What is the Mitre ATT&CK framework?
The Mitre ATT&CK framework is a free, globally accessible knowledge base that describes the latest behaviors and tactics of cyberadversaries to help organizations strengthen their cybersecurity strategies. The acronym ATT&CK stands for Adversarial Tactics, Techniques and Common Knowledge. That's the basis for the Mitre ATT&CK -- pronounced miter attack -- framework and its accompanying ATT&CK knowledge base.
The framework is used across multiple fields and disciplines, including intrusion detection systems, threat hunting, red teaming, security engineering, threat intelligence and risk management.
Organizations can use the framework to evaluate and test their security methods and to vet cybersecurity vendor products and services. Security vendors use Mitre ATT&CK to ensure their offerings make defending against and responding to security events faster and more effective.
Components of the Mitre ATT&CK framework
Mitre Corp., a not-for-profit security research organization, created and continues to curate the ATT&CK framework and cyberthreat intelligence knowledge base. The knowledge base contains analyses based on real-world events that organizations can reference when developing threat models and methodologies. It grows, and thus informs the framework, as organizations contribute cyberthreat knowledge. Mitre aims to foster a stronger overall cybersecurity community with these free offerings.
Mitre has established three iterations of the ATT&CK framework:
- ATT&CK for Enterprise. Addresses threat behavior in Windows, Mac, Linux and cloud environments.
- ATT&CK for Mobile Environments. Addresses threat behavior for mobile devices using iOS and Android operating systems.
- ATT&CK for Industrial Control Systems. Addresses threat behavior that impacts industrial control systems.
The framework evaluation criteria are specific to each organization using it and focus on the details of an organization's cybersecurity approach. The results of the evaluations are noncompetitive; organizations can't use results to gain a business advantage over other organizations that have been evaluated.
Tactics and techniques in the ATT&CK framework
Tactics and techniques are Mitre's two different ways of categorizing adversarial behavior. By Mitre's definition, an ATT&CK technique describes how adversaries achieve their objective and, in some cases, what they gain from achieving that objective. An ATT&CK tactic describes the objective, or reason, for performing the attack.
Techniques show the information that attackers are after and how they go about getting it. Tactics explain why they want it. Multiple techniques can be used to achieve a tactical objective.
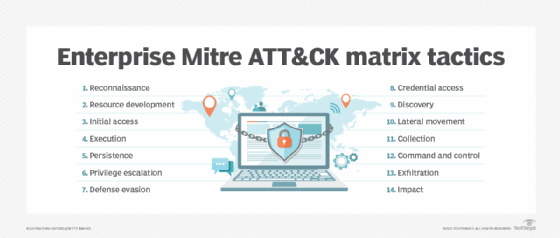
The following 14 tactics are included in the enterprise Mitre ATT&CK matrix:
- Reconnaissance. Adversaries find possible weak points and targets by learning as much as possible about the target.
- Resource development. Adversaries acquire resources, such as infrastructure or tools, to support their operations.
- Initial access. Adversaries gain an initial foothold in the target environment by using techniques such as spear phishing or exploiting vulnerabilities.
- Execution. To accomplish their goals, adversaries use malicious code or commands on compromised systems.
- Persistence. Adversaries establish ways to continue to access compromised systems even after a reboot or remediation attempts.
- Privilege escalation. Adversaries gain higher levels of access or privileges within the target environment.
- Defense evasion. To avoid detection, adversaries employ techniques to bypass and get around security systems.
- Credential access. Adversaries steal credentials or obtain legitimate credentials to gain unauthorized access to systems or accounts.
- Discovery. Adversaries explore the target environment to collect information regarding the network, systems and user accounts.
- Lateral movement. Adversaries move laterally within the network to expand their reach and access additional systems.
- Collection. Adversaries gather data or information from compromised systems, including sensitive files and credentials.
- Command and control. Adversaries create communication channels between compromised systems and their controlled external entities.
- Exfiltration. Adversaries steal or move data from the target environment to external locations or systems.
- Impact. Adversaries disrupt, modify or destroy systems or data within the target environment.
