
Getty Images/iStockphoto
93% of vulnerabilities unanalyzed by NVD since February
New research from VulnCheck shows the NIST's National Vulnerability Database has struggled to manage a growing number of reported vulnerabilities this year.
The recent slowdown at the National Vulnerability Database has led to a backlog of 93% of newly reported vulnerabilities since the NIST first announced delays in February.
In a new report on Thursday, threat intelligence vendor VulnCheck provided updates on the vulnerability landscape following disruptions to the National Vulnerability Database (NVD), which helps enterprises prioritize patching. On Feb. 13, the NIST announced it was working to establish a consortium to improve the NVD program, which would cause temporary delays in vulnerability analysis.
"Currently, we are prioritizing analysis of the most significant vulnerabilities. In addition, we are working with our agency partners to bring on more support for analyzing vulnerabilities and have reassigned additional NIST staff to this task as well," the NIST said in the announcement.
VulnCheck revealed an alarming number of unanalyzed vulnerabilities remain, including flaws that have been weaponized and have public proof of concept (PoC) exploits available. VulnCheck's report includes vulnerability data from Feb. 12 through May 20.
"Since that date, 12,720 new vulnerabilities have been added to NVD but have not been analyzed or enriched with critical data that help security professionals determine which software has been affected by a vulnerability," VulnCheck wrote in the report.
The report emphasized that the NVD has "played a critical role" in helping organizations prioritize the increasing influx of vulnerabilities for more than 20 years. VulnCheck highlighted how the NVD provides CVSS scoring and vendor accountability.
However, VulnCheck also addressed the debate over the NVD's current approach and whether it's the most effective. The report referred to NVD's future as "uncertain."
"The outlook for the NVD is bleak. As of now, 93.4% of vulnerabilities remain unanalyzed," the report said.
VulnCheck addressed how the delays affected CISA's Known Exploited Vulnerabilities (KEV) catalog that launched in 2021. Federal agencies are required to mitigate any flaws added to the KEV catalog. VulnCheck commonly reviews the KEV catalog and found that while CISA added 557 CVEs to the list in 2022, it missed 42 flaws that were exploited in the wild.
For the latest report, as of Monday, VulnCheck discovered that 50.8%, or 30 out of 59, vulnerabilities added to the KEV catalog have not been reviewed by the NVD. The report said those KEV entries affect Microsoft Windows, Adobe ColdFusion, ChatGPT, WordPress and more.
More alarmingly, VulnCheck detailed how many weaponized vulnerabilities remain unaddressed in the threat landscape. Patrick Garrity, VulnCheck security researcher, said VulnCheck defines "weaponized" as an exploit that delivers a substantial payload.
VulnCheck's report found that more than 55% of weaponized flaws were awaiting analysis as of Monday. Sixty-eight weaponized vulnerabilities were reported since Feb. 12, and 38 remain unreviewed. Only 2.9% are undergoing analysis.
The data is even more concerning when it comes to vulnerabilities with a publicly available PoC exploit. In recent attacks, threats actors have exploited vulnerabilities just days after a PoC is released. For example, in February, attackers started to exploit a critical Fortinet vulnerability five days following a publicly available PoC exploit.
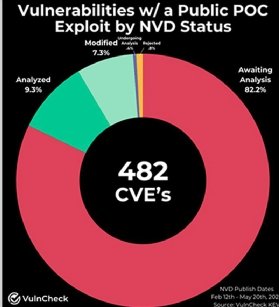
"As of May 20th, 82% of CVEs with a Proof-of-Concept Exploit are unanalyzed by the NVD. Of the 482 CVEs that have a Proof-of-Concept Exploit associated, 396 remain unanalyzed by the NVD," the report said.
Call for coordination
VulnCheck called for coordination efforts among the CVE program community to "fill the void NIST NVD has currently created." For example, the vendor recommended that MITRE and NVD should consider automating the CVE enrichment process to fill in information gaps. VulnCheck also urged NVD to prioritize analyzing every CVE submission and moving to a model where they establish trust with the organizations that assign CVE IDs, which are known as CVE Number Authorities.
"Numerous prominent and influential voices in the industry have warned about how this [analysis delays] gives malicious threat actors an upper hand in weaponizing vulnerabilities with exploits that greatly increases supply chain risks across critical sectors," the report read.
Garrity told TechTarget Editorial that the time needed of processing CVEs and ensuring a certain level of consistency was underestimated. He also said that it is unclear when the NVD issues will be resolved.
"NIST has done a poor job at providing any insight about if and when the issue will be addressed. The limited communication they have provided does not provide any insight, which has left the security community uncertain about the program's future," Garrity said.
He added the private industry can play an important role. "ANY CVE number authority, which includes major vendors, can enhance the CVE information they are submitting to ensure there is broader information available regardless of NVD's status," he said.
Recent reports have highlighted how dire the vulnerability problem has become for enterprises of all sizes. For example, on Tuesday, security vendor Rapid7 revealed that in 2023, more zero-day vulnerabilities were used in widespread attack campaigns than known vulnerabilities. Researchers said the trend has continued into 2024.
Earlier this month, Verizon published its "2024 Data Breach Investigations Report," which found vulnerability exploitation in breaches surged 180% compared to the previous year. Like Rapid7, Verizon also linked exploitation increases to widespread attack campaigns.
Arielle Waldman is a news writer for TechTarget Editorial covering enterprise security.






