Information Security
- Editor's letterWhen cyberthreats are nebulous, how can you plan?
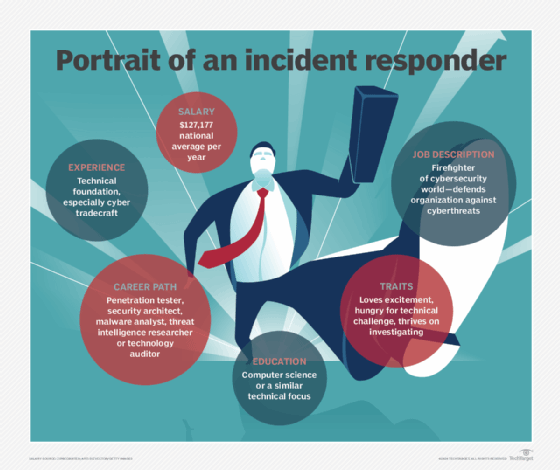
- Cover story
- InfographicEnterprises feel the pain of cybersecurity staff shortages
- FeatureA cybersecurity skills gap demands thinking outside the box
- ColumnReport shows CISOs, IT unprepared for privacy regulations
- ColumnCISOs, does your incident response plan cover all the bases?

stock.adobe.com
CISOs, does your incident response plan cover all the bases?
Security incidents, let's face it, are essentially inevitable. How do you cover the key bases -- education, inventory, and visibility -- in planning for incident response?
Security incidents are a reality you face as a CISO. There's just no way around it. You say you're up for the task, but are you truly ready for things to go sideways? When the going gets rough (and it can get pretty darned rough in the middle of a big incident!), do you know what you're going to do -- your first step, your second step and so on? Will you know where to turn, who to call on and how to lead the charge? Incidents are complicated, but given the threats and vulnerabilities your business faces, they're not uncommon. How things shake out is up to you.
I recall hearing Dr. Phil McGraw say something many years ago that really stuck with me in terms of security and incident response. It was about parents involving their children in adult issues. Dr. Phil said that you shouldn't pull your kids into grown-up conversations and situations associated with marriage, money, health and the like. Since children look up to their parents to see if all is well with the world, pulling them into complicated issues that they cannot solve only serves to harm their young minds. Being a parent myself, children really do look up to you to see how you're going to handle those difficult situations that crop up on a seemingly daily basis. And the older they get, the more they watch.
This is where security and incident response come in.
You see, a security incident will be your testing time. And everyone's going to be watching: board members and executive management, your peers and your subordinates. Lots of people will be looking to you, the CISO, to solve the problem that lies before you. Not that this is a bad thing. Well, it can be a bad thing if you set it up that way.
Have you truly stopped to ask yourself: What is your biggest concern regarding security incidents? Have you pondered what the greatest weakness is in your security program and how that might just facilitate an incident? There's at least one big thing, likely many things, holding back your incident response efforts. It's up to you to identify these impediments so that you can get started addressing them before they bring about an impactful security event.
You probably don't have to look too far. Most incident response situations are the result of one of three things:
- not addressing the simple stuff before the bad guys find it and exploit it;
- not preparing, well in advance, for common incident scenarios; and
- not taking the time to get the facts and jumping to conclusions once an incident does occur.
I've found that many people find more perceived value in "proactive" security controls. It makes sense, but you have to be careful to not spend money on areas of security that might not need investment. Maybe you have enough security products and services. Perhaps your security audits and your vulnerability and penetration testing are about as good as they're going to get. There's seemingly always room for improvement in terms of security, but it never seems to come in the form of incident response initiatives. This is especially true as it relates to the following:
- Inventory: Knowing what's where. From my conversations with technical staff and business managers, it's clear to me that no one really knows what information is where, much less how it's at risk.
- Visibility: Having enough of it to make quick decisions. Many people assume they'll be able to quickly review their logs and comb through the necessary parts of the network once an incident occurs. But usually there are two problems with this assumption: IT pros don't know where to start once an event arises, or they don't have the proper systems and controls in place to get the information necessary to execute a proper response.
- Education: Training team members on their role. This includes what to look for, what to look past, and how to promptly and properly use security tools during the investigation process.
We've all experienced moments that are life-changing. Your job as an information security leader is to ensure these moments are not experienced at work in the form of security incidents and breaches. This comes through building day-to-day habits -- how you view and learn from your internal experiences as well as how you perceive other people's security incidents and breaches.
When it comes to security incidents, Robert Frost was correct when he wrote "the best way out is always through." True, but to get through, you still must be prepared. What's important is how much you've prepared and how efficiently you can step through the necessary processes to see it all through.
Inertia is a powerful thing. It can prevent you from getting the things done that need to be done. Likewise, the desire for immediate gratification -- chasing down this or that security tool without focusing on what's important -- is also powerful. As a CISO, the ultimate goal should be to find your most pressing incident response gaps and plug the holes as soon as reasonably possible. I'm not convinced that incidents have to occur. But, when they do, you'd better be ready.
Related Resources
Dig Deeper on Security operations and management
-
![]()
Evaluating AI tools for healthcare cybersecurity in a saturated market
By: Jill Hughes
-
![]()
Burnout burden: why CISOs are at breaking point, what needs to change
-
![]()
What is a CISO (chief information security officer)?
By: Kinza Yasar
-
![]()
How to build a cybersecurity team to maximize business impact
By: Ed Moyle




















