What is a block cipher?
A block cipher is a method of encrypting data in blocks to produce ciphertext using a cryptographic key and algorithm. The block cipher processes fixed-size blocks simultaneously, as opposed to a stream cipher, which encrypts data one bit at a time. Most modern block ciphers are designed to encrypt data in fixed-size blocks of either 64 or 128 bits.
Characteristics of block ciphers
Block ciphers are invertible symmetric key cryptographic algorithms. Here, symmetric means that the same cryptographic key is used to both encrypt and decrypt messages. The key is used to transform (encrypt) one block of information at a time.
Block cipher algorithms take in input of some fixed-size (fixed-length) blocks and produce a ciphertext output block that has the same length as the input block. Another characteristic of block ciphers is that the strength of encryption scheme is not affected by the size of the block, which remains fixed for a given scheme. Rather, the strength depends on the key length.
That said, blocks of small size are usually not used due to security concerns. If the block is too small, it may allow attackers to build a dictionary of plaintext/ciphertext pairs sent using the cipher's encryption key in order to execute dictionary attacks. A larger block size makes it harder to compile such dictionaries, thus minimizing the potential for attack. On the other hand, a block that's too large can make the cipher inefficient and difficult to manage. For these reasons, it's important to use blocks of the right length. Since most computers handle data in multiples of 8 bits, it's usually best to use blocks of such multiples to provide both security and efficiency.
Different modes of operation are available for block ciphers. Electronic codebook (ECB) and cipher block chaining (CBC) are two of the oldest modes. Popular block cipher schemes include Data Encryption Standard, Triple DES (3DES), Advanced Encryption Standard (AES) and Twofish.
How does a block cipher work?
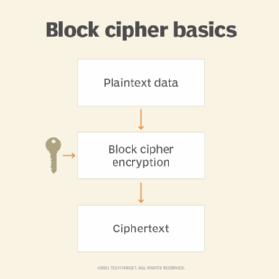
A block cipher uses a symmetric key and algorithm to encrypt and decrypt a block of data whose length remains fixed. The block size of a block cipher refers to the number of bits that are processed together.
All block ciphers require an initialization vector (IV) -- a random binary value that is added to the input plaintext to initialize the algorithm. The IV is derived from a random number generator, which is combined with text in the first block and the key to ensure all subsequent blocks result in ciphertext that does not match that of the first encryption block. In other words, the same plaintext message encrypted with the same key results in different ciphertext output -- as long as different IVs are used.
The IV, which does not need to be secret but must be random and unpredictable, increases the keyspace of the cipher and makes it more difficult for an attacker to use brute force to break the key and compromise the cipher. By making it harder to identify patterns in the ciphertext, the IV increases security and helps prevent dictionary attacks and other types of cyberattacks.
Here's how a block cipher works:
- It breaks down the plaintext input into blocks of fixed length, e.g., 64 bits or 128 bits.
- If the plaintext length is not a multiple of the block size, it is padded with redundant information to provide a complete final block.
- Each block is encrypted using the cipher key.
- The ciphertext is generated by connecting the encrypted blocks.
- The message recipient receives the same key and uses it to decrypt the message into the original plaintext.
What are the different modes of operation in block ciphers?
Block ciphers only encrypt messages that are the same size as their block length, so each block of plaintext with more or less blocks needs to be encrypted separately. The following block cipher modes of operation define how these blocks are encrypted.
Electronic codebook mode
ECB mode is used to electronically code messages as their plaintext form. It is the simplest of all block cipher modes of operation. It does not add any randomness to the key stream, and it is the only mode that can be used to encrypt a single-bit stream. This means that each plaintext symbol, such as a character from the plaintext alphabet, is converted into a ciphertext symbol using the cipher's key and a substitution alphabet. Each plaintext block is encrypted independently of all the other blocks. If a plaintext block is only 8 bytes, only 8 bytes of the key are used; if a plaintext block is 100 bytes, all 100 bytes of the key are used.
With ECB, a plaintext block always results in the same ciphertext block, given the same key. This direct relationship between plaintext and ciphertext makes ECB vulnerable to cryptanalysis and other types of attack. On the positive side, ECB is one of the simplest block ciphers. It is also fast since it supports parallel encryption.
Cipher block chaining mode
In CBC mode, each block of plaintext is combined, or chained, with the previous ciphertext block before being encrypted. This symmetric key algorithm creates a ciphertext that depends on all plaintext blocks processed before it in a data stream, ensuring that each ciphertext block is dependent on all the previous blocks. Each plaintext block is XORed (exclusive OR) with the previous ciphertext block before being encrypted with the cipher algorithm.
To decrypt the message, the inverse of the encryption algorithm is applied to the first ciphertext block, and this block is XORed with the IV to get the first plaintext block. This process continues until the entire message is decrypted. CBC mode is used in a variety of security applications. One example is Secure Sockets Layer/Transport Layer Security, which is used to encrypt and secure data transferred over the internet.
