
Flavijus Piliponis â stock.ado
Penetration testing vs. vulnerability scanning: What's the difference?
Confused by the distinctions between penetration testing and vulnerability scanning? You're not alone. Learn the key differences between the two and when to use each.
IT security terminology and acronyms are bandied about at a furious rate -- so much so that the use of several terms throughout the course of a typical cybersecurity conversation could end up sounding quite similar. The terms penetration testing and vulnerability scanning, in particular, often end up confusing many, especially when it comes to their key differences and overall purpose.
While both aim to detect weaknesses in a system, the methods used to conduct penetration tests and vulnerability scans differ, as do their goals. In short, a pen test is an offensive technique that mimics real-world attacks and their consequences, while a vulnerability scan is a higher-level technique that identifies and reports on flaws.
Let's delve into penetration testing vs. vulnerability scanning -- how they're different, how they're related and why they're both important parts of an organization's IT security strategy.
What is a penetration test?
As mentioned, pen tests are offensive cybersecurity exercises in which IT security professionals use real-world hacking techniques to identify vulnerabilities and what could happen if attackers exploit them. Pen tests help security teams identify, report on and remediate vulnerabilities, as well as verify their removal.
Note that pen testing is a form of ethical hacking. Security professionals should always obtain permission from the organization before performing any tests.
The goal of pen testing, which can be conducted in-house or outsourced to a third-party tester, isn't to steal data or cause harm to assets, but to mimic the tactics, techniques and procedures threat actors might use to identify exploitable flaws in a business's systems. Once identified during a pen test, security teams can fix these vulnerabilities prior to a real-world attack.
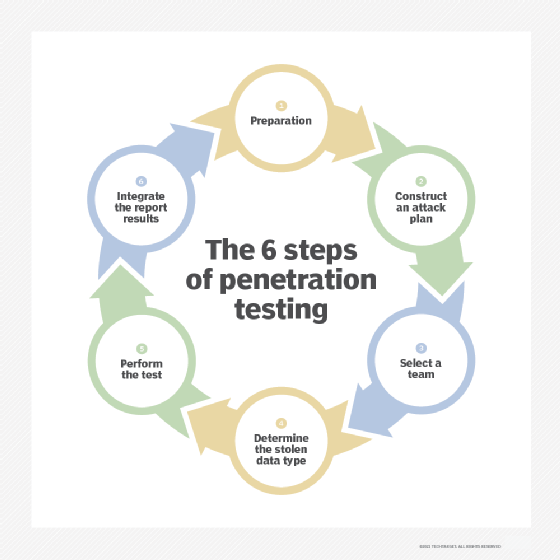
A pen test is a relatively broad term for the following six underlying testing steps:
- Prepare and perform reconnaissance.
- Construct an attack plan.
- Select a team to carry out the tests.
- Choose target data types.
- Execute the pen test.
- Review and analyze results.
Security teams should follow up these steps with remediation efforts and retesting to ensure vulnerabilities are fixed.
Security practitioners usually conduct pen tests with a particular focus. For example, a social engineering penetration test determines how employees respond to phishing scams, a mobile application pen test assesses the security of mobile apps and a cloud pen test discerns vulnerabilities in cloud environments.
Ethical hackers use a variety of commercial and open source penetration testing tools. Some options include Nmap to scan networks, Wireshark to capture and analyze protocols, Checkmarx's Zed Attack Proxy to scan web applications and Aircrack-ng to test Wi-Fi security.
Pen test frequency varies by organization. Many experts suggest annual testing, but organizations in high-risk industries, such as banking or healthcare, might need to test more often. Compliance regulations can also dictate testing cadence. PCI DSS 4.0, for example, requires annual pen tests. Teams should also perform pen tests after infrastructure changes, such as installing new appliances, upgrading applications or equipment, opening new office locations or updating security policies.
Benefits of penetration testing include the following:
- Discovers and remediates vulnerabilities and weaknesses.
- Helps ensure compliance with regulatory testing requirements.
- Strengthens risk management by locating and analyzing security weak points.
- Boosts brand reputation and improves customer trust.
Challenges of pen testing include the following:
- Costs can be high, especially if pen testers don't have a specific attack or target.
- Tests can be time-consuming.
- Attacks don't always replicate real-world breaches, especially if employees know when testing occurs.
