EDR vs. XDR vs. MDR: Key differences and benefits
One of the most important goals of cybersecurity professionals is to quickly identify potential or in-progress cyberattacks. These three approaches can help.
Availability of detection and response resources is a key element in a cybersecurity professional's arsenal. Security teams take differing approaches to threat detection. This article compares and contrasts each technology and offers guidance on which approach(es) to use.
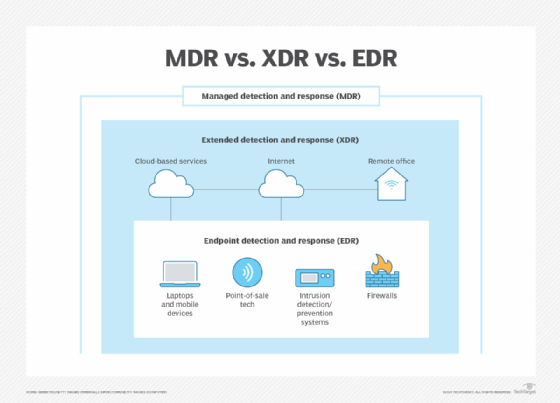
Endpoint detection and response (EDR) monitors the security of endpoints exclusively while extended detection and response (XDR) monitors endpoints plus other assets, like remote offices and IoT systems. Both EDR and XDR systems can be managed detection and response (MDR) systems, which are detection and response services provided by a third-party vendor.
More specifically:
- EDR is used to continuously monitor endpoints locally or in the cloud.
- MDR provides around-the-clock monitoring, threat detection, threat hunting, AI-based analysis, threat containment and elimination, all while providing reports on their activities.
- XDR platforms not only monitor all known points in an organization's digital landscape, but they also address cyberattacks in progress to stop or reduce the threat before it becomes a serious disruption.
Let's look at how these three are similar and how they differ.
What is endpoint detection and response (EDR)?
Endpoint detection and response involves devices typically located within an organization's four walls. EDR systems examine laptops, workstations, printers, network components and other information systems for suspicious activity.
EDR technology can identify suspicious behavior; use AI to analyze anomalies; and enable threat identification, triage, containment and elimination. EDR systems typically have dashboards to deliver threat status and performance information to security teams.
This article is part of
What is threat detection and response (TDR)? Complete guide
AI elements not only examine suspicious code from lists of thousands of threats, but they also use behavioral analytics to crunch vast amounts of data to identify possible similarities to known threats. Systems can then deliver guidance on how best to mitigate the threat, as well as proactively contain and eliminate the threat. Data captured during monitoring is processed and stored in databases for future use.
An important feature of EDR -- as well as XDR and MDR systems -- is threat hunting, which actively searches networks, devices, systems and other resources to identify potential threats. This capability greatly extends a cybersecurity team's capabilities in threat identification and management, helping to stay one step ahead of phishing, ransomware and other threats.
Similar to XDR, EDR systems automatically monitor, detect, analyze and mitigate security threats affecting endpoints. They initiate threat hunting, establish a proactive defensive posture, pull threat data into databases for future use, increase a security operations center's (SOC) capabilities and effectiveness, and provide actionable information for managing and resolving security incidents.
Vendors that provide EDR products include BlackBerry, Check Point, Cisco, CrowdStrike, Cybereason, Cynet, ESET, FireEye, IBM, Kaspersky, Malwarebytes, McAfee, Microsoft, Palo Alto Networks, SentinelOne, Sophos, Symantec (Broadcom), Trend Micro, VMware and WatchGuard.
What is managed detection and response (MDR)?
Attributes of EDR and XDR systems can also be delivered by third parties. These managed detection and response services supplement cybersecurity efforts by adding functions that might be beyond a particular team's capabilities. MDR can also be a single-point solution that addresses all aspects of cybersecurity management.
MDR providers offer an extensive suite of detection and response services. With access to those capabilities and expertise, an organization can bolster its security without needing to find and hire additional staff. Also, organizations with compliance requirements can benefit from an MDR vendor's expertise and ongoing reporting.
