Getty Images/iStockphoto
Test conditional access with Microsoft Entra ID What If tool
Admins should employ regular use of this simulation tool to ensure conditional access policies have no conflicts and avoid access problems that can slow down users.
Conditional access policies have become a cornerstone to secure organizational resources within Microsoft Entra and have formed a crucial part of Microsoft's zero-trust security model.
These policies act as gatekeepers, ensuring only authorized users can access sensitive data and applications under the right conditions. However, managing these policies can become challenging as organizations implement increasingly complex security measures. Administrators often face the daunting task of predicting how multiple policies interact, which could lead to unintended access blocks or security gaps.
The What If tool in the Microsoft Entra admin center simulates policy scenarios and previews how policies will behave. This discovery process helps admins adjust configurations and prevent conflicts between policies or overly restrictive access controls.
Overview of conditional access policies
Microsoft designed its zero-trust security model to protect customer resources in an increasingly complex threat landscape. Unlike traditional security models that rely on perimeter defenses, zero-trust assumes that every access request, whether from inside or outside the network, is a potential threat. This model requires continuous verification of user identity, device health and other risk factors before granting access to resources.
Microsoft has adopted the zero-trust approach to provide robust security for its cloud services, including Microsoft Entra, the umbrella term for the company's cloud-based identity and access management offering. The What If tool is part of Microsoft Entra ID -- formerly Azure Active Directory -- which manages identity and access through conditional access policies.
By implementing a zero-trust model, organizations can ensure that only authenticated and authorized users can access their resources, regardless of location or device. This approach is crucial in today's work environment, where remote access and mobile devices have become the norm.
Role of conditional access policies
Conditional access policies are an essential part of Microsoft's zero-trust strategy. They provide access controls to enforce the company's "verify explicitly" principle. Administrators use the policies to set specific conditions that users must meet to access resources.
By combining assignments and access controls, admins can create a layered security model that adapts to the context of each access request. This approach ensures the system grants access based not only on the user's identity but also on their location, their device and the risk level associated with the sign-in attempt.
For instance, an organization can establish a policy mandating multifactor authentication (MFA) for users accessing sensitive data outside the corporate network. Another policy might restrict access from countries where the organization doesn't have operations. Admins can customize the adaptable policies to meet an organization's security needs, providing precise control over resource access.
Types of assignments and access controls in policies
There are two main components to creating or editing a policy in the Microsoft Entra admin center: assignments -- formerly called conditions -- and access controls.
Assignments define the conditions under which a conditional access policy applies. These include:
- Users or groups: Admins can target policies at specific users, groups or organizational roles.
- Locations: Configure policies to apply based on geographic location or IP range.
- Device platforms and state: Control access based on whether the device is hybrid-joined, compliant or meets specific security requirements.
- Cloud apps or actions Apply policies to specific cloud apps or user actions within those apps.
- Risk levels: Integrate with Microsoft Entra ID Protection to enforce policies based on user or sign-in risk levels. Using Microsoft Purview adaptive protection also checks for insider risk.
Access controls determine the actions taken when the policy applies:
- Grant controls: Define user requirements for access, such as requiring MFA, a compliant device or a Microsoft Entra hybrid-joined device.
- Session controls: Managing user sessions to protect sensitive data by applying app-enforced restrictions, enabling session monitoring with Microsoft Defender for Cloud Apps, setting sign-in frequency and configuring persistent browser session behavior.
Challenges in working with conditional access policies
One of the main hurdles administrators face when working with conditional access policies is the inherent complexity and the potential for unintended interactions between policies. As organizations grow and their security needs evolve, they often end up with numerous policies to address specific scenarios.
Although each policy might work well in isolation, the interaction between multiple policies can create unexpected results. For example, a policy requiring MFA for external users might conflict with another policy that blocks access from specific geographic locations. When these policies overlap, predicting the exact outcome of a user's access attempt can be difficult.
This complexity increases with the number of assignments and access controls applied across different policies. Assignments combined with access controls and understanding how these interact during an access attempt is challenging. It often leads to policies becoming too restrictive and inadvertently blocking legitimate access or too lenient and exposing resources to security risks.
Difficulty in foreseeing outcomes
Due to the layered nature of conditional access policies, predicting how they will affect user access can be difficult. Even experienced administrators can find it challenging to anticipate the results of policy interactions, especially when dealing with complex configurations.
Factors such as these compound this difficulty:
- Multiple assignments: Policies often contain several assignments, such as requiring a compliant device and the user to be in a specific group, which makes it difficult to predict combined behavior.
- Order of enforcement: Unlike firewall rules with a clear execution order, conditional access policies undergo a joint evaluation in which all policies must be satisfied and can sometimes lead to unpredictable results.
- Dynamic signals: Conditional access policies can include dynamic elements, such as user risk levels and device compliance status, which change over time. It adds another layer of complexity to predicting a policy's behavior in any given situation.
Introducing the What If tool
Testing and troubleshooting conditional access policies is challenging because live testing carries risks, such as locking out admins or users. Traditional methods are time-consuming and prone to errors and lack immediate feedback after policy changes, making it difficult to prevent security incidents and unintended disruptions.
Admins require improved tools that offer instant feedback and replicate outcomes to find conflicts before they affect users. The What If tool assists this work by simulating sign-in scenarios for a user or service principal to troubleshoot conditional access policies. This simulation capability is crucial for understanding the potential issues of policies before implementing them, reducing the risk of unintended access issues or security gaps.
