proof of concept (PoC) exploit
What is a proof of concept (PoC) exploit?
A proof of concept (PoC) exploit is a nonharmful attack against a computer or network. PoC exploits aren't meant to cause harm, but to show security weaknesses within software. Identifying issues enables companies to patch vulnerabilities and protect themselves against attacks.
While PoC exploits aren't intended to be harmful, they could cause potential harm if they fall into the wrong hands. For example, when a PoC is made public before a patch is available, it can provide attackers with a blueprint and a window of vulnerability to exploit a system before users can install a fix.
How PoC exploits work
Typically, PoC exploits are performed by a vendor working for the company. By simulating an attack, it enables the company to patch the security holes without systems or data being compromised.
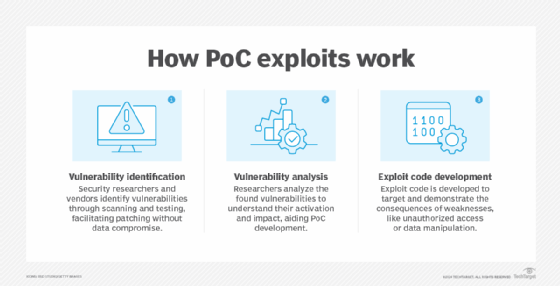
PoC exploits are typically conducted in the following three stages.
Stage 1. Vulnerability identification
The first step involves finding a weakness in a system's software or hardware. This vulnerability could be a coding error, design flaw or configuration mistake. Security researchers often use vulnerability scanners and manual testing techniques to identify these weaknesses.
Stage 2. Vulnerability analysis
Once the vulnerability is discovered, researchers must comprehend its workings. This entails analyzing the PoC code or system to ascertain how the vulnerability can be activated and what repercussions it might have. These details help with creating an effective PoC.
Stage 3. Exploit code development
With a deep understanding of the vulnerability, researchers create a small program or script -- the PoC -- that specifically targets the weakness and exploits it in a controlled way, often demonstrating a specific consequence, such as unauthorized access or data manipulation. The code developed for the test will likely be used in the future to test the software and ensure the new security measures work.
What is the difference between PoC and PoC exploit?
Both PoC and PoC exploit are interrelated concepts, but the former can span multiple fields, while the latter targets security and system vulnerabilities for exploitation.
PoC refers to showing that something is possible. For example, in technology and cybersecurity, a PoC proves that a specific vulnerability can be used to gain unauthorized access or perform unintended actions on a system.
A PoC exploit is the method or trick used to take advantage of a vulnerability. It showcases how this exploit works and how a malicious actor can take advantage of a weakness in a system.
Use cases of PoC exploits
PoC exploits aid against cyberattacks and other threat vectors. Benefits and use cases of PoC exploits include the following:
- Cybersecurity research. Security researchers can develop PoC exploits to demonstrate vulnerabilities in software or systems. These exploits are used to validate the existence of vulnerabilities and to advocate for their mitigation or patching by the software vendor.
- Penetration testing. As part of a penetration test, PoC exploits are used to gain entry into a system for which the organization has given explicit written permission to access. They execute operations to target specific vulnerabilities in an operating system (OS) or application.
- Patch development. After a PoC exploit confirms a vulnerability, it serves as the basis for developing a patch to fix the flaw. Security researchers frequently collaborate with software vendors to responsibly disclose vulnerabilities and jointly craft patches. This collaborative process facilitates the prompt availability of fixes, preempting malicious exploitation by threat actors.
- Security product evaluation. Organizations can use PoC exploits to assess the effectiveness of network security products, such as firewalls, intrusion detection systems or antivirus software. By testing these products with PoC exploits, they can determine their ability to detect and prevent known vulnerabilities.
- Training and education. PoC exploits are often used in cybersecurity training programs and educational courses to teach students about common network vulnerabilities and exploitation techniques. Hands-on experience with PoC exploits can help students understand real-world security and cyberthreats and how to defend against them.
Different types of PoC exploits in cybersecurity
PoC exploits can fall into several categories based on their nature and the vulnerabilities they target. The following are some common types:
- Buffer overflow exploits. Buffer overflow exploits take advantage of a program's vulnerability to buffer overflows, where an attacker can overwrite adjacent memory locations.
- Structured Query Language injection exploits. SQL injection exploits occur when an attacker inserts malicious SQL code into input fields, potentially gaining access to a database or manipulating its contents.