- Tests can result in false positives.
- Narrow testing scopes can result in missed vulnerabilities or weaknesses.
- Testing could require skills and resources organizations don't have in-house.
- Executives might ignore test results and see pen testing as a box to check for compliance reporting.
To counter high costs and the time-consuming nature of manual pen tests, many pen testing tools use AI to automate some processes of the testing lifecycle. Automated tools enable teams to speed up testing times and can counter staffing and skills gaps.
What is vulnerability scanning?
Vulnerability scanning is a higher-level security technique that involves the automated detection of weaknesses and vulnerabilities across an organization's networks and systems. It is the first step in the larger vulnerability management process of defining, identifying, classifying and prioritizing vulnerabilities in IT systems.
Vulnerability assessment reports use scan results to summarize the vulnerabilities, prioritize threats and create a remediation plan.
Types of vulnerability scans include the following:
- Internal scans. These scans look for vulnerabilities within a network. They have access to the internal network and look for vulnerabilities such as misconfigurations, missing patches, weak passwords and coding errors.
- External scans. These scans are performed outside the network being tested. They do not have access to the internal network. External scans look for vulnerabilities that could provide access to external attackers, such as open ports, insecure APIs and web application flaws.
- Unauthenticated scans. These scans mimic external attackers who do not have legitimate access to a network.
- Authenticated scans. These scans test a system as a valid, credentialed user. They search for vulnerabilities attackers could exploit if they had access to a network.
Common targeted vulnerability scans include compliance scanning, network scanning, database scanning and host-based scanning.
Security teams have a variety of commercial and open source vulnerability scanners to choose from. Some open source options include Open Vulnerability Assessment Scanner to find known vulnerabilities, Snyk Open Source to discover application dependencies with known vulnerabilities and sqlmap to scan databases.
Vulnerability scanning benefits include the following:
- Discovers misconfigured security controls and other vulnerabilities within a security system.
- Helps ensure compliance with industry regulations for periodic scanning for security weaknesses.
- Helps inform security teams to fix vulnerabilities or weaknesses before attackers exploit them.
Vulnerability scanning challenges include the following:
- Can create false positives about potential vulnerabilities.
- Provides a limited picture of security systems and controls -- organizations require continuous monitoring, which can be costly and degrade network performance.
- Catches known security issues but can miss newer, more sophisticated attacks and zero-day vulnerabilities.
Security teams conduct automated vulnerability scans at regularly scheduled intervals as part of their vulnerability management program. These automated scans provide up-to-date reports of potentially vulnerable systems and software so security administrators can prioritize and schedule patching efforts to mitigate cyberthreats.
Comparing pen testing vs. vulnerability scanning
Both cybersecurity tools enable security practitioners to find weaknesses and vulnerabilities within security controls, networks, web applications, APIs and other IT systems. A major difference between them is vulnerability scanning provides a broad view of a system's weaknesses, whereas pen testing simulates cyberattacks.
While both tools use varying levels of automation to find vulnerabilities, pen tests are generally more manual and in-depth than vulnerability scans, which makes them more expensive. Pen tests also attempt to exploit vulnerabilities to discover their effects on systems, while vulnerability scans only report flaws and weaknesses but not their exploitability.
Pen test vs. vulnerability scan: Which should organizations use?
Most organizations find that pen tests and vulnerability scans are not an either-or proposition. A combination of the two is important to prevent, detect and mitigate system weaknesses.
Vulnerability scanning is often performed as part of a pen test. As mentioned above, step two of a pen test lifecycle involves the construction of an attack plan. Depending on the target types and attack methods, this could involve the use of one or more pen test tools. These tools might focus on the following tasks:
- Intelligence gathering.
- Gaining access to applications or systems.
- Privilege escalation.
- Payload inspection and analysis.
Vulnerability scanning is key to the intelligence gathering step. It detects and creates a report on potential weaknesses. Security teams can use this report to inform their pen test efforts, as well as validate the results of a scan.
Kyle Johnson is technology editor for Informa TechTarget's SearchSecurity site.
Andrew Froehlich is founder of InfraMomentum, an enterprise IT research and analyst firm, and president of West Gate Networks, an IT consulting company. He has been involved in enterprise IT for more than 20 years.







