2021-44228.
CVE uses CVSS to indicate the severity of each CVE. For each CVE vulnerability, FIRST provides qualitative ratings based on the CVSS Base score.
CVSS calculators
A CVSS calculator is necessary to calculate the Temporal and Environmental scores for an organization's own environment. FIRST, NIST and Cisco provide free CVSS calculators.
For example, FIRST's CVSS v3.1 calculator gives a score for each Base, Temporal and Environmental metric. To use the calculator, the end user selects one option from each provided category. For example, the Base score is calculated using metrics such as the following:
- Attack vector: Network, adjacent, local or physical.
- Attack complexity: Low or high.
- Privileges required: None, low or high.
- User interaction: None or required.
- Scope: Unchanged or changed.
- Confidentiality: None, low or high.
- Integrity: None, low or high.
- Availability: None, low or high.
Limitations of CVSS
CVSS is valuable in standardizing vulnerability assessments. However, it does come with some limitations including the following:
- Subjectivity. CVSS scores can fluctuate based on the particular context and environment being used for the evaluation of a vulnerability. This can result in subjective and irregular scoring patterns.
- Limited scope. CVSS fails to provide a thorough evaluation of the potential effect of vulnerabilities on an organization. For example, it might not take into account things such as the importance of assets to company operations, whether any types of cybersecurity controls are in place and how the item in question is specifically used.
- Complexity. While CVSS provides a standardized and objective method for assessing the severity of vulnerabilities, it can be complicated and necessitate a thorough comprehension of the scoring factors and their implications.
- Can cause oversights. Since CVSS scores can be found in several publicly accessible databases, many security teams start by looking through these sources when determining which vulnerabilities to prioritize and how to fix them. However, solely relying on these sources neglects real-world exploits and available mitigation options, which can lead to significant oversights.
Learn three additional steps for ranking enterprise network security vulnerabilities.



