What is a message authentication code (MAC)? How it works and best practices
A message authentication code (MAC) is a cryptographic checksum applied to a message to guarantee its integrity and authenticity. A MAC is used in network communications to confirm that a message is indeed coming from the stated sender and has not been changed.
MACs are useful for protecting data, preventing impersonation and detecting message tampering. They ensure the transmitted message originated with the stated sender and was not modified during transmission, either accidentally or intentionally. To do this, MACs use authentication cryptography in the verification process, ensuring the data sent from one party to another is legitimate and unaltered.
A MAC is also referred to as a tag, as it is a shorter piece of authentication data added to the message it is verifying.
How a MAC works
Symmetric key cryptographic techniques are used to generate MACs for individual messages. The process requires a standard MAC algorithm that takes two inputs: the original message and a secret key known only to the message originator and its intended recipient. The following image provides an overview of how a sender generates a MAC and how it is verified by the receiver.
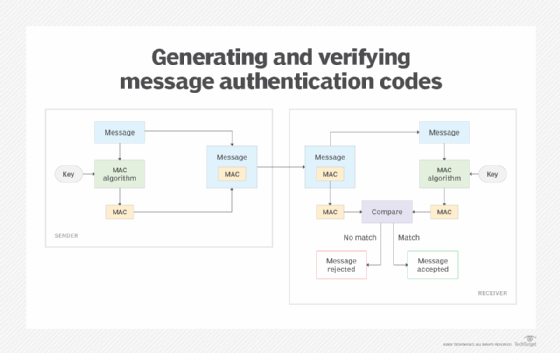
MAC-based message verification requires both the sender and receiver to address the following specific steps to ensure the message's credibility:
- The sender and receiver share a secret symmetric key.
- The sender runs a standard algorithm to create the MAC. As input, the algorithm takes the original message and the secret key.
- The algorithm combines the message and secret key and generates a fixed-length checksum from this content, which is used to create the MAC.
- The sender appends the MAC to the message and transmits both to the receiver.
- When the sender receives the message and MAC, it runs the MAC algorithm using the transmitted message and shared secret key as input.
- The algorithm combines the message and secret key and, from this content, generates a fixed-length checksum that is used to create its own MAC.
- The receiver compares the sender's MAC against its own MAC. If they match, the receiver accepts the message. If the two MACs do not match, the receiver rejects the message.
When the two MACs match, the receiver knows the message came from the legitimate sender and was not altered when transmitted between the sender and the receiver. If the sender and receiver are not using the same secret key or if the message content is different between the sender and receiver, the MAC values will not match, and the receiver will reject the message.
Although a MAC ensures authenticity and integrity, it does not protect the message data itself. That is not its purpose. For data protection, the message needs to be encrypted in a separate process.
Types of message authentication codes
MACs that can be categorized into different types, including the following:
- One-time MAC. A one-time MAC is designed for a single message per key and is normally characterized by having strong security and fast computation.
- Keyed-Hash MAC. An HMAC uses a cryptographic hash function and two keys to generate a MAC.
- Universal Hash-based MAC. A UHF-MAC uses mathematical universal hashing techniques to authenticate and process a message. It is notable for its speed.
- Carter-Wegman MAC. This MAC provides a way to authenticate long messages. It can process parts of a message in parallel and only needs to call a cryptographic function once per message. The Carter-Wegman MAC is a specific type of UHF-MAC.
- Block Cipher-based MAC. This type of MAC uses a symmetric block cipher to process parts of a message in blocks, which is useful for longer messages.
- Parallelizable MAC. A PMAC is based on block ciphers and is designed to improve speed and efficiency by enabling each block to be processed in parallel. It is a specific type of block cipher-based MACs.
Approved message authentication code algorithms
MAC generation requires a general-purpose algorithm that can securely generate the cryptographic checksum needed to create the MAC. There are multiple algorithms available for MAC creation; however, the National Institute of Standards and Technology (NIST) has approved only the following three algorithms:
HMAC
The HMAC cryptographic authentication technique uses a secret key in conjunction with a hash function approved by the Federal Information Processing Standards (FIPS). Because different hash functions can be used, multiple implementations of HMAC exist, such as HMAC-SHA256 and HMAC-SHA3-256. Multiple communication and transfer protocols use HMAC, including Hypertext Transfer Protocol Secure File Transfer Protocol Secure and Secure File Transfer Protocol.
Keccak message authentication code
A keyed hash function based on Keccak, KMAC is a cryptographic hash function that can also be used for authentication, encryption and pseudo-random number generation. There are two variants of Keccak, KMAC128 and KMAC256. Keccak is specified in the FIPS 202, SHA-3 Standard: Permutation-Based Hash and Extendable-Output Functions.
CMAC mode for authentication
The cipher-based message authentication code (CMAC) standard defines a block cipher-based MAC algorithm for ensuring authenticity and integrity. According to NIST, CMAC can be considered a mode of operation of the block cipher, providing an "algorithm for the cryptographic transformation of data that features a symmetric key block cipher."
NIST also provides testing requirements and validation lists for the approved algorithms through its Cryptographic Algorithm Validation Program.
Benefits of MACs for businesses
MACs provide several benefits, including the following:
- Data integrity. MACs help ensure that unauthorized code has not been added to a message and that the message has not been tampered with.
- Authentication. MACs verify that a message originates from the authenticated sender who possesses the secret key.
- Lightweight. MACs are lightweight and efficient, as they are small tags of code that attach to a message.
Challenges and limitations of MACs
MACs do, however, have the following limitations:
- Complex key management. To generate and verify a MAC, the sender and the recipient must both have the same secret key. This can be complex in large-scale systems.
- No protection. Although a MAC ensures authenticity and integrity, it does not protect the message itself. A separate encryption process needs to be used for security.
- No repudiation. MAC does not offer nonrepudiation capabilities, meaning there is no way to prove who created the original message.
MACs vs. digital signatures
Message authentication codes and digital signatures are similar in concept, as both ensure message authenticity and integrity.
However, the most notable difference is that digital signatures are asymmetric, meaning that they use a pair of keys -- the sender signs their message with one key and the receiving party accesses the message with the other. MACs, by comparison, use a single shared secret key for both parties.
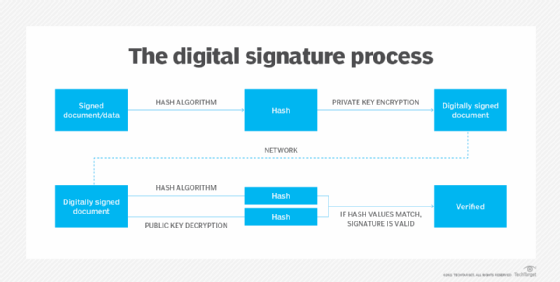
This also means that a digital signature offers nonrepudiation, which provides a record of a document's origin. With a MAC, there is no way to prove who created the original message.
Explore how MAC and HMAC use hash function encryption to authenticate messages and the differences between symmetric vs. asymmetric encryption algorithms.






