What is an input validation attack?
An input validation attack is any malicious cyberattack that involves an attacker manually entering strange, suspicious or unsafe information into a normal user input field of a target computer system. Such attacks occur when an attacker purposefully enters information into a system or application to exploit the system's vulnerabilities.
Successful input validation attacks can give hackers and cybercriminals unauthorized access to an organization's computer network. Results may include system malfunctions and a breach of sensitive or business-critical data, putting its confidentiality, integrity and availability at risk.
How input validation attacks work
When user inputs are inadequately validated or not validated, threat actors can execute input validation attacks. These adversaries exploit this weakness and insert malicious input into a computer system, knowing the system will not validate the input, much less block it. They can use different types of malicious input, including code, scripts and commands, to launch input validation attacks, all of which can affect system functionality or lead to data breaches.
When an application or user inputs information as part of a user input attack, it can make a computer vulnerable to unauthorized changes and destructive commands. The type of unsafe data entered into a system can range from simple words to malicious code to information attacks of massive scale.
Impact of input validation attacks
Consider a web application for a financial institution.
Without stringent input validation protocols, a threat actor can insert an input containing malicious code into the application. This causes the application functionality to break, which may affect the user experience of genuine users. It can also cause buffer overflows, which can lead to data corruption, system compromise and denial of service for legitimate users.
Moreover, if successful, the attack may allow the attacker to execute unauthorized commands designed to harm the organization or its users. Attackers may also be able to gain unauthorized access to users' sensitive financial data, which they may then steal for other malicious purposes, like identity theft or extortion.
Any of these can have severe consequences for an affected organization. The attack and subsequent data breach may result in severe financial losses. It can also erode customer trust and increase regulatory scrutiny. In some cases, regulators may impose fines or initiate legal proceedings against the organization.
Types of input validation attacks
Input validation attack is a broad term that incorporates many different types of attacks. Some of the most common attack types are the following:
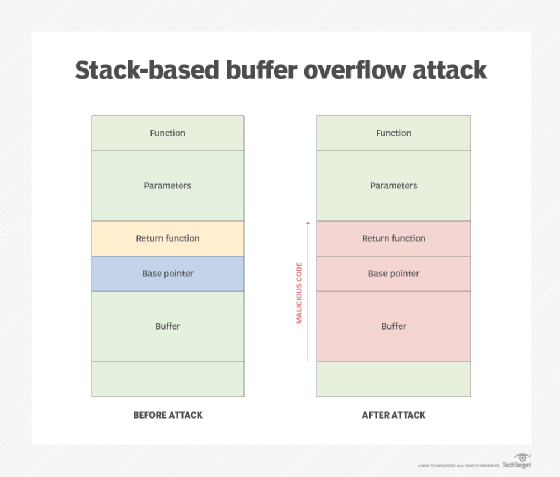
- Buffer overflow attacks. In a buffer overflow attack, the attacker exploits a coding error or vulnerability to cause the volume of data in a memory buffer to exceed its storage capacity. Too much information is sent for a system to process, which modifies the program's execution path and causes the computer or network to stop responding -- it crashes. A buffer overflow might also cause excess information to take up memory that was not intended for it -- sometimes even overwriting some or all parts of the memory. In addition, such attacks can lead to the loss of access control or allow the attacker to exploit other vulnerabilities to cause further damage.
![A diagram showing the area in an application stack typically targeted in a stack-based buffer overflow attack.]()
A stack-based buffer overflow attack is a common type of cyberattack; it exploits an application's stack, the memory space that stores user input. - Canonicalization attacks. A canonicalization attack -- also known as a canonical ideation input validation attack -- occurs when someone changes a file directory path that has digital permissions to gain unauthorized access to parts of a computer. Changing the file path can allow malicious parties to view or steal sensitive information or make unapproved changes.
- Cross-site scripting attacks. An XSS attack involves placing a malicious link in an innocuous place, like a forum. The forum's "new" link contains most of a valid URL with a dangerous script embedded. An unsuspecting visitor may not be able to distinguish between a legitimate and a malicious link. As a result, they may trust the site and not know that a comment or entry on the site contains a virus that can infect their device.
- Cross-site request forgery attacks. A CSRF attack occurs when a user is tricked into performing unauthorized or unwanted actions on a web application in which they are (currently) authenticated. Attackers usually send malicious links using email or chat and manipulate inadequately validated user requests to circumvent existing security measures. If successful, the attacker can get the victim to change their email address or transfer funds to the attacker, among other possibilities. If the victim's account is an administrative account, the attack can even compromise the entire application.
- Structured Query Language injection attacks. SQLi attacks involve adding a string of malicious SQL code to a database query. The attack relies on manipulating SQL code to provide adversary access to sensitive information. They may also be able to execute malicious SQL statements to command the system to do their bidding, such as copying all the contents of a database to a location that they control. Clever hackers can also use SQLi attacks to authenticate malicious information, reveal hidden entries in a database or delete information without the consent of authorized users or owners.
How to protect against input validation attacks
The best form of defense against input validation attacks is to test for input validation before deploying an application. Application developers must use filters to validate inputs and confirm what kinds of inputs are acceptable.
It's important to set a maximum input length and monitor it to ensure it doesn't violate the limit and increase the risk of input validation attacks. Developers must always specify the allowable data type for input fields. This control ensures that unwanted data is restricted from being entered as input, either inadvertently by a genuine user or maliciously by a cyberattacker.
Another strategy to avoid attacks is to implement input validation whenever data processing happens, including user interface controls and server-side verification. Server-side input validation is particularly important because it provides an additional layer of security. It ensures that the server receives only legitimate data, preventing data manipulation and the insertion of malicious input.
Other methods of input validation include the following:
- Client-side validation. This is when user input is validated in the user's browser to catch errors and missing details before the data is sent to the server for processing.
- Regular expressions. Regexes are search queries that can search and match text, such as email addresses or phone numbers, to provide greater control in data processing and management.
- Allowlist. This involves creating a list of approved items or entities and blocking everything that's not on the whitelist by default.
- Blocklist. It involves creating a denylist of problematic entities that will be blocked. Any entity that's not on this list is permitted.
If input validation mechanisms are already in place, it's good practice to review them using regular and comprehensive security audits. These assessments can help organizations to identify and address proactively the weaknesses in their input validation protocols and strengthen their defenses against input validation attacks.
How to mitigate the effect of an input validation attack
An input validation attack could occur despite implementing preventive procedures. However, isolating the impacted systems can mitigate the effect. Isolation helps to contain the scope of the attack and limit the extent of potential damage.
It's also advisable to perform a comprehensive forensic analysis to assess and, if possible, quantify the effect of the attack. Finally, it's crucial to implement controls to prevent data breaches, denial of service or further system compromises.
Cybersecurity has many facets that require a keen and consistent eye for successful use. Improve your cybersecurity implementation with these cybersecurity best practices and tips.