
Getty Images/iStockphoto
Understand the basics of Microsoft hybrid identity
Microsoft hybrid identity combines on-premises AD resources and cloud-based Entra ID capabilities to create a seamless access experience across environments.
Although AD traditionally serves as the central authority for managing users, computers and security within an organization's network, Entra ID provides similar functionalities in the cloud, focusing on managing access to cloud applications and resources.
Microsoft hybrid identity gives IT admins the best of both worlds, combining on-premises identity infrastructure with cloud-based identity management.
Hybrid identity is a simplified, secure and user-friendly identity and access management (IAM) system. But it also comes with unique implementation challenges and prerequisites IT admins must thoroughly understand before deploying it for their organization.
This article covers the components involved in Microsoft hybrid identity, how to prepare for its deployment and an implementation roadmap for launching hybrid identity for your IT environment.
What is Microsoft hybrid identity?
Hybrid identity refers to Microsoft's integration of on-premises and cloud-based identity infrastructure and management.
This system enables users to use a single identity, such as username and password, to access both on-premises resources managed by AD and cloud resources managed by Entra ID, formerly Azure AD. For example, users can use the same credentials to log on to local AD resources that they would use for cloud-based applications, such as Microsoft 365 and other SaaS applications.
Hybrid identity is commonly used in environments transitioning to the cloud, as it enables coexistence between legacy systems and modern cloud services. It provides several benefits to IT administrators, including centralized IAM and access to enhanced features, such as conditional access and multifactor authentication (MFA) from Entra ID.
Key concepts of Microsoft hybrid identity
The following components comprise a hybrid identity system:
- On-premises AD. AD manages user identities, groups and access to internal resources.
- Entra ID. This extends identity capabilities to cloud apps and services.
- Entra Connect or Cloud Sync. These tools synchronize identities between on-premises AD and Entra ID.
- Authentication model. Choose from password hash synchronization (PHS), pass-through authentication (PTA) or federated authentication with AD Federation Service (AD FS).
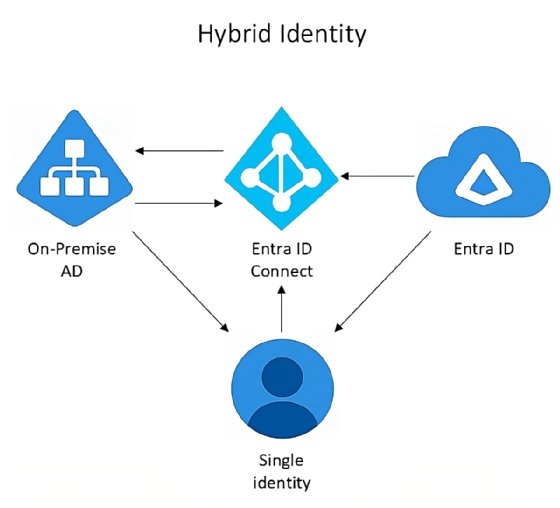
Microsoft Entra Connect, formerly known as Azure AD Connect, and Microsoft Entra Cloud Sync are two tools used to synchronize on-premises AD with Microsoft Entra ID. Although both achieve similar outcomes -- syncing identities to the cloud -- they differ in architecture, capabilities and use cases.
Microsoft Entra Connect overview
This comprehensive tool, which is installed on an on-premises Windows Server, provides robust sync and authentication features. Key features include the following:
- Directory synchronization, including users, groups and passwords.
- Password hash sync, pass-through authentication or federation.
- Custom filtering, such as by organizational unit or attribute values.
- Exchange hybrid configuration support.
- Writeback features, including password, device and group writeback.
Entra Connect's architecture requires a SQL database and runs as a full server application. It comes with a heavier footprint and requires more ongoing maintenance compared to Entra Cloud Sync. Given this, Entra Connect is best for complex enterprise environments, including those with Exchange hybrid deployments, and scenarios that require writeback capabilities.