- Cross-site scripting exploits. XSS exploits involve injecting malicious scripts into webpages viewed by other users, often leading to the theft of session cookies or other sensitive information.
- Remote code execution exploits. RCE exploits enable attackers to execute arbitrary code on a targeted system, potentially leading to complete control over the system.
- Privilege escalation exploits. These exploits involve gaining higher-level access or privileges than intended, frequently by exploiting vulnerabilities in OSes or applications.
- Denial-of-service and distributed denial-of-service exploits. DoS and DDoS exploits aim to overwhelm a system or network with excessive traffic, leading to a loss of service for legitimate users.
- Zero-day exploits. Zero-day exploits target vulnerabilities that are unknown to the software vendor or haven't yet been patched, making them particularly dangerous.
What is a PoC payload?
A PoC payload refers to the malicious code that's delivered to a target system and performs some unwanted action. It could be used for various reasons, such as stealing data, taking control of a system for ransomware, installing malware or disrupting system operations.
The PoC payload can be delivered in many ways, such as through a downloaded file, a link that executes malicious code or a vulnerability in a web application.
It's important to note that PoC payloads can be used for both ethical and nonethical reasons. In ethical PoCs used for penetration testing, the payload is often designed to be harmless. It might simply print a message or access a noncritical file to demonstrate the vulnerability exists. However, malicious actors can use PoC payloads to cause real harm.
Databases to search for PoC exploits
According to a blog post from vendor SecurityTrails and a cheat sheet from the University of the Pacific, organizations should consider the following PoC exploit databases, among others, when researching existing PoC exploits:
- CXSecurity. This exploit database offers users immediate access to recent exploits with filters for local and remote vulnerabilities, including risk level, authorship and release date details. Users can access the full code for replication and find PoC instructions. It also includes the latest Common Vulnerabilities and Exposures (CVE) and dorks.
- Exploit-DB. The free Exploit Database is a repository for exploits and PoCs rather than advisories, making it a valuable resource for those who need actionable data right away. For example, it provides a wide range of exploits, including shellcodes, zero-days, remote and local, and web apps, as well as vulnerability reports, security articles and tutorials for penetration testers, researchers and ethical hackers.
- Packet Storm Security. Packet Storm Security is an exploit community dedicated to sharing vulnerabilities and advisories, as well as information about PoCs, demos, and working exploits for local and remote vulnerabilities. It offers direct access to the latest exploits from a web-based interface, where a user can filter and find exploits for local or remote vulnerabilities, along with risk level and other details, such as author and publishing date.
- Rapid7. Rapid7's Vulnerability & Exploit Database contains technical details for more than 180,000 vulnerabilities and 4,000 exploits. These vulnerabilities are used by its vulnerability management tool, InsightVM, and are all included in the Metasploit framework, which is used by its Metasploit Pro penetration testing tool. The database is updated frequently and contains updated security research.
Examples of PoC exploits
CVE is a standardized method for identifying known security vulnerabilities and PoC exploits, providing a reliable way for organizations to improve their security defenses and address vulnerabilities in computer systems.
The following are examples of known and exploited CVEs:
- CVE-2024-1403. This vulnerability has a maximum severity rating of 10.0, or critical, on the Common Vulnerability Scoring System. It affects Progress OpenEdge authentication versions prior to 11.7.19, 12.2.14 and 12.8.1.
- CVE-2024-24919. This vulnerability enables attackers to access information on gateways connected to the internet via Check Point Security Gateways.
- CVE-2023-21773. This is a PoC for the Windows kernel elevation of privilege vulnerability that's due to an incorrect setup of the kernel access control list. A local attacker can exploit this vulnerability by running a specially crafted application and gaining elevated privileges. The PoC demonstrates how to exploit the vulnerability to elevate privileges on a vulnerable system.
- CVE-2023-20871. This exploit was a bogus PoC for VMware Fusion circulated by a profile named ChriSander22 and was found to be deceptive.
- CVE-2023-34051. This is a PoC exploit for a recently patched security flaw in VMware Aria Operations for Logs that was announced by VMware, prompting customers to apply the latest patches.
Organizations use penetration testing to identify vulnerabilities before attackers can exploit them. Gain comprehensive insights into various penetration testing types, steps, methods and frameworks.