The main objective of the ATT&CK Matrix is to provide organizations with a deeper understanding of potential threat actors and to help them formulate more thorough defense strategies over attack lifecycles.
A visualization of the relationship between attacker tactics and attacker techniques is shown as a large table on the Mitre ATT&CK website. Each tactic or technique is clickable and leads to more detailed explanations of the term. An organization can use this matrix to pinpoint the exact adversarial behavior it wants to learn more about for defense purposes.
Because multiple techniques can be used to achieve a given outcome, the ATT&CK Enterprise Matrix includes multiple techniques in each tactic category. Currently there are 202 techniques and 435 subtechniques in the ATT&CK enterprise framework. The tactics are listed on the x-axis and the techniques are listed on the y-axis.
For example, if a user clicks on the "Initial Access" tactic, they're presented with 10 techniques and their descriptions. The first three items on the list are "Content Injection," "Drive-by Compromise" and "Exploit Public-Facing Application." If the user clicks on "Content Injection," they're taken to a page that describes the attack in more detail, provides procedure examples and lists subtechniques.
Mitre ATT&CK use cases
The Mitre framework has several use cases that make it compelling for organizations as well as managed security service providers and manufacturers of cybersecurity systems and software. Common use cases of the framework include the following:
- Penetration testing. With pen testing, organizations designate a red team to simulate behavior and find vulnerabilities. Pen testers can use Mitre to learn how to simulate behaviors and help them develop accurate defenses.
- Red teaming. When preparing a red team assessment, the ATT&CK framework can help ensure that specific issues aren't overlooked and identify attack vectors that might be in scope for the assessment.
- Cybersecurity service evaluation. Cybersecurity vendors use Mitre's evaluations to determine the strength of their products and services. The evaluations provide objective insights into the use of specific commercial security products and offer a transparent analysis of a product's capabilities. They also strengthen the cybersecurity community as a whole by encouraging vendors that develop products responsible for customer security across many industries.
- Cybersecurity gap assessments. Mitre ATT&CK identifies which parts of an enterprise have defense issues and lack visibility. Organizations can use it to test prospective tools before making a purchase and evaluate their existing ones.
- Behavior analytics. The framework can be used for user behavior analytics, as it provides a comprehensive knowledge base of tactics, techniques and procedures that adversaries use during the different phases of the cyberattack lifecycle. For example, the ATT&CK framework includes techniques related to lateral movement, credential access and privilege escalation, which adversaries commonly use. By keeping an eye out for these types of activities, organizations can detect potential security threats and take necessary precautions to mitigate them.
- Prioritization of detection efforts. Security teams can use the ATT&CK framework as a roadmap to determine where to focus their detection efforts. For instance, some teams opt to prioritize threats that occur earlier in the attack chain, whereas others focus on the techniques attacker groups use.
- Security operations center maturity assessment. Similar to gap assessment, organizations can use Mitre ATT&CK to determine how effective a SOC is at detecting, analyzing and responding to breaches.
Benefits of the Mitre ATT&CK framework
The benefits of the Mitre framework include the following:
- It offers a concrete account of adversarial behaviors.
- The framework provides an account of threat indicators as well as threat groups. Businesses can use Mitre to detect behaviors, make educated guesses about who is performing them and track behaviors across different attacker groups. Its attack page features group-based information.
- It includes sector-specific threat information that's used and trusted across many industries.
- It provides a communal approach to threat reporting that ensures information is up to date and checked by the public as well as Mitre.
- Using the framework improves an organization's security posture as it aligns its security strategies with the tactics and techniques outlined in the framework.
The framework enables a business to do the following:
- Associate attack behavior to different groups.
- Pen test its network.
- Find vulnerabilities in its network and map ATT&CK methodologies to threats.
- Discover network misconfigurations.
- Share its cybersecurity knowledge with the broader community.
- Standardize disparate security tools and techniques to create a more cohesive security strategy.
How to use Mitre ATT&CK
There are several ways an organization can use Mitre ATT&CK to strengthen its cybersecurity strategies:
- Gain an understanding of the framework and the matrices that cover different attack environments, such as enterprise systems, cloud environments and mobile devices.