Microsoft Entra Cloud Sync overview
This lightweight, cloud-managed agent-based tool is designed for simpler and more scalable synchronization. The following are some of its key features:
- Lightweight agent-based sync.
- Password hash sync only.
- Multiple AD forests supported (with multiple agents).
- Managed entirely from the cloud with no on-premises UI.
Entra Cloud Sync's architecture uses cloud-based configuration and doesn't require a SQL database. It can be easier to deploy and maintain than Entra Connect, which makes it a good fit for modern, cloud-first organizations, including ones with multiple AD forest environments, and scenarios without the need for writeback.
Authentication models
Password hash synchronization. With PHS, hashes of user passwords are synced from on-premises AD to Microsoft Entra ID, and the user authenticates directly with Entra ID in the cloud.
The advantages of PHS are that it's simple to deploy and manage, and there is no dependency on on-premises servers at logon. It supports single sign-on (SSO), although there is a sync delay when changing user passwords. Some organizations might choose to use other methods because password hashes are stored in the cloud.
Single sign-on for hybrid identity
SSO in a hybrid identity environment enables users to access both on-premises and cloud-based applications and resources using a single set of credentials -- typically their AD username and password -- without being prompted to sign in again each time. In a hybrid identity implementation, SSO authenticates the user once, typically at the time of device login using AD credentials. It automatically passes authentication tokens to cloud applications, such as Microsoft 365 or SharePoint Online. Admins can maintain centralized IAM using AD or Entra ID.
Pass-through authentication. In this model, users enter credentials in the cloud, and the authentication request is securely passed to an on-premises agent, which validates it against the local AD instance. The advantages of this method are that no password hashes are stored in the cloud, and the agent is lightweight, making it easier for IT administrators to implement than AD FS. It does require the on-premises infrastructure to be online.
Federation. Microsoft Entra redirects the user to AD FS, an on-premises federation service, for authentication. IT administrators have full control over authentication policies and can implement custom login branding, multifactor options and smart card support. Federation is more complex to deploy and maintain, and it requires multiple servers. However, this authentication method is typically required to satisfy government and regulatory requirements.
Why implement hybrid identity?
Organizations should implement hybrid identity to bridge the gap between on-premises infrastructure and the cloud. This enables a secure, seamless and scalable identity experience across all environments.
Here are some key reasons why hybrid identity is beneficial.
Familiarity for users
The use of a single identity for your organization's users lowers frustration, improves productivity and reduces password fatigue. Users often find that their login experience is improved, as it reduces repeated sign-ins. For example, a user can log into their Windows device using AD credentials and open Outlook or Microsoft Teams. Thanks to Entra ID's SSO option and the user's on-premises identity, access is granted without another login.
Simplified management
Most organizations already use on-premises AD. Hybrid identity incorporates existing AD users, groups and policies without the need to recreate them in the cloud. It simplifies user management, provisioning and deprovisioning, while also ensuring consistent access policies, auditing and role assignments.
Enhanced security
Hybrid identity uses cloud-based conditional access, MFA and risk-based access. It reduces the risk of account compromise from reused or weak passwords. Conditional access policies enable IT administrators to create rules that control how, when and under what conditions users can access corporate resources -- especially cloud apps, such as Microsoft 365. These policies play a key role in zero-trust security by enforcing the "never trust, always verify" principle. Admins can set specific conditions based on location, device compliance, IP address, the application accessed or user group membership.
Conditional access is the gatekeeper of the hybrid identity environment. It analyzes the context of each sign-in and enforces real-time decisions -- allow, block, challenge or restrict access -- to protect corporate data without hindering user productivity.
Planning for hybrid identity
Planning and implementing Microsoft hybrid identity using Entra ID requires understanding your current infrastructure and IAM methods, preparing your environment and carefully deploying it.
You must decide which authentication strategy -- PHS, PTA or AD FS -- best suits your organization and its security requirements. Design the identity architecture, including sync scope, domains and forests, and create an implementation roadmap.
