
Getty Images/iStockphoto
Mandiant: Cyberextortion schemes increasing pressure to pay
At RSA Conference 2022, Mandiant executives discussed how attackers are pulling out all the stops to pressure victims to pay, from DDoS attacks to harassing victims' customers.
SAN FRANCISCO -- Enterprises are facing multilayered cyberextortion campaigns that combine data theft, public shaming and system encryption, which are increasing the pressure on victims to pay ransoms.
During an RSA Conference 2022 session Wednesday, David Wong, vice president at Mandiant, and Nick Bennett, vice president of professional services at Mandiant, provided case studies and anecdotal data that compared the outcomes of two clients that each suffered a ransomware attack and various cyberextortion attempts. While one client was more prepared to deal with a successful attack than the other, the examples highlighted an increasing persistence from attackers that pays off if the victim is ill-equipped.
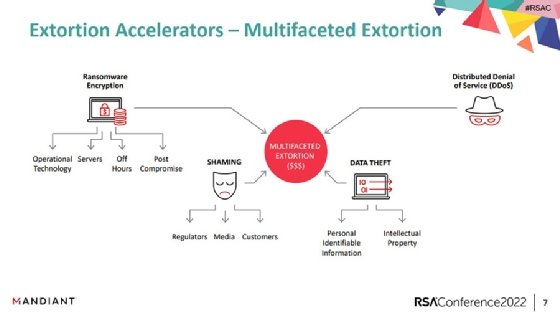
Bennett highlighted some of the newer cyberextortion tactics that ransomware gangs and cybercriminals are using to pressure victims to pay. Encrypting data and demanding payments for decryption keys is only one of the tactics used by threat actors, he said.
"We see them reaching out directly to the victim's customers and antagonizing those customers," Bennett said. "We see them reaching out to the media to get more heat on the victim. We see them sometimes even reaching out to regulators that have jurisdiction over the victims."
The first case study involved a company that had relative success, despite it being the client's first incident response situation, because of some key factors in place. The client had implemented multifactor authentication across all remote access technologies, kept aggregated logs, understood its Active Directory environment, was ready to issue public statements and had a clear plan of whom to contact during all attack stages.
Bennett said that enabled Mandiant to react more swiftly and effectively in its incident response investigation.
"The client's team was confident, they were motivated, and importantly, they were authorized by leadership to make decisions and execute," Bennett said during the session.
On the other hand, the second client did not have confidence in bringing its environment back online, Bennett noted. The company was also worried about encryption starting again and feared public leaking of its data. Overall, the client just wanted to get the attacker to back down. Subsequently, Bennett said, it ended up paying a hefty ransom in the million-dollar range.
Wong also provided an example of an incident response case where the company had a policy against paying. While he said Mandiant agrees with that approach, sometimes they start ransom negotiations with the threat actor to stall and gain additional information on the attack, with no intention of paying. However, this company refused to engage in negotiations at all.
In return, the threat actor got nervous and followed through with posting the company's data on a public leak site, Wong said. That alerted the victim's customers, which caused further problems.
"The attacker started DDoS campaigns, they started calling customers because of that multifaceted extortion ransomware attack where they keep trying to put pressure on you, and you don't have much time to respond because you didn't prepare, and now you've got customers calling you," Wong said. "You need to think about those types of strategies, and it's not anything the IT can do -- it's your lawyers, communication teams and the business folks."
Cyber insurance plays a role
Another factor that is contributing to paying ransoms is cyber insurance, both from a company standpoint as well as incentives for attackers. Wong said that although it's an unpopular opinion, sometimes if companies are insured for ransomware coverage, they will pay because it has little effect on their bottom line.
Payal Chakravarty, head of product at cyber insurance company Coalition, echoed that sentiment in an interview with SearchSecurity. Some companies have become confident that if something happens, they will be covered.
"A few customers say, 'Why are you bothering to alert me, you've got me covered,' or 'I have insurance, so why are you telling me to fix things?'" Chakravarty said. "Additionally, if attackers know you're insured, they'll attack you because there's a higher chance of paying it."
Mandiant also addressed a problem stemming from alerts. In both incident response scenarios detailed during the presentation, Bennett said, the victims were equipped with endpoint security tools that identified credential harvesting and issued an alert. However, the human expertise was lacking.
Bennett said there's often failure in the analyst being able to see the alert, understand the full context and piece it together as part of a more significant event.
Chakravarty has observed similar problems with responses to alerts. In some cases, they are ignored, she said. Other times, there are too many people to loop in, or the person who received the alerts no longer works for that company.
"Recently we started tracking preventability, and almost 50% to 60% of ransomware cases are preventable if they had responded [to alerts]," Chakravarty said.
When Mandiant clients do pay, Wong said, nearly 100% do not attempt to recover the funds, even when law enforcement offers to do so. Several reasons contribute to that decision, including cyber insurance and potential attack reciprocation.
"You just suffered a ransomware attack and made that difficult decision to pay, and once you do, you don't really want to open that can of worms," Wong said during the session. "I do want to give law enforcement credit -- for a lot of crimes, you can follow the money and tackle the problem. But with ransomware today, if the victims aren't really trying to recover those funds, it will make it a lot harder for law enforcement, and we're going to have to tackle this in a different way."