The primary purpose of the What If tool is to:
- Predict policy outcomes: By simulating different sign-in scenarios, administrators can see which conditional access policies apply and the resulting access decisions.
- Troubleshoot issues: When users experience unexpected access issues, the What If tool can help pinpoint the policy or combination of policies causing the problem.
- Refine policies: The tool shows how policies apply and why to help admins readjust configurations.
Benefits of using the What If tool
The What If tool offers several advantages for managing and optimizing conditional access policies:
- Risk-free testing: Administrators can simulate different scenarios and see the potential outcomes without the risk of disrupting user access or exposing resources.
- Immediate Feedback: The tool provides instant feedback which policies apply to identify and address issues quickly.
- Proactive troubleshooting: The What If tool helps resolve potential conflicts before enabling policies to maintain a seamless user access experience.
- Detailed analysis: Get a report listing applicable policies and the resulting access decision for refining policy configurations.
How the What If tool works
The What If tool simulates an access request based on specific parameters set by the administrator. Here's how it functions:
- User selection: The administrator selects a user or group to run the simulation, such as a user with access issues or a group to test broader policy implications.
- Scenario setup: The admin specifies the sign-in conditions to simulate, such as the target resource, device platform, identity and location. This enables testing a wide range of scenarios, from standard access attempts to more complex situations involving multiple scenarios.
- Policy evaluation: The What If tool evaluates enabled or report-only conditional access policies against the specified scenario. It determines which policies would apply and what the resulting access decision would be, including grant, block or require MFA.
- Report generation: The tool generates a report showing the simulation's outcome, including the policies that apply and required controls, policies that don't apply and why and any app filters with custom security attributes.
How to use the What If tool for troubleshooting policies
The What If tool simulation process is straightforward and provides valuable insights into how policies will behave in various scenarios.
Accessing the What If tool
- Sign in to the Microsoft Entra admin center with admin privileges.
- Go to Entra ID>Conditional Access>Policies to manage all conditional access policies.
- Click What If and set up the simulation, adding the conditions to check, such as client app, device platform and identity.

Setting up a simulation
- Choose the identity to test. Click "No user or service principal selected" and use the search box to find the user or service principal.
- Specify the conditions to test. Required conditions include identity, target resource, device platform and client app. Optional conditions are sign-in risk, location, user action or authentication context, device state and authentication strength.
Running the simulation
- After setting up the desired scenario, click What If to run the simulation. The tool checks the selected user or service principal against enabled or report-only conditional access policies.
- The What If tool provides an evaluation report once the simulation completes, which includes:
- Applicable policies: A list of all the conditional access policies that apply to the specified scenario.
- Policy outcome: The outcome for each policy, such as grant access, block access or require MFA.
- Overall decision: Indicates the final decision for the access attempt based on the combined evaluation of all pertinent policies.
Understanding the report
The What If report details how conditional access policies apply in the specified scenario. Critical sections of the report include:
- Policy evaluation: Lists each policy evaluated, showing whether it did or didn't apply, and the enforced action.
- Policy details: The report provides detailed information for each applicable policy, including the grant controls and session controls it evaluated.
- App filters: Shows if a policy uses custom security attributes for filtering apps.
- Non-applicable policies: What If will list any policies in scenarios when the first condition isn't met with an explainer.
- Classic policies indicator: Lists if legacy conditional access policies exist in the environment.
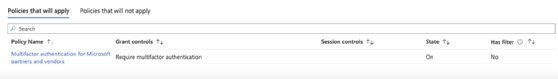
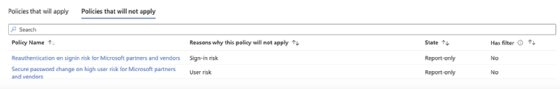
To enhance the process, enable the Enhanced 'What if' evaluation experience for further details when evaluating the policies.
Make changes based on the What If report
- Identify and resolve conflicts: Use the report to identify conflicting policies that might lead to unintended access blocks or overly lenient access. Adjust the assignments to ensure a clear and intended access path.
- Test before implementation: Before changing conditional access policies, use the What If tool to simulate the new configuration, evaluating the changes' effect and verifying that they will produce the desired results.
- Refine policies: Based on the simulation results, adjust policies to align with security objectives. For example, if a policy requiring MFA doesn't trigger as expected, change the assignments to ensure they apply to the right users and intended scenarios.
Tips for effective use
- Regular testing: Use the What If tool often to validate policies, especially after creating new ones or modifying existing ones to find issues before they affect users.
- Test a variety of scenarios: To make policies resilient and comprehensive, don't just test typical access scenarios. Simulate a range of conditions, including high-risk situations and edge cases.
- Document findings: Record the simulations and findings for future troubleshooting and to explain policy decisions to stakeholders.
Remove doubt with the What If tool
In Microsoft's zero-trust security model, conditional access policies are key to securing access to organizational resources. The What If tool provides a safe and efficient way to check policies to help admins identify and resolve conflicts and optimize access controls.
Incorporating the What If tool into a regular policy management routine helps prevent misconfigurations, enhances the organization's security and ensures policies work as expected. By using this tool, admins can confidently navigate the complexities of conditional access policies, ensuring they provide the intended level of protection without compromising user productivity.
Liam Cleary is the founder and owner of SharePlicity, a technology consulting company that helps organizations with internal and external collaboration, document and records management, business process automation, automation tool deployment, and security controls and protection. Cleary's areas of expertise include security on the Microsoft 365 and Azure platforms, PowerShell automation, and IT administration. Cleary is a Microsoft MVP and a Microsoft Certified Trainer.







