
Getty Images/iStockphoto
Critical Log4j flaw exploited a week before disclosure
The Apache Software Foundation first found out about the Log4j 2 vulnerability in late November, but Cisco and Cloudflare detected exploitation in the wild shortly after.
A critical vulnerability in Log4j 2, CVE-2021-44228, had reportedly been exploited prior to when it was disclosed to the public.
The flaw, sometimes referred to as "Log4Shell," is a remote code execution flaw impacting Log4j 2, the second version of a popular Java logging framework developed by the Apache Software Foundation. The vulnerability, which was initially disclosed on Dec. 9, occurs due to certain standard configurations of previous Log4j 2 versions, and those using the framework can mitigate the flaw either by patching to Log4j 2.15.0 or changing their configuration according to Apache's advisory.
CVE-2021-44228 is considered an extremely dangerous flaw, given its extensive use, and shortly after its public disclosure it was granted a CVSS score of 10 -- the highest possible.
Cloudflare co-founder and CEO Matthew Prince tweeted Saturday that the web security vendor had seen exploitation of the flaw as early as Dec. 1, over a week before it was widely known.
"Earliest evidence we've found so far of #Log4J exploit is 2021-12-01 04:36:50 UTC. That suggests it was in the wild at least 9 days before publicly disclosed," he wrote. "However, [we] don't see evidence of mass exploitation until after public disclosure."
The flaw first became publicly known when an anonymous security researcher with the handle "p0rz9" shared on Twitter a GitHub link to a proof of concept (PoC) exploit of the flaw. Over the following day, the first reports of exploitation came out from organizations such as Cloudflare and New Zealand's Computer Emergency Response Team.
In an email Friday, an Apache spokesperson shared the following timeline of Log4Shell in an email with SearchSecurity, which dated the initial report of the vulnerability to Nov. 24.
"11/24/2021: informed
11/25/2021: accepted report, CVE reserved, researching fix
11/26/2021: communicated with reporter
11/29/2021: communicated with reporter
12/4/2021: changes committed
12/5/2021: changes committed
12/7/2021: first release candidate
12/8/2021: communicated with reporter, additional fixes, second release candidate
12/9/2021: released"
The spokesperson added "the above dates may be -/+ 1 day due to time zones."
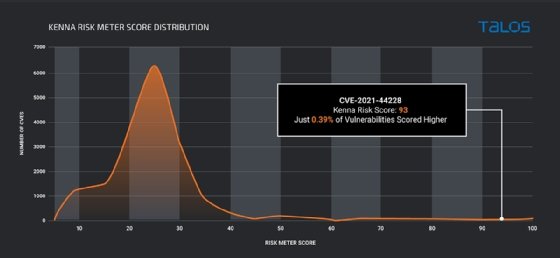
Cisco Talos said in a technical post updated Sunday that it first spotted threat activity related to the flaw on Dec. 2, well ahead of the public disclosure. According to the Kenna Risk Score, a vulnerability scoring system operated by Cisco subsidiary Kenna Security, the vulnerability has a score of 93 out of 100.
"Of the more than 165,000 CVEs currently scored by Kenna," the Cisco post read, "only 0.39 percent have earned a Kenna Risk Score of 93 or higher."
Cisco Talos senior threat researcher Vitor Ventura provided additional context for the severity of the bug in an email to SearchSecurity.
"The vulnerability is like a perfect storm; it allows remote code execution, but it's also very easy to exploit and it exists in an extremely common library," Ventura wrote. "Log4j is used both on Internet exposed systems as well as systems which are further down the stack that at first glance would not be exploitable."
Cloudflare published a blog Friday detailing how it responded to news of CVE-2021-44228, as the company uses the framework internally; Log4j is utilized in many cloud services and applications, including Apple's iCloud, VMware and Minecraft.
It's unclear why exploitation activity occurred prior to Apache's disclosure and the PoC published by p0rz9, but it wouldn't be the first time this year that a reported zero-day vulnerability apparently leaked to threat actors before it could be patched.
Earlier this year, security researchers detected exploitation of the Microsoft Exchange Server vulnerabilities known as "ProxyLogon" weeks before Microsoft disclosed and patched the flaw. Microsoft and infosec consultancy DevCore, which discovered and reported the flaws, each said they investigated the matter and found no evidence of a hack or leak connected to the zero-day exploitation.
Alexander Culafi is a writer, journalist and podcaster based in Boston.







