VMware vs. Citrix: VDI security showdown
Good VDI image management will help an organization at multiple levels.
Many organizations, however, lean on this feature too much as a security easy button. There is no substitution for good Group Policies, application control and antivirus protection.
Organizations that count on this feature to prevent attacks may be in store for a surprise. VDI image management can work to a point, but it might not even slow attacks down as they evolve from one system to the next. IT pros should pay close attention to VDI images, policies and other security recommendations rather than rely solely on this feature.
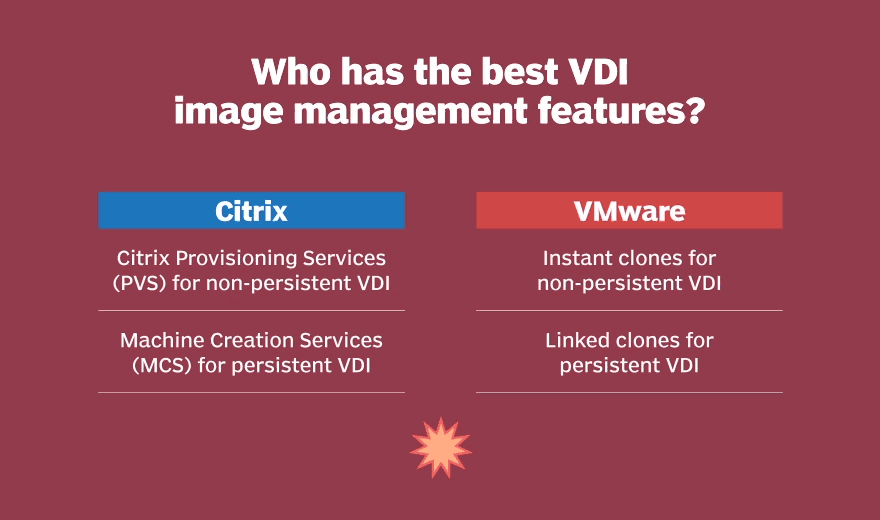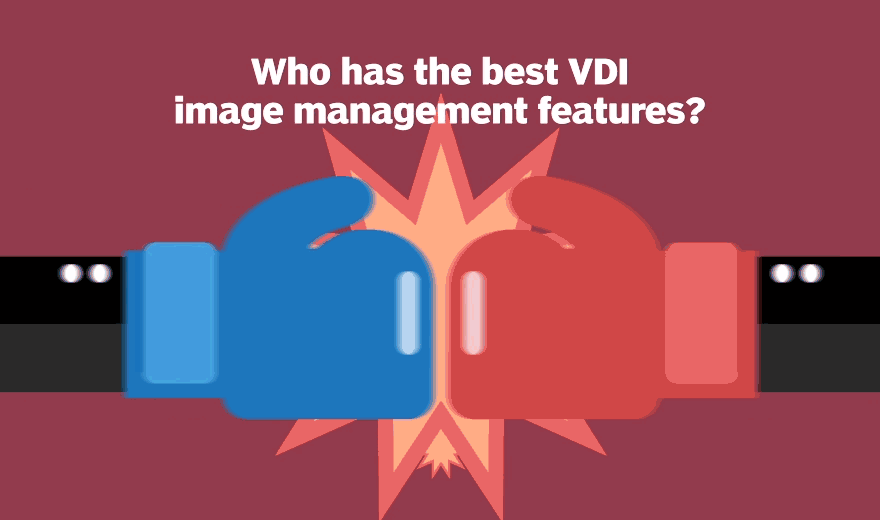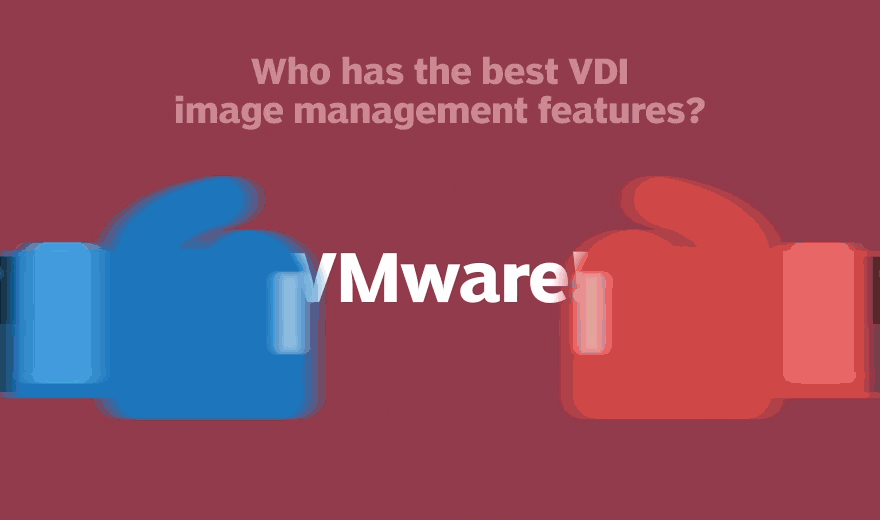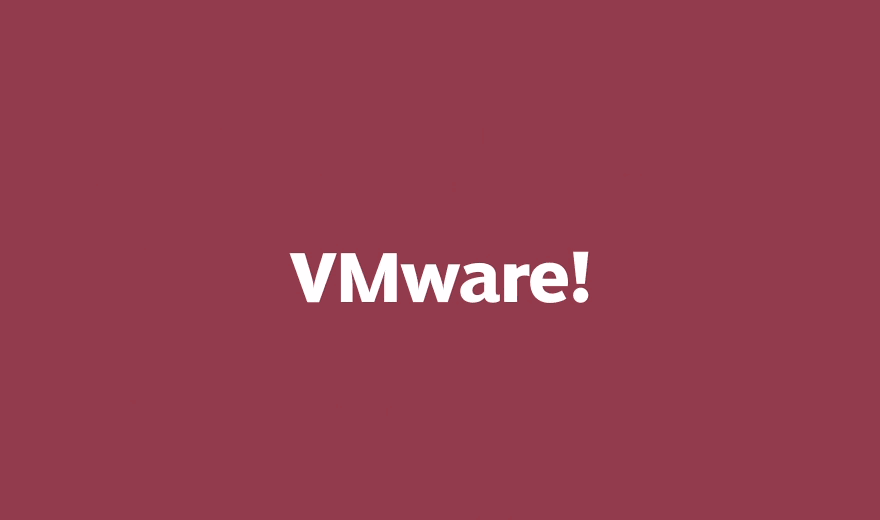
Citrix Machine Creation Services (MCS) and VMware Linked Clones use the same underlying technology. Both tools take snapshots of VMs and share those snapshots with the parent VMs. Similarly, Citrix Provisioning Services (PVS) and VMware Instant Clones both offer automated provisioning. PVS streams a disk image, called a vDisk, to reduce the number of disk images that IT needs to manage. VMware Instant Clone Technology, also called vmFork, clones a parent VM and then uses a copy-on-write strategy to deploy those VMs.
When it comes to VDI image management, VMware's Instant and Linked Clones take the win with only a slight advantage. Both vendors enable IT to destroy the image and/or recreate images after a logout. VMware Instant Clones will rebuild or recompose the desktop after each session by default. VMware Instant Clones prevent file persistency in the OS, which increases security. Some Citrix PVS deployments configure the write cache drive as persistent storage for Windows event logs and other configuration items, which could lead to attack persistency. Citrix PVS enables a way to write files persistently in a read-only deployment, which causes Citrix to lose a few points in this round. From a security perspective, Citrix MCS and Linked Clones are equivalent, based on how each tool retains settings after user sessions until it is recomposed.