
Compare vulnerability assessment vs. vulnerability management
Vulnerability assessments and vulnerability management are different but similar-sounding security terms. Discover their similarities and differences.
Cybersecurity has no shortage of jargon. Unfortunately, many terms get used interchangeably yet incorrectly. Let's looks at two similar-sounding terms and their true meanings: vulnerability assessment and vulnerability management.
What is a vulnerability assessment?
A vulnerability assessment is a scan of IT and network infrastructure that looks for security vulnerabilities and weaknesses. Assessments can be done manually by the IT security team or as an automated process. The latter is often preferred so employees can focus on more pressing issues.
A vulnerability assessment typically scans servers, workstations and wireless devices. Software can also be analyzed; web applications are studied the most.
To conduct a scan, teams provide a list of IP addresses and domain names to the scanner. The test can be as short as a few minutes or take a few hours.
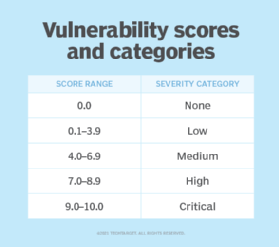
Once the scan is complete, the team receives a report that provides a high-level overview of discovered weaknesses and vulnerabilities. A rating system is used to categorize the level of vulnerabilities found. For example, some vulnerabilities may be negligible and not warrant remediation efforts, while some could be severe and require immediate attention.
Keep in mind that a vulnerability scan is passive. It finds existing gaps and weaknesses, whether known or not. A scan does not dive deeper into the IT and network infrastructure. Deeper dives are conducted through penetration testing.
Vulnerability scans are appealing due to their low cost. A typical test runs a few hundred dollars, depending on its scope. While online tools are available to run scans, this is not recommended. Have an experienced professional handle it or a highly reputable automated tool.
Vulnerability scanning has disadvantages, too. Remediation recommendations are general in nature and won't necessarily be specific to any organization. The test does not further exploit the weaknesses discovered to determine how they got in there in the first place either. A pen test is the best way to get that answer.
What is vulnerability management?
While a vulnerability scan is a single point-in-time check, vulnerability management is an ongoing, dynamic process. It helps security teams manage and remediate weaknesses discovered during a scan. Managing and remediating a particular vulnerability could take weeks or months, depending on its severity.
Vulnerability scans should be conducted at least once a quarter. The follow-up vulnerability management program will, therefore, last at least that long. This time frame gives security teams time to remediate any weaknesses or vulnerabilities.

A typical vulnerability management methodology includes the following steps:
- Assess. This period involves running the vulnerability scan and receiving the report.
- Prioritize the findings. A report typically ranks the severity of vulnerabilities discovered during the scan as low, medium or high. Organizations should further classify these weaknesses based on the established CVSS.
- Act. Using the ranked vulnerabilities, act on any with high or critical rankings immediately. Follow those by remediating any vulnerability with a medium rating.
- Reassess the situation. After remediations are complete, run another vulnerability scan. Most vendors offer multiple scans for a fixed yearly fee, so it may not cost anything to run two scans a quarter.
If the second scan detects the same weaknesses or new ones, the vulnerability management process needs to be repeated. Aim for zero vulnerabilities found, but this isn't realistic. Look to mitigate gaps and holes from reappearing; this is why following the management process is important.