Implementation requires several technical and organizational prerequisites to ensure a smooth deployment. These cover your on-premises environment, cloud configuration, security planning and infrastructure readiness.
The on-premises AD requirements include the following:
- At least one AD forest or domain with a functional level of Windows Server 2008 R2 or later.
- A routable User Principal Name suffix. For example, the UPN must be [email protected] instead of user@localdomain.
- Consistent and unique user attributes, such as UPN, mail and SAM account name.
- Cleanup of stale accounts, duplicates and nonstandard naming conventions.
The following infrastructure requirements must be in place:
- A dedicated Windows Server to install Microsoft Entra Connect.
- Administrative access to both on-premises AD and Entra ID tenant.
- Required network ports open for sync and authentication, such as HTTPS, LDAP or Kerberos.
- A valid Microsoft Entra ID tenant, either as part of your Microsoft 365 subscription or standalone.
- At least one verified custom domain in Entra ID.
Then, ensure security and compliance readiness with these steps:
- Plan to implement MFA.
- Define conditional access policies, such as those based on device, location or risk.
- Prepare to handle identity protection, user risk detections and reporting.
Your deployment strategy should incorporate operational and user readiness. Communicate hybrid identity plans to stakeholders, train IT staff and prepare user education materials for any sign-in behavior changes.
The following outlines a typical implementation roadmap:
Phase 1: Planning
- Define business goals for hybrid identity.
- Choose your authentication model (PHS, PTA or AD FS).
- Design identity architecture (sync scope, domains, forests).
Phase 2: Preparation
- Prepare AD with cleanup and UPN standardization.
- Prepare server infrastructure for Entra Connect.
- Review security and compliance requirements.
Phase 3: Deployment
- Install and configure Microsoft Entra Connect.
- Configure selected authentication method.
- Set up SSO or seamless SSO (optional).
- Run initial directory sync (test with pilot users).
Phase 4: Testing and validation
- Validate the following components:
- User sign-ins to Microsoft 365 and Entra-protected apps.
- Password changes and sync behavior.
- MFA and conditional access, if configured.
- Monitor logs and sync health.
Phase 5: Rollout
- Expand sync scope to include all users/groups.
- Communicate changes to end users.
- Begin enabling cloud services, such as Teams or SharePoint
Phase 6: Optimization
- Deploy MFA, conditional access and self-service password reset.
- Consider group writeback or hybrid device join.
- Monitor and fine-tune performance and logs using Microsoft Entra admin center.
Potential issues with on-premises AD
Although hybrid identity offers flexibility and control by integrating on-premises AD with Microsoft Entra ID, it also introduces technical and operational challenges that organizations must plan for.
AD health issues. Replication errors, DNS issues or corrupt AD objects can lead to failed synchronization or incomplete user provisioning in Entra ID. Run dcdiag, repadmin and Entra Connect Health checks regularly. Clean up AD objects before sync.
Password or authentication inconsistencies. Password changes might not sync quickly, especially with PHS. If not redundant, PTA agents or AD FS servers can become single points of failure. Clock drift in AD can cause Kerberos or auth token issues. Use redundant agents, ensure accurate time sync and monitor authentication services.
Synchronization failures. Microsoft Entra Connect might fail to sync due to connectivity issues, outdated schema or object attribute mismatches -- especially if UPNs don't match verified domains. Be sure to review sync rules, use consistent UPNs and monitor Entra Connect sync logs.
Security gaps. On-premises AD might not enforce MFA, conditional access or sign-in risk detection. To mitigate security concerns, use Microsoft Entra conditional access and identity protection and enforce cloud policies.
Hybrid identity is the cornerstone of a secure, flexible and user-friendly IT environment in the cloud era, especially for organizations transitioning from legacy systems.
Helen Searle-Jones holds a group head of IT position in the manufacturing sector. She draws on 30 years of experience in enterprise and end-user computing, utilizing cloud and on-premises technologies to enhance IT performance.







