What is the Twofish encryption algorithm?
Twofish is a symmetric-key block cipher with a block size of 128 bits and variable-length key of size 128, 192 or 256 bits. This encryption algorithm is optimized for 32-bit central processing units and is ideal for hardware and software environments. It is open source (unlicensed), unpatented and freely available for use. Twofish is similar to an earlier block cipher, Blowfish. It also includes advanced functionalities to replace the Data Encryption Standard (DES) algorithm.
Understanding Twofish
Twofish is a symmetric encryption algorithm that uses a single key to encrypt and decrypt data and information. It accepts the key along with the plaintext information. This key then turns the information into ciphertext, which cannot be understood without decoding. The encrypted data is sent to the recipient along with the encryption key, either after the ciphertext or with it. The user can use this key to decrypt the encrypted information.
Although not considered an advanced encryption standard, Twofish does provide a more efficient and secure alternative to the DES algorithm. One reason is its block size of 128 bits, which makes it resistant to brute-force attacks. Another is its complex key schedule with support for multiple key sizes.
Twofish architecture
Twofish consists of a number of building blocks, such as the following:
- Feistel network. A method of transforming any function (F function) into a permutation that forms the basis of many block ciphers.
- S-boxes. Table-driven, nonlinear substitution operations. Twofish uses four precomputed, key-dependent, bijective, 8-by-8-bit S-boxes. They are commonly used in block ciphers.
- Maximum distance separable (MDS) matrices. A common feature of Reed-Solomon error-correcting codes. Twofish uses a single 4-by-4 MDS matrix over Galois field (28) for computations.
- Pseudo-Hadamard transform (PHT). Simple mixing operation that runs quickly in software. Twofish uses a 32-bit PHT to mix the outputs from its two parallel 32-bit g functions.
- Whitening. The technique of XORing key material before and after the first and last rounds, respectively. Twofish XORs 128 bits of subkey before the first Feistel round and after the last Feistel round.
- Key schedule. The means by which key bits are transformed into round keys that the cipher can use. Twofish has a complicated key schedule, which contributes to its security capabilities.
How Twofish works
Twofish is a 128-bit symmetric block cipher that splits plaintext into four 32-bit words. These words are XORred with four keywords -- a step known as input whitening. Sixteen rounds then follow, with the two words on the left used as input to the g functions (four byte-wide key-dependent S-boxes followed by linear mixing based on an MDS matrix) in each round.
Next, a PHT combines the results of the two g functions. One of the words on the right is rotated left by 1 bit, while the other is rotated right afterward. Following this, the two results (of adding the two keywords) are XORed into the words on the right.
The left and right halves are swapped for the next round. Once all the rounds are complete, the swap of the last round is reversed. This step is known as output whitening. Finally, the four words are XORed with four more keywords to produce the ciphertext, whose four words are written as 16 bytes. The same little-endian conversion used for the plaintext is also used to write the ciphertext.
In sum, the encryption process in Twofish includes the following steps:
- Twofish breaks the input plaintext into 128-bit blocks that are then divided into 32-bit words.
- In each round, two 32-bit words act as inputs into the F function. This function, a key-dependent permutation on 64-bit values, also takes the round number r used to select appropriate subkeys as input. The subkeys generated from the main key are used to whiten each 32-bit word.
- Each word is broken up into 4 bytes, which are then sent through four key-dependent S-boxes. These S-boxes have 8-bit input/output (I/O).
- The MDS matrix combines the 4 output bytes into a 32-bit word.
- The two 32-bit words are combined using a PHT.
- Finally, they are added to two round subkeys and XORed into the right half.
Key features of the Twofish algorithm
One key characteristic that distinguishes Twofish from some other encryption algorithms is that it uses a 16-round Feistel-like structure. This means that the input data is split into equal blocks, and each block is processed through multiple encryption rounds. Also, the operations for encryption and decryption are similar and use an invertible Feistel round function to return an output that is the same size as the data block.
Another unique feature of Twofish is that it uses precomputed, key-dependent S-boxes. The S-box, which takes in 8 bits of input and produces 8 bits of output, obscures the relationship of the key to the ciphertext. Further, the S-box is already provided but depends on the cipher key to decrypt information. The input to the S-boxes is a counter.
A complex key schedule, another characteristic of Twofish, is designed to provide higher resistance to attack in addition to enhanced implementation flexibility. The algorithm is defined for keys of length 128 bits, 192 bits, and 256 bits but can accept keys of any length up to 256 bits. Keys that are shorter than 256 bits can also be used. However, they must be padded with zeroes until the next larger defined key length. With Twofish, key scheduling can be done on the fly during encryption, providing high key agility and allowing for low-memory implementations.