Vendors that provide MDR services include Alert Logic, CrowdStrike, Cynet, Cybereason, eSentire, Rapid7, SecurityHQ, Security Joes, SentinelOne and UnderDefense.
What is extended detection and response (XDR)?
When an organization needs threat monitoring, analysis and mitigation beyond endpoints, extended detection and response technology is recommended. Local implementations can be done, but cloud-based XDR is often more desirable, especially if the vendor has many locations from which to launch XDR activities.
XDR tools are designed to look at more than just endpoints. They examine remote offices, cloud implementations, corporate networks and specialized systems, such as IoT and remote monitoring.
These systems constantly accumulate threat data; they analyze it using AI and behavior analytics and act upon it when necessary. XDR systems can initiate incident response and management activities, provide a team with real-time status data, analyze threat chain data to identify vulnerabilities that might otherwise be missed, mitigate or eliminate threats, and even help return affected systems to a safe and usable state.
In addition to having a greater reach than endpoint-focused systems, XDR systems and platforms provide greater visibility across all elements of network infrastructures. They provide automated threat detection and response across multiple domains, increase performance of a SOC and reduce the amount of time security teams spend examining threats.
Vendors that provide XDR services include CrowdStrike, Cybereason, Cynet, FireEye, Microsoft, Palo Alto Networks, ReliaQuest, SentinelOne, Secureworks and Trellix.
EDR vs. MDR vs. XDR
EDR services generally focus on corporate office endpoints.
MDR vendors deliver threat detection services wherever they are needed within an organization. Users can select how to manage threats and which parts of the ecosystem are addressed. MDR delivers threat detection and response services via an external third-party entity, such as an MSP or cloud service provider. Instead of the user managing threat detection and response activities internally, the firm can delegate those activities -- in whole or in parts -- to a third party.
XDR can address endpoints, as well as technology points outside the organization's offices, such as remote offices, corporate networks, internet activities, websites and other elements.
With so many available options, organizations should carefully evaluate their requirements before considering which tools might be right.
Tips for selecting a threat detection product
When evaluating, selecting and deploying threat detection and response tools and services, consider the following steps:
- Examine current cybersecurity management activities to identify where additional capabilities -- e.g., greater monitoring, AI-based analytics, advanced threat hunting and detection, and automated event managing -- are needed.
- Establish goals and strategies for cyberthreat management based on the needs assessment; consider revising and updating cybersecurity policies and associated procedures.
- Once gaps in cybersecurity management and security strategies have been identified, review them with management, and obtain approval to initiate a selection and evaluation process.
- Identify prospective vendors based on the level of service needed -- be it enhanced threat management, added support for an existing SOC or something similar -- and then evaluate a vendor's capabilities via a request for information or request for proposal.
- When vendor candidates have been selected, ask to see live demonstrations of the systems, platforms, services and dashboards; you want your team to be comfortable with the product under consideration.
- Scrutinize the services to be provided, including training, documentation, maintenance, warranties, contracts, service-level agreements, pricing, compatibility with existing user systems, and how the system or service is deployed, tested, accepted and put into production.
- Once a product has been selected, establish a project plan to prepare the SOC for the new system or service, train teams, schedule system testing and acceptance, and provide post-installation support.
- Once the system is in production, modify existing procedures and policies as needed; schedule periodic reviews of system performance, and conduct tests when patches are made.
EDR, MDR and XDR can provide essential cybersecurity protections: threat monitoring, analysis, containment and elimination. In addition to being capable of monitoring and detecting threats, they can proactively hunt, identify and neutralize potential threats that might otherwise go undetected. Capabilities of existing SOCs can be greatly improved using these systems and services.
Also, data generated by these systems can be valuable during security audit activities and help demonstrate compliance with specific security standards and regulations.
Paul Kirvan is an independent consultant, IT auditor, technical writer, editor and educator. He has more than 25 years of experience in business continuity, disaster recovery, security, enterprise risk management, telecom and IT auditing.






