
Getty Images/iStockphoto
Mandiant upgrades Sandworm to APT44 due to increasing threat
Over the past decade, Sandworm has been responsible for high-severity attacks that highlight the group's persistence, evasion techniques and threat to government bodies.
Mandiant promoted Russian APT group Sandworm to APT44 due to the significant risk it poses to government and critical infrastructure organizations globally.
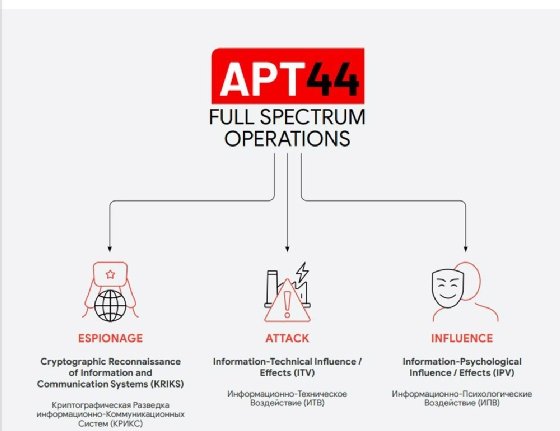
In a blog post on Wednesday, the threat intelligence vendor revealed it upgraded the advanced persistent threat group commonly known as Sandworm to APT44 due to its crucial role in the ongoing Russia-Ukraine war and highly adaptative nature. Mandiant emphasized how dangerous APT44 is compared with other threat groups because of to its ability to conduct espionage, deploy attacks and influence operations while backed by the Russian Main Intelligence Directorate (GRU). The APT group launched many successful campaigns since Mandiant exposed Sandworm 10 years ago.
In 2020, six Sandworm members were charged for highly disruptive attacks that deployed NotPetya malware against Ukraine organizations in 2017. Sandworm was also responsible for the WannaCry ransomware attack in 2017; both events highlighted the risk of spillover attacks to entities outside the target.
"To date, no other Russian government-backed cyber group has played a more central role in shaping and supporting Russia's military campaign," Mandiant wrote in the report.
More recently, what Mandiant now tracks as APT44 is heavily involved in the Russia-Ukraine war, which began in 2022. Mandiant observed APT44 launch a disruptive campaign when Russia first invaded Ukraine that continues presently.
During some of the attacks, APT44 deployed wiper malware, which can lead to permanent data loss. Mandiant observed one attack in 2022 where APT44 operators targeted Ukraine's energy grid and caused power outages.
While Mandiant emphasized what a "formidable threat" APT44 poses to Ukraine, the vendor warned other Russian adversaries should also be on alert.
"Due to the group's history of aggressive use of network attack capabilities across political and military contexts, APT44 represents a persistent, high severity threat to governments and critical infrastructure operators globally where Russian national interests intersect," the report read.
Despite the ongoing war in Ukraine, APT44 has successfully targeted other countries as well. Mandiant observed APT44 conduct espionage operations across North America, Europe, the Middle East, Central Asia and Latin America.
In addition to government entities, Mandiant found that APT44 targets primarily defense, transportation, energy, media and civil society organizations located near Russia. APT44 also frequently targets government organizations and other critical infrastructure operators in Poland and Kazakhstan as well as within Russia.
Regarding U.S. targets, it appears recent APT44 activity targeted victims in the water utility sector. Mandiant tracks GRU activity through the messaging platform Telegram. In January, researchers discovered a video posted to Telegram by a user who goes by CyberArmyofRussia_Reborn, likely associated with GRU.
In the video, CyberArmyofRussia_Reborn took "credit for the manipulation of human machine interfaces (HMI) and controlling operational technology (OT) assets at Polish and U.S. water utilities." That same month, CISA issued an incident response guide for U.S. water and wastewater as well as urged operators to harden security protocols.
"Mandiant cannot independently verify the above claimed intrusion activity or its link to APT44 at this time. However, we note that officials from the affected U.S. utilities publicly acknowledged incidents at entities advertised as victims in the CyberArmyofRussia_Reborn video," the report read.
Mandiant referred to a news article published by My Plainview in February. The media outlet reported on a town meeting where officials of Muleshoe, Texas, discussed an attack against water infrastructure systems that occurred on Jan. 18.
Election concerns
APT44 also poses a threat to the democratic elections process, Mandiant warned. The vendor emphasized APT44 has "repeatedly targeted Western electoral systems and institutions, including those in current and prospective North Atlantic Treaty Organization (NATO) member countries." For example, APT44 interfered in the 2016 U.S. presidential election. Mandiant stressed that APT44 attempts to disrupt the elections process by leaking politically sensitive information and deploying malware to manipulate election data.
"We assess with high confidence that APT44 is seen by the Kremlin as a flexible instrument of power capable of servicing Russia's wide ranging national interests and ambitions, including efforts to undermine democratic processes globally," the report read.
Mandiant observed additional operations where APT44 conducted widespread credential theft to target public and private sector mail servers globally. The campaign, initially discovered in 2019, targeted Exim, Zimbra and Exchange servers. Attacks that exploited an Exim remote code execution vulnerability highlighted APT44's persistence. Organizations who used Exim continued to face attacks attributed to the threat group for over a year.
Persistence is one key contributor to the group's efficacy. Mandiant said following network intrusion, operators leverage living off the land (LOTL) techniques to gain further access, establish persistence and exfiltrate information. To evade detection, operators use pre-existing tools to conduct reconnaissance, move laterally and exfiltrate information on target networks.
Mandiant also warned organizations that APT44 gains initial access through phishing, credential harvesting and known exploited vulnerabilities to target supply chain compromises. APT44 frequently targets initial access vectors that can provide operators with access to a wide range of targets. Operators then decide which targets to prioritize.
Mandiant said APT44's success is likely fueled by its access to several Russian companies and the country's criminal marketplaces where operators can get criminally sourced malware.
Mandiant recommended that organizations prioritize detections of LOTL techniques and investigate instances of commercially available malware as potential APT44 activity.
"Responses to APT44 should also consider the group's sensitivity to counterintelligence risk. This is an actor that is highly aware of incident response and detection efforts, and in certain cases, mitigation efforts may drive an intrusion toward disruptive activity," the report read.
Dan Black, principal analyst at Mandiant and Google Cloud, told TechTarget Editorial that APT44 has thrived for a decade because of its real-world operational experience. Supporting Russia's political and military interests for the past 10 years allowed APT44 to continuously adapt its methods, he stressed.
Black also warned that the U.S. continues to be a primary target for APT44. He said the group has shown an enduring interest in U.S. critical infrastructure over the past decade, emphasizing its role in influencing public opinions to manipulate elections.
"Graduating Sandworm into APT44 is not only a reflection of the severity of the threat posed but also our depth of understanding of how the group operates," he said. "The intensity of APT44's operations in Ukraine has allowed us to develop a more holistic understanding of its methods and capabilities and the ability to strengthen our attribution around the group's past operations."
Arielle Waldman is a news writer for TechTarget Editorial covering enterprise security.