Finally, Twofish "whitens" both the input and output. During input whitening, the four 32-bit words into which the plaintext is split are XORed with four keywords. And during output whitening, the swap of the last round is reversed, and the data words are XORed with four words of the expanded key, resulting in the 16-byte ciphertext.
The security of Twofish
With a 128-bit block size and variable-length encryption key, Twofish is one of the most secure encryption protocols. In theory, its high block size means that Twofish is safe from brute-force attacks since such an attack would require tremendous processing power to decrypt a 128-bit encrypted message.
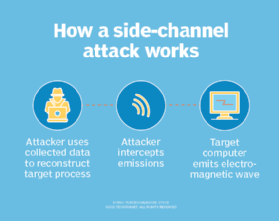
It is argued that the precomputed, key-dependent S-boxes used in Twofish are vulnerable to side-channel attacks -- in which threat actors might exploit information leaked from a channel (such as an application) to understand the algorithm's cryptographic processes and weaken its security. However, it is possible to minimize the risk of such attacks by adding randomness to the encryption process or by introducing noise into cryptographic operations. Both can help prevent adversaries from leveraging leaked side-channel information to deduce and exploit the operations.
The larger size of the encrypted data also makes Twofish secure. When different encryption algorithms are compared in terms of plaintext size after encryption, Twofish converts 240 KB of plaintext information into a massive 955 KB. Only Blowfish can match Twofish in this aspect. Even the Advanced Encryption Standard (AES) algorithm is limited in that it can convert 250 KB of plaintext into a maximum encrypted size of 847 KB. The only problem with this large size is that it can slow down program execution, especially if the algorithm is applied to massive quantities of plaintext data.
Main advantages and disadvantages of Twofish encryption
As previously stated, one of the main advantages of Twofish encryption is security. The cipher's complexity, block size and key length provide strong protection in a wide range of applications. Also, support for multiple key lengths provides the flexibility needed to implement the algorithm for differing security requirements.
Another advantage is its democratic nature. Since there is no patent or license, Twofish can be freely implemented by anyone for almost any kind of application.
On the flip side, Twofish's complexity can be a disadvantage. Since it can be resource-intensive and require a lot of computational overhead, it can be hard to implement the algorithm for low-power devices. Speed can also be a limiting factor when Twofish is implemented in apps with limited resources.
Twofish applications
Although Twofish is not as popular as AES, it is still used by several popular products. Among these are the following:
- GNU Privacy Guard (GnuPG). A free implementation of OpenPGP to encrypt and sign communications and data. GnuPG provides access modules to access public key directories and a versatile key management system.
- 96Crypt. An encryption/decryption/steganography program for files and folders. It uses Twofish (and other block ciphers) plus multiple collision-resistant HMAC-HASH algorithms to provide high levels of data confidentiality and integrity.
- KeePass. An open-source password manager that securely stores all passwords in a single Twofish encrypted database and requires only a single master key to unlock the entire database
- PeaZip. A free archiver and file manager utility that supports multiple file formats (read/write) to provide an all-purpose ZIP utility. It also supports the ARC archive format with Twofish256 for efficient and secure compression.
Twofish vs. Blowfish
Both Twofish and Blowfish are block ciphers in which input plaintext data is encrypted in fixed-length blocks. They are also based on the Feistel network structure in which the fixed-length blocks of input data go through multiple processing rounds before the ciphertext is produced. Also, both symmetric ciphers, meaning the same key is used for both encryption and decryption processes. Another similarity is that they are both unpatented and free to use.
A major difference between Twofish and Blowfish is the block size. Where Blowfish uses a 64-bit block size, Twofish uses a 128-bit block size. This 2X increase makes Twofish more secure and harder to crack than Blowfish. Twofish is a particularly good choice over Blowfish if the risk of birthday attacks is high.
That said, Blowfish has the advantages of speed and simplicity over Twofish, which explains why it remains popular for many applications, such as bulk encryption and password managers. The complexity of Twofish also makes it harder to implement for applications with few (or limited) computing resources. That said, Twofish provides strong security benefits that make it a better choice for applications where protection from attacks is a high priority.
Twofish vs. AES
Both Twofish and Rijndael AES offer similar security benefits. However, AES beats Twofish in terms of simplicity. Since it uses a fixed block size and offers a choice between three key lengths, AES has a simpler design, making it easier to implement.
Also, its simple key schedule and use of a substitution-permutation network make it faster than Twofish which uses a complex key schedule. The speed differences can be particularly visible on low-power devices that lack the resources needed to properly implement and run Twofish.
In terms of efficiency, both Twofish and AES are considered efficient. Twofish is efficient on various software and hardware platforms. The same goes for AES. However, since AES offers more optimal use of computational resources, it might have a slight edge over Twofish on the efficiency scale for certain applications.
As internal and external cyber threats increase, consider these tips to effectively protect and secure data at rest, in use and in motion.






