
Ljupco Smokovski - Fotolia
Red vs. blue vs. purple team: What are the differences?
Red teams attack, blue teams defend and purple teams facilitate collaboration. Together, they strengthen cybersecurity through simulated exercises and knowledge sharing.
Cybersecurity team exercises involve red, blue and purple teams working in tandem to test cyberdefenses, identify vulnerabilities and weaknesses, and improve an organization's security posture.
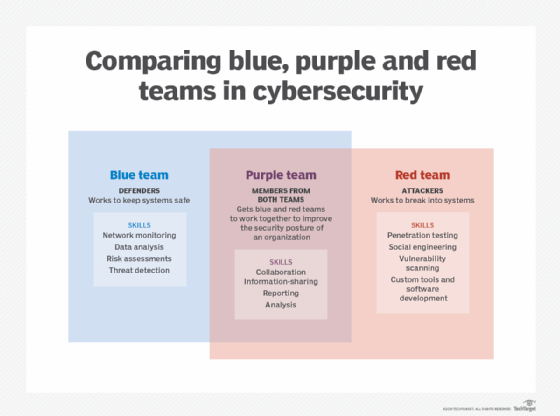
Each team plays a vital role in these exercises. In a nutshell, the red team is offense, the blue team is defense, and the purple team is a mix of both the red and blue teams.
Read on to learn more about each team, including its roles and responsibilities, and how each benefits a security operations center (SOC).
What is a red team?
Playing offense, the red team attacks and attempts to break the blue team's defenses. They simulate attacks to circumvent defense mechanisms, infiltrate networks, and access and exfiltrate data -- all while avoiding detection by the blue team.
Red teams usually consist of ethical hackers, penetration testers and other security professionals. To be effective, red team members should have no knowledge of an enterprise's defense mechanisms. As such, organizations often outsource red team services to a third party.
During cybersecurity exercises, red teams use real-world cyberattack techniques to act as adversaries that exploit weaknesses in a company's people, processes and technologies. Common techniques include the following:
- Penetration testing.
- Phishing and social engineering.
- Credential theft.
- Port scanning.
- Vulnerability scanning.
Team members use open source, commercial and custom-made tools to infiltrate systems and then escalate privileges to successfully "breach" the network.
Post-attack reporting is another red team task. Members write up details about the attacks, including techniques used, vectors targeted, and successful and unsuccessful attempts. Reports should also include recommendations about how to strengthen defensive security measures. These reports help blue teams understand where security gaps exist, how defenses failed and where to tighten security.
What is a blue team?
Playing defense, the blue team is responsible for regularly analyzing enterprise systems to adequately protect them, identifying and remediating vulnerabilities, and evaluating the effectiveness of security tools and processes.
Blue teams usually comprise SOC analysts, incident responders, threat hunters and digital forensics analysts.
During a cybersecurity exercise, blue teams aim to detect, mitigate, contain, eradicate and recover from the red team's attack. Common tactics include the following:
- Monitoring corporate networks, systems and devices.
- Collecting network traffic and forensic data.
- Performing data analysis.
- Conducting network scans and risk assessments.
Blue team members use existing tools and processes during exercises.
Day-to-day blue team responsibilities include the following:
- Creating, configuring and enforcing firewall rules.
- Setting and implementing device and user controls.
- Implementing the principle of least privilege.
- Patching and updating enterprise software.
- Deploying additional security tools and controls.
- Segmenting networks.
- Performing reverse engineering on cyberattacks.
- Conducting DDoS testing.
- Developing or updating incident response and remediation policies.
The blue team is also key in assessing and addressing human vulnerabilities. Staying up to date with the latest phishing and social engineering scams helps blue teams effectively develop and hold security awareness trainings and implement end-user policies, such as password policies.
When they find risks, blue teams should notify senior management, who, in turn, can assess whether to accept the risks or implement new policies or controls to mitigate them.
Like red teams, blue teams gather evidence, logs and data after completing an exercise to write reports about their experiences and insights, as well as develop a list of actions to be taken. They analyze what defenses work and what needs improvement to better protect against potential cyberattacks.
What is a purple team?
Calling the purple team a team is a bit misleading. The purple team is, in fact, not a standalone team but a mix of blue and red team members, roles and responsibilities.
While red and blue teams have the same goal of improving an organization's security, too often, neither is willing to share its "secrets." For example, red teams might not disclose methods used to infiltrate systems, while blue teams might not say how they detected and defended against red team attacks.
However, sharing these secrets is critical to strengthening a company's security posture. The value of red and blue teams is diminished if they don't share their research and reporting.
This is where the purple team steps in. Purple team members are instrumental in getting their red and blue teammates to communicate, collaborate and share. Purple teaming focuses less on which team "wins" cybersecurity exercises and more on how teams work together to improve an organization's security.
Because it is a mix of red and blue teams, purple teaming activities include the following:
- Vulnerability identification.
- Pen testing.
- Threat intelligence.
- Incident response.
- Patching.
- Network monitoring.
- Evaluating tools and security controls.
Benefits of red, blue and purple teaming
While each color team offers its own benefits, organizations can reap the greatest rewards from combining the different teams and strategies. Namely, purple team exercises help with the following:
- Foster collaboration.
- Raise healthy competition.
- Identify where training exercises are needed.
- Encourage employees to think outside the box.
- Help employees learn new real-world security skills in real time.
- Improve threat detection and response teams.
- Continuously improve an organization's security posture.
Sharon Shea is executive editor of Informa TechTarget's SearchSecurity site.








