
denisismagilov - stock.adobe.com
Types of vulnerability scanning and when to use each
Vulnerability scanning gives companies a key weapon when looking for security weaknesses. Discovery, assessment and threat prioritization are just a few of its benefits.
Vulnerability scanning helps organizations probe for threats across their entire IT infrastructures, from software and specialized devices to files and databases. Types of vulnerability scanning vary, but the overall technique is a key component of any cybersecurity management program. It identifies weaknesses and potential risk points for remediation before they become disruptive.
How vulnerability scanning works
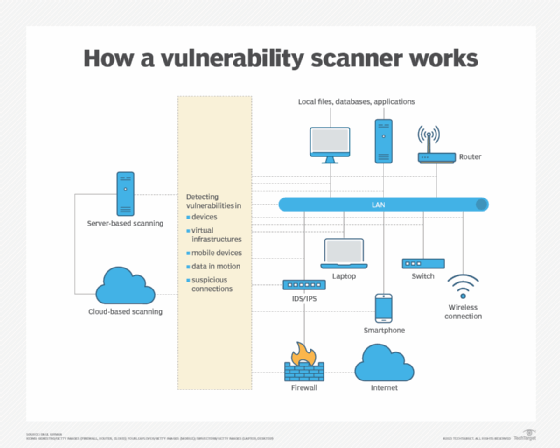
Vulnerability scanning is typically performed through specialized software that examines assets attached to and using a network. The software relies on a database of recognized anomalies, often based on the CVE database of publicly disclosed threats. If a scanner finds an irregularity, it triggers an alert that displays on a user's dashboard.
Vulnerability scanners perform three primary functions:
- Discovery. Scanning provides a single-point-in-time view or continuous view of known and previously unknown assets.
- Assessment. Systems identify and highlight vulnerabilities, using data contained in the CVE database and other databases of known anomalies.
- Prioritization. Based on metrics programmed into the scanner, network devices use CVE data, threat intelligence and data science to assess issues and prioritize them for remediation.
It is important to differentiate between vulnerability scanning and penetration testing. The former identifies an issue, whereas pen testing provides methods to further examine an anomaly and identify ways to remove it. Together, the systems pack a powerful one-two punch for cybersecurity managers and technical staff.
Types of vulnerability scanning and applications
Vulnerability scanner capabilities vary. Among the different types are the following:
- Internal scanning. This is performed inside the boundaries of a network infrastructure and strengthens applications and other resources from internal attacks, rogue or unhappy employees, and threat actors who have penetrated network perimeters.
- External scanning. This approach operates as if the scanner was outside an organization. It performs as a threat actor to identify vulnerabilities inside the perimeter -- for example, firewalls; internal applications; web apps; data ports, especially open and underutilized ports; and network elements.
- Authenticated scanning. In authenticated scanning, a tester logs in as a legitimate user and examines vulnerabilities from a trusted user's perspective.
- Unauthenticated scanning. In unauthenticated scanning, an unauthenticated tester examines the infrastructure as an intruder, which can identify additional risks and vulnerabilities.
- Assessment scanning. This fundamental scanning activity provides a view and analysis of the infrastructure.
- Discovery scanning. Discovery scanning is perhaps the primary role of any scanner. It aims to discover situations that present risks and threats to the organization.
- Compliance scanning. This form of scanning determines if an infrastructure is compliant with standards, policies, regulations and other rule-based requirements.
- Host-based scanning. These scanners assess local systems and servers and their OS configurations -- along with additional supported hosts -- to identify vulnerabilities.
- Network scanning. Network scanning works alongside port scanners to check for weak or questionable passwords. It also performs limited pen testing without disrupting network operations and exploits identified vulnerabilities to pinpoint attack vectors and other anomalies without affecting system and network performance.
- Web application scanning. This examines public-facing web applications for potential vulnerabilities.
- Port scanning. Port scanning looks for open ports in network servers by sending connection requests, which are then monitored to determine their activity. Port scanners are also used by threat actors to gain unauthorized access by identifying open or underutilized ports.
- Database scanning. This technique probes databases to unearth any suspicious activity.
- Source code vulnerability scanning. Regular examination of source code helps testers identify potential anomalies. Consider vulnerability scanning software that applies anomaly data gathered by NIST.
- Cloud vulnerability scanning. Cloud scanners examine the organization's cloud-based environment to identify potential anomalies, such as improper configuration of cloud settings and controls, problems with access control and authentication, and possible overlapping conflicts with other cloud users.
Challenges of using vulnerability scanners
Vulnerability scanning requires careful oversight. If a scanner's CVE database is out of date, it may fail to detect new vulnerabilities that have yet to be identified. Resource management is another challenge. Addressing issues flagged by scanners depends on the resources available to mitigate anomalies.
Continuous scanning may result in degraded network performance, as networks are processing a continuous stream of probes. To that end, the benefits of continuous scanning must be balanced against the effects it has on network performance. Manual or single-view scans, by contrast, are less intensive. But since they only examine the infrastructure at a point in time, they could miss new or highly complex anomalies.
How to select vulnerability scanners
As with any technology, the first action to take when considering vendors is to define the requirements. Some types of vulnerability scanning systems are targeted; others are more flexible and support different scanning environments. Some scanners may be part of a suite of related services such as pen testing or other diagnostic applications. Open Source vulnerability scanning is another option and may be attractive to companies that want to try the technology before making an investment.
When shopping for a vulnerability scanner, consider the following:
- Look for a system that can examine the infrastructure for compliance with specific regulations and standards that are pertinent to the organization.
- Select a tool with a dashboard that displays relevant information.
- Ensure the scanner has the flexibility to scan the most critical systems and existing defenses.
- Confirm IT personnel are available to address vulnerability monitoring and analysis.
- Verify if vulnerability assessments are needed for compliance.
- Determine if cloud-based vulnerability scanning support is needed.
- Confirm compatibility with the organization's existing infrastructure.
Vulnerability scanners provide valuable security data. Scanner outputs should be reviewed, triaged and investigated by security teams. Pair vulnerability scanning with pen testing to optimize threat management as key elements of an overall cybersecurity strategy.





