
What is federated identity management (FIM)? How does it work?
Federated identity management (FIM) is an arrangement between multiple enterprises or domains that enables their users to use the same identification data (digital identity) to access all their networks. These partners are also known as trust domains. A trust domain can be an organization, a business unit or a smaller subsidiary of a larger organization.
FIM is a system of single login and multiple access. For FIM to work effectively, all involved partners must have a sense of mutual trust. Each trust domain maintains its own identity management. However, all domains are interlinked through a third-party service that stores user access credentials and provides the trust mechanism needed for FIM to work. This third service is known as the identity provider or identity broker.
This provider manages access control for multiple service providers. The FIM arrangement is made between two or more identity brokers across organizations.
FIM links users' identities across multiple security domains. When two domains are federated, users must only authenticate themselves to one domain. This improves the user experience by enabling users to move between systems quickly and securely. That's because a second security domain -- and part of the FIM system -- trusts that the user's home domain authenticated the user and enables them to have unfettered access.
Examples of federated identity management
Examples of FIM systems include OpenID and Open Authorization (OAuth), as well as Shibboleth, which is based on the Security Assertion Markup Language (SAML) from the Organization for the Advancement of Structured Information Standards, commonly known as OASIS.
A common example of FIM is when someone signs into a third-party website using their Google, Facebook or Apple accounts. With Google's FIM system, for example, users can log into their Gmail, YouTube, Disney+, Spotify and Netflix accounts, along with some other mobile apps and websites.
How does federated identity management work?
FIM works because the FIM partners send each other authorization messages. These messages can be transmitted using SAML or a similar Extensible Markup Language (XML) standard. Both enable users to log on once to access multiple affiliated but separate websites or networks.
Users' credentials are provided to and stored with their identity provider, which is their home domain. Then, when logging in to a service, such as a software as a service (SaaS) application, they don't have to provide credentials to the service provider. Rather, the service provider trusts the identity provider to validate these credentials and grant them access.
So, when a user attempts to log into a website or application using FIM, the website or application requests federated authentication from the identity provider's authentication server, which verifies the user's access and permissions. The identity provider then authorizes the user to the service provider, and the user is granted access.
What are common federated identity management use cases?
FIM is useful when administering applications that need access to resources in multiple security domains.
The following are common FIM use cases:
- New users added to a system after a merger or acquisition.
- External vendors or distributors that require access to the organization's resources.
- Users from commercial identity providers.
- Users with credentials from a public organization.
- Citizens using credentials from a national identity provider.
- Access to social websites, such as Gmail or Facebook.
Technologies that make up FIM
Several technologies make up FIM. Authentication protocols constitute a significant part of the process that enables communication between identity providers and service providers. Authentication protocols that can be used include the following:
- SAML. SAML is an open standard for sharing security information about identity, authentication and authorization. It uses XML to share data.
- Open Authentication. OAuth is an open standard authorization framework for authorization over the internet.
- OpenID Connect. OpenID Connect is an open specification for authentication and single sign-on (SSO). It expands on OAuth, enabling third parties to confirm user identities and retrieve profile data.
- Kerberos. Kerberos is an authentication protocol that authenticates service requests between trusted hosts across untrusted networks.
- Remote Authentication Dial-In User Service (RADIUS). RADIUS is a client-server protocol used for centralized authentication for remote and network access.
Different frameworks are also used to define how an organization should establish trust and share identity data. WS-Federation, for example, is a framework commonly used for Microsoft platforms, such as Active Directory Federation Services (AD FS). WS-Federation provides a general language to connect users and resources across secure boundaries. Shibboleth is another example, which is an open source system that supports SAML for federated authentication.
Technology is also needed to store user identities and attributes, which is usually done using a directory service, such as Lightweight Directory Access Protocol or AD FS.
The 7 laws of identity that guide FIM
There are seven commonly cited laws to FIM, called the laws of identity, which aim to provide a set of principles for designing secure and user-friendly identity management. These seven laws comprise the following:
- User control and consent. Users should be able to give permission to share their identity data, and they should know how data is shared.