Ciphertext feedback mode
In contrast to CBC mode, which encrypts a set number of bits of plaintext at a time, it is sometimes necessary to encrypt and transfer plaintext values instantly, one at a time. For this, cipher feedback mode is used. Like CBC, CFB also uses an IV. However, unlike CBC, CFB uses a fraction of the previous block to compute the next block. Additionally, it uses a block cipher as a component of a random number generator. The previous ciphertext block is encrypted, and the output is XORed with the current plaintext block to create the current ciphertext block.
As with CBC, the XOR operation in CFB conceals plaintext patterns, making cryptanalysis difficult. The downside of CFB is that errors can propagate downstream if a byte is received with an error. Also, both CBC and CFB cannot perform encryption in parallel.
Output feedback mode
Output feedback (OFB) mode can be used with any block cipher and is similar to CBC mode. However, it is less likely to produce transmission errors than CFB.
OFB uses a feedback mechanism, but instead of XORing the previous block of ciphertext with the plaintext before encryption, the previous block of ciphertext is XORed with the plaintext after it is encrypted. This process is repeated for the entire length of the message. OFB requires that the IV, which is encrypted with the encryption algorithm to produce the output block, be unique for each execution for a given key.
Counter mode
Counter (CTR) mode uses unique input blocks known as counters to which the encryption algorithm is applied. The encryption process is performed by XORing the plaintext with a sequence of pseudorandom values, each of which is generated from the ciphertext using a feedback function. The process can be visualized as a series of XORs between blocks of plaintext and corresponding blocks of ciphertext. Decryption follows a similar pattern as encryption, with the counter being encrypted with the algorithm, followed by the output being XORed with the corresponding ciphertext block. This then results in the plaintext block. CTR is as secure as CBC, CFB and OFB. It is also fast and can execute both encryption and decryption in parallel.
Block cipher schemes: DES and AES
DES and AES are both symmetric block cipher schemes, meaning they use only one key for data encryption and decryption. DES was originally designed by IBM in 1975 and consisted of 64-bit blocks and a 56-bit key. Its key size is now considered too short for today's cybersecurity and information security, which is why this cipher is no longer considered secure.
Variations of DES include Double DES and 3DES.
Double DES uses two instances of DES on the same plaintext and two keys to encrypt the plaintext. Since the algorithm is performed twice and the length of the key is doubled, Double DES is more secure than the original DES scheme. Specifically, it is more resistant to brute-force attacks in which attackers attempt to decrypt encrypted data. However, the scheme is vulnerable to meet-in-the-middle attacks in which attackers try to intercept the ciphertext and try each key for every encryption stage until they can decrypt the data.
First introduced in 1998, 3DES uses three versions of DES to encrypt the same plaintext. In other words, it runs the algorithm three times over the same data block. Three 56-bit keys are used: the first for encryption, the second for decryption and the third for final encryption. This is why 3DES is said to use encrypt-decrypt-encrypt operations. 3DES is more secure than DES and Double DES. However, it is slower and less secure than other algorithms like AES. Also, its triple encryption process requires more computing power.
AES uses a 128-bit block size and a 128-, 192- or 256-bit key size. The longer keys make AES much more secure than DES and its variants. Designed to replace DES, the AES standard was published by the National Institute of Standards and Technology in 2001. Today, AES is widely used for data security applications, including databases, web browsers, wireless systems and virtual private networks.
Authenticated encryption with additional data modes
The following modes provide message encryption and can supply additional data, including sequence number or header, that is not included in the ciphertext:
- Galois/Counter Mode. In GCM mode, blocks are combined with an IV and encrypted with AES. The result is then XORed with the plaintext to generate the ciphertext.
- Counter Mode with CBC Message Authentication Code Protocol. CCMP mode is for use with AES. It uses a 128-bit block size and a 128-bit key size and is capable of handling messages up to 16 bytes. CCMP mode was designed to address some of the problems with the CBC mode of operation in which the same block of plaintext can encrypt to different ciphertexts.
- Synthetic IV. SIV is a byte-oriented (8-bit) substitution-permutation network AES algorithm. It takes a plaintext message and a secret key and encrypts the plaintext into ciphertext. However, it differs from other cipher modes in that it does not use a random key stream; instead, it uses a fixed key stream that is generated from a pseudorandom number generator.
- AES-GCM-SIV. AES-GCM-SIV is a combination of the AES block cipher and GCM, with the added security feature of SIV. This enables more messages to be encrypted with the same key than with GCM-SIV.
See best practices for wireless network security, tips for managing guest wireless network access and how the Wi-Fi Protected Access 3 security protocol simplifies logins and secures the internet of things. Learn why experts warn cryptography techniques must keep pace with threats and about the importance of security and data encryption in the cloud. Also, explore what quantum computers mean for cryptography.





