
kras99 - stock.adobe.com
Top breach and attack simulation use cases
While pen tests offer a point-in-time report on the security of an organization's security defenses, breach and attack simulations offer regular or even constant status checks.
Every security team is concerned about whether the security controls, processes and procedures they have in place will stop or confine an attack, as well as how quickly their recovery plans will maintain or restore systems to normal operations. Many organizations use penetration testing to assess the effectiveness of their security program, but the use of breach and attack simulations are also growing in popularity.
Pen tests tend to be one-off, resource-intensive exercises that only provide a snapshot of the state of security at that point in time. Security teams should use breach and attack simulation (BAS) exercises to test security defenses on a regular, if not constant, basis. This helps teams keep up with constantly changing IT environments and the continuously evolving threat landscape. It also ensures defensive measures are always configured correctly and can detect and respond to any cyberattacks.
What is a breach and attack simulation?
A BAS is an exercise that involves an organization emulating a full attack cycle against its own network, infrastructure and assets using the tactics, techniques and procedures threat actors use. A simulation, which can also involve key security partners that play an active role in the day-to-day protection of IT systems, can be based on known threats or threat actors or focus on security issues, such as exploitation of a specific vulnerability, malware or ransomware attacks, data exfiltration or user behavior.
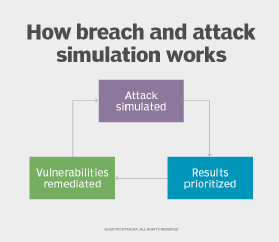
The goal of a BAS is to evaluate how well security controls and personnel perform in the detection and mitigation of attacks. It also identifies areas that need improvement and uncovers existing vulnerabilities and security issues. Regularly testing IT networks and systems from an attacker's perspective enables organizations to evaluate and improve their overall security defenses. Any combination of vulnerabilities, misconfigurations and user behaviors that could put critical assets at risk should be exposed during a simulation.
BAS tools are highly automated. This makes it easier to run frequent BAS tests and avoid the typically longer intervals between pen tests or red and blue team exercises. Frequent testing improves overall visibility into the security environment's actual state.
Top BAS use cases
BAS exercises can be run at any time, but organizations should especially consider the following four compelling use cases for them.
Stress, assess and validate security controls
BAS exercises regularly check that current security controls are correctly integrated and configured to successfully detect and halt the progress of an attack. Frequent updates to software and systems can easily lead to configuration drift or errors that introduce unexpected security gaps.
The iterative nature and wider scope of BAS compared to pen testing makes it easier and quicker to uncover new or unforeseen gaps in security defenses. Not only is the effectiveness of security controls validated, but it helps improve response times as security personnel become more familiar with who needs to do what, when and how through regular practice.
Efficiency improvements
BAS tools can help improve two key security metrics: mean time to detect and mean time to respond. Running regular breach and attack simulations enables security teams to fine-tune their monitoring and detection tools. It also helps teams learn how best to respond to different types of attack so procedures can be updated to improve the effectiveness and timeliness of responders' actions.
Vulnerability patching schedules can also be better prioritized based on those vulnerabilities that are shown to be exploitable in a specific IT environment. Prioritizing vulnerability patching based solely on a CVSS score is not necessarily the most appropriate approach. Compensating controls may already be in place that can prevent their exploitation until the next scheduled patching window, while a low CVSS score vulnerability may still enable an attacker to reach critical or high-value assets due to how a particular environment is configured and protected and, therefore, needs to be patched urgently.
Simulations can also check to ensure patch updates and other changes to the system have not adversely affected overall security.
Resilience and readiness assessment
BASes can emulate how an attack may unfold -- delivery, exploitation, installation, command and control, and malicious actions -- enabling security teams and controls to be prepped and ready to handle a real attack. The Mitre ATT&CK framework is used by many BAS vendors to offer simulations of attacks relevant to particular industries and environments. Simulations can be implemented in less time and with less risk than a full pen test, while still providing details of attack vectors, attackers' movements and methodology, and actions the security team needs to take to prevent a full-blown breach.
Assist with mergers, acquisitions and internal change
Any time an IT environment goes through a rapid period of change, such as during a merger, acquisition or internal expansion or reorganization, it is essential to establish how the changes affect security resilience, often within a short time frame. A BAS is one of the quickest ways to gain visibility into the security of acquired, new or modified systems so integration can be planned to ensure constant security with minimum disruption.
User behavior assessment
Employees are often the weakest link in an organization's IT environment; many breaches start with human error. Users can inadvertently aid attackers by clicking malicious links or attachments and not following security procedures stringently. Phishing-based BAS exercises are a great way to gauge how employees will react to phishing attacks. When based on real-world events and known campaigns adapted to individual, department or country specifics, BAS results provide clear metrics to gauge adherence to internal security standards, assess how effective current cybersecurity training is and decide which individuals need additional training.
BAS use cases set to grow
As enterprise networks become increasingly complex and cloud-oriented and IoT and remote working add to this complexity, breach and attack simulations are an effective and comprehensive means of gauging an organization's actual resilience to cyber threats, while also helping increase the knowledge, understanding and efficiency of those tasked with detecting, preventing and responding to attacks.
Even when making use of BAS tools and technologies, pen testing and red, blue and purple team exercises will remain an important part of ensuring a strong security posture. Remember, though, the results from any of these tests are only useful if they are acted upon and flaws and weaknesses are remediated. The next round of simulations should always show positive improvements and progress.