- Stay informed on attacker tactics and techniques using the threat matrix.
- Learn how to prep a network before any attack happens.
- Learn mitigation strategies after an attack.
- Share observations to improve overall community understanding.
- Evaluate cybersecurity products and services using Mitre's noncompetitive evaluation methodologies. This feature is mainly for cybersecurity vendors.
The key is understanding how to use the framework to maintain a high level of awareness of potential threats and how to respond to them.
Mitre ATT&CK vs. Cyber Kill Chain
Both the Cyber Kill Chain and Mitre ATT&CK are frameworks used in cybersecurity. However, their approaches, structures and points of emphasis are different.
Lockheed Martin developed the Cyber Kill Chain model in 2011. It outlines the stages of a cyberattack from initial reconnaissance to data exfiltration. The Cyber Kill Chain involves seven steps:
- Reconnaissance. Cyberattackers research and identify potential targets.
- Weaponization. Attackers create a backdoor to exploit a delivered payload.
- Delivery. Cybercriminals send the victim a weaponized bundle using a USB device, email or a website.
- Exploitation. Attackers take advantage of a vulnerability to run code on a victim's computer.
- Installation. Intruders install malware and other cyberweapons on the asset's network.
- Command and control. Cybercriminals communicate with their cyberweapons for remote manipulation.
- Actions on objectives. Intruders carry out their cyberattack objectives.
Mitre ATT&CK vs. NIST Cybersecurity Framework
The ATT&CK framework focuses on the methods adversaries use when preparing and delivering their attacks. The idea is to get into the mind of the attacker so that ideal preparations can be made to counter an attack. By contrast, the National Institute for Standards and Technology Cybersecurity Framework (NIST CSF) is a risk-based blueprint for government and nongovernment organizations to establish and maintain an optimum security posture.
Each framework has its own set of characteristics; Mitre ATT&CK has its tactics and techniques, and NIST CSF has a set of core functions. There's overlap across the two frameworks, but in practice they complement each other. NIST CSF provides the foundation for a secure cybersecurity governance structure, and Mitre ATT&CK provides the action-oriented guidance to prepare, protect and defend the organization from an attack. CSF provides the what and why behind the security strategy, while ATT&CK delivers the how-to tactics.
Mitre ATT&CK history
Mitre launched ATT&CK in 2013 to document common tactics, a common language, and techniques and procedures that advanced persistent threats used against Windows enterprise networks. Experiential data came from real-world observations.
ATT&CK began as an effort to gather this data for a research project on detecting threats in enterprise networks post-compromise, such as after adversaries had broken in. This was used to identify adversary techniques and from there to develop adversary emulation techniques.
Mitre's Fort Meade Experiment involved close observation of more than 200 hosts on a monitored network segment. It ran red team operations on this network, designating teams to act as attackers using known techniques to penetrate the network. A blue team then attempted to detect and mitigate these simulated attacks.
By simulating the complete cybersecurity landscape from both the attacker's and defender's perspective, Mitre formulated the following key insights that it uses as the basis of its ATT&CK framework:
- Focusing on adversarial behavior let it develop behavioral analytics and techniques for defense of systems and network security.
- Many existing cybersecurity lifecycle models were too abstract and unable to efficiently detect new threats.
- To work, threat behaviors and tactics must be based on real past observations of adversarial behavior, such as endpoint threats and ransomware attacks.
- Terminology for describing tactics must be consistent across different adversarial groups to enable businesses to compare and contrast them.
By applying these principles in a controlled research setting, Mitre verified it could improve the threat detection capabilities of networks in a measurable way. It also improved incident response.
In 2015, Mitre released the ATT&CK framework to the public. It has since expanded to include threats to macOS X, Linux and mobile device OSes.
In 2020, Mitre released its framework for industrial control systems, which can handle issues and challenges that are exclusive to industrial environments. These systems manage and control critical infrastructure, including manufacturing plants, power plants and other industrial activities.
Learn how to create a cybersecurity awareness training program that will equip employees with the knowledge and skills they need to help protect their organization from cyberattacks.