- Minimal disclosure. Identity systems should share only the minimum amount of data necessary.
- Justification. Identity systems should ensure that identity data is only shared with parties that can prove they have a valid reason to receive it.
- Directed identity. Identity systems should protect public and private identifiers to protect user privacy.
- Competition. Different identity providers should also be supported to improve interoperability between different technologies.
- Human integration. To reduce computer-to-computer attacks, the human user should be included as a component of a distributed system.
- Consistency. Users should have a simple and consistent experience from platform to platform.
The government's role in FIM
Governments have also pushed for FIM requirements to be implemented. For example, in 2012, the Homeland Security Presidential Directive 12 was issued in the U.S. This established a governmentwide requirement to create a secure form of ID for federal employees and related contractors. The directive aimed to create a secure identification system across all federal agencies, encouraging quick movement between platforms and programs.
One year earlier, in 2011, another governmentwide program was issued: the Federal Risk and Authorization Management Program. This was closely related to FIM, as it enforced a standardized use of identity and access management (IAM) practices for cloud services.
What is the difference between SSO and FIM?
Single sign-on is an important component of FIM, but it isn't the same as FIM.
SSO enables users to use a single set of credentials to access multiple systems within a single organization. It is token-based, meaning that a token rather than a password identifies users.
FIM enables users to access systems across federated organizations. They can use the same credentials to access the applications, programs and networks of all members within the federated group. It provides single-step access to multiple systems across different organizations. Unlike SSO, FIM users don't provide credentials directly to a web application but to the FIM system itself.
Organizations that implement SSO do not necessarily use FIM. However, FIM relies heavily on SSO technologies to authenticate users across domains.
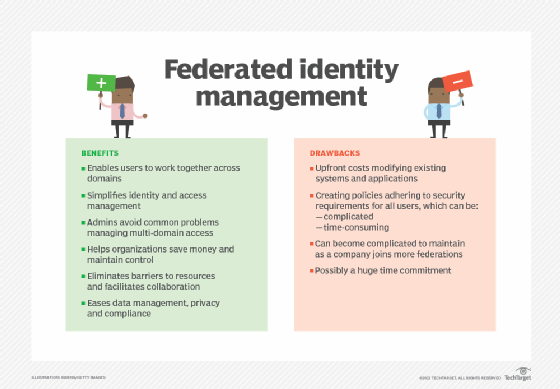
What are the benefits and drawbacks of federated identity management?
FIM provides several benefits to an organization if implemented, including the following:
- When organizations work together on a project, FIM enables participants to access and share resources across all domains.
- FIM simplifies the process of authenticating and authorizing users of the systems within the federation.
- At the same time, administrators in each organization still control access levels in their own domains. They can set permissions and access levels across different systems in different security domains for a user based on a single username. This reduces their work and simplifies IAM.
- Administrators can also avoid common issues that crop up when balancing multi-domain access, such as developing a specific system to make it easy to access the resources of an external organization. FIM's consolidation approach helps organizations save money and maintain control.
- FIM also eliminates the barriers that often prevent users from easily and securely accessing the resources they need. It delivers convenience so they can securely access systems in different domains without remembering multiple credentials or logging in multiple times. Consequently, the user can save time, minimize access friction and increase productivity.
- FIM also simplifies data management, privacy and compliance.
- Storage costs are reduced by centralizing identity management, reducing data redundancy and simplifying data synchronization.
There are some drawbacks that come with FIM, however:
- One drawback of FIM is the upfront costs that organizations incur to modify existing systems and applications. This can be a substantial financial burden for smaller organizations.
- Another challenge is that participating federation members must create policies that adhere to the security requirements of all members. This negotiation can be a complicated, time-consuming undertaking when each enterprise sets different requirements and rules.
- Finally, a participating organization can be a member of more than one federation, so its policies should reflect the rules and requirements of each federation. As the company joins additional federations, this can become complicated and require a huge time commitment that many enterprises might not be prepared for.
FIM plays an active role in IAM. Learn more about the challenges behind IAM in cloud and SaaS environments.






