What is Data Encryption Standard (DES)?
Data Encryption Standard (DES) is an outdated symmetric key method of data encryption. It was adopted in 1977 for government agencies to protect sensitive data and was officially retired in 2005.
IBM researchers originally designed the standard in the early 1970s. It was then adopted by the U.S. National Bureau of Standards -- now the National Institute of Standards and Technology, or NIST -- as an official Federal Information Processing Standard (FIPS) in 1977 for the encryption of commercial and sensitive yet unclassified government computer data.
DES was the first encryption algorithm the U.S. government approved for public disclosure. This move ensured it was quickly adopted by industries, such as financial services, that needed strong encryption. Because of its simplicity, DES was also used in a variety of embedded systems, including the following:
- smart cards
- SIM cards
- modems
- routers
- set-top boxes
How does DES work?
DES uses the same key to encrypt and decrypt a message, so both the sender and the receiver must know and use the same private key. DES was once the go-to, symmetric key algorithm for the encryption of electronic data, but it has been superseded by the more secure Advanced Encryption Standard (AES) algorithm.
Some key features affecting how DES works include the following:
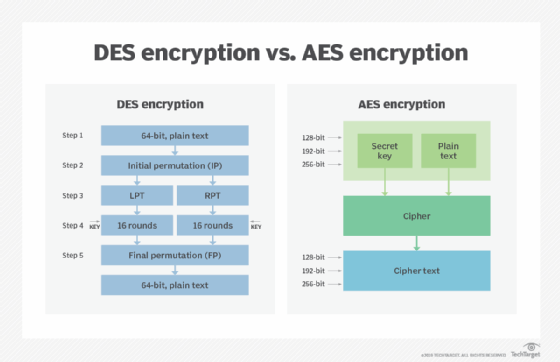
- Block cipher. The Data Encryption Standard is a block cipher, meaning a cryptographic key and algorithm are applied to a block of data simultaneously rather than one bit at a time. To encrypt a plaintext message, DES groups it into 64-bit blocks. Each block is enciphered using the secret key into a 64-bit ciphertext by means of permutation and substitution.
- Several rounds of encryption. The DES process involves encrypting 16 times. It can run in four different modes, encrypting blocks individually or making each cipher block dependent on all the previous blocks. Decryption is simply the inverse of encryption, following the same steps but reversing the order in which the keys are applied.
- 64-bit key. DES uses a 64-bit key, but because eight of those bits are used for parity checks, the effective key length is only 56 bits. The encryption algorithm generates 16 different 48-bit subkeys, one for each of the 16 encryption rounds. Subkeys are generated by selecting and permuting parts of the key as defined by the DES algorithm.
- Replacement and permutation. The algorithm defines sequences of replacement and permutation that the ciphertext undergoes during the encryption process.
- Backward compatibility. DES also provides this capability in some instances.
Why is DES unsafe?
For any cipher, the most basic method of attack is brute force, which involves trying each key until you find the right one. The length of the key determines the number of possible keys -- and hence the feasibility -- of this type of attack.
The effective DES key length of 56 bits would require a maximum of 256, or about 72 quadrillion, attempts to find the correct key. This is not enough to protect data with DES against brute-force attempts with modern computers.
Few messages encrypted using DES before it was replaced by AES were likely subjected to this kind of code-breaking effort. Nevertheless, many security experts felt the 56-bit key length was inadequate even before DES was adopted as a standard. There have always been suspicions that interference from the National Security Agency weakened the original algorithm.
DES remained a trusted and widely used encryption algorithm through the mid-1990s. However, in 1998, a computer built by the Electronic Frontier Foundation (EFF) decrypted a DES-encoded message in 56 hours. By harnessing the power of thousands of networked computers, the following year, EFF cut the decryption time to 22 hours.
Currently, a DES cracking service operated at the crack.sh website promises to crack DES keys, for a fee, in about 26 hours as of this writing. Crack.sh also offers free access to a rainbow table for known plaintexts of 1122334455667788 that can return a DES key in 25 seconds or less.
Today, reliance on DES for data confidentiality is a serious security design error in any computer system and should be avoided. There are much more secure algorithms available, such as AES. Much like a cheap suitcase lock, DES will keep the contents safe from honest people, but it won't stop a determined thief.
Successors to DES
Encryption strength is directly tied to key size, and 56-bit key lengths have become too small relative to the processing power of modern computers. So, in 1997, NIST announced an initiative to choose a successor to DES and undertook a five-year evaluation process of 15 encryption algorithms. In 2001, NIST selected the Rijndael cipher, and with some tweaks, it became the new AES.
Data Encryption Standard (FIPS 46-3) was officially withdrawn in May 2005. Triple DES (3DES), a variant of DES that can use up to three different keys for greater effective key length, has also been deprecated. 3DES performs three iterations of the DES algorithm; the strongest version of 3DES uses a different key for each iteration, increasing the effective key length to 168 bits. However, due to the likelihood of a meet-in-the-middle attack, the effective security it provides is only 112 bits. 3DES encryption is slower than plain DES.
How is DES used today?
As deprecated standards, both the DES and 3DES algorithms and key lengths could still be used. However, users must accept that there is a security risk in using the deprecated algorithm and key length and that the risk will increase over time.
DES is no longer trusted for encrypting sensitive data. Before it was deprecated and eventually disallowed, the standard was required for U.S. government financial transactions that used electronic funds transfer. It became the default encryption algorithm used in financial services and other industries.
DES and 3DES continue to be used in limited ways.
3DES. NIST guidance for 3DES will change to disallowed in 2023. At that point, the algorithm and key length will not be used for cryptographic protection.
Cryptographic training. DES and its variants continue to be used today for teaching about cryptography. The algorithms are well understood, and there is a significant body of research into both how effective DES can be and how to effectively attack it. The technology is still used in academia to demonstrate the fundamentals of digital cryptography, including the following:
- substitution and permutation of ciphertexts;
- techniques for applying keys and how to find them; and
- exploiting weaknesses in cryptographic algorithms.
Legacy of DES
Despite having reached the end of its useful life, the arrival of Data Encryption Standard served to promote the study of cryptography and the development of new encryption algorithms. Until DES, cryptography was a dark art confined to military and government intelligence organizations.
The open nature of DES has meant academics, mathematicians and anyone interested in data security could study how the algorithm worked and try to crack it. As with any popular and challenging puzzle, a craze -- or, in this case, a whole industry -- was born.
Learn more about the basics of cryptography and symmetric key encryption in this excerpt from Computer Security Fundamentals by Chuck Easttom.




