encryption key management
What is encryption key management?
Encryption key management is the practice of generating, organizing, protecting, storing, backing up and distributing encryption keys.
The need for encryption key management
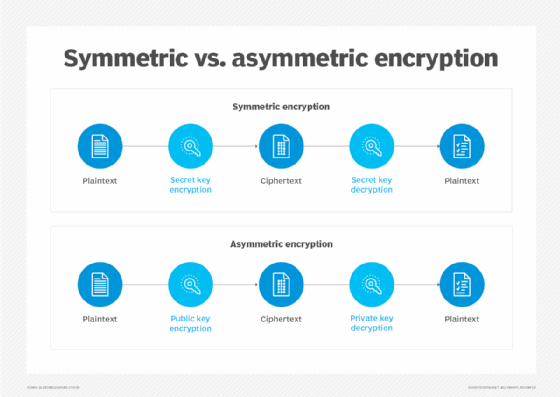
High-profile data losses and regulatory compliance requirements have caused a dramatic increase in the use of encryption to protect data in the enterprise. Encryption is the process of applying complex algorithms to data and then converting that data into streams of seemingly random alphanumeric characters. There are two basic types of cryptographic algorithms: symmetric, or private key, and asymmetric, or public key.
To protect their data and business-critical assets, enterprises might use many different and possibly incompatible encryption tools, resulting in the use of thousands of encryption keys. Each key must be securely generated and stored, because if an unauthorized or malicious user gains access to a key, they could be able to decrypt the encrypted data and then use that data for their own purposes.
In addition, the distribution of encryption keys must be controlled, and any losses or compromises must be addressed quickly and appropriately. It's also vital to ensure that each key is easily retrievable by authorized users.
To effectively manage all these aspects, encryption key management is vital. With an effective encryption key management system, organizations can efficiently generate, store, use, organize and manage their encryption keys. That's why encryption key management must be part of the enterprise data encryption and data protection strategy.
Best practices for encryption key management
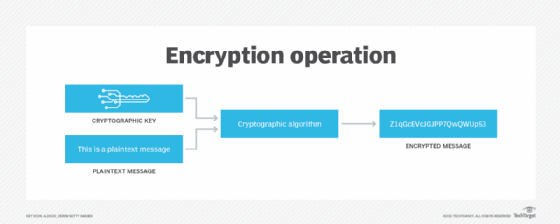
Key management means protecting every encryption key from loss, corruption and unauthorized access throughout its lifecycle. Many processes can be used to control key management, including changing the keys regularly as well as managing how keys are assigned and who is authorized to get them. In addition, organizations must evaluate whether one key should be used for all data types or if each type should have its own key. They must also rotate keys to minimize the chances of keys being stolen or compromised because they've been used for a long time.
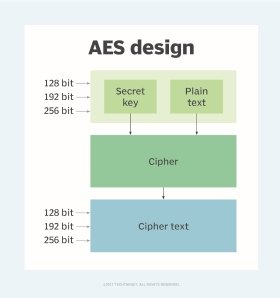
To generate secure encryption keys, it's important to use secure methods such as Advanced Encryption Standard (AES) encryption algorithms and random number generators. Also, the keys must not be hardcoded into any program code and must be securely distributed to authorized users only via secure connections.
Secure storage is vital so that the encryption keys can be reused for decryption more than once. A hardware security module (HSM) provides one of the most secure methods for encryption key storage. Keys can also be securely stored in the cloud using a cloud service provider's key management service. Ideally, deactivated keys should also be stored in a secure archive to enable the later decryption of encrypted data that uses those keys.
Having more than one person in charge of storing, backing up, referencing and rotating encryption keys is essential. The roles of key players should be defined, and the encryption key management policy should be accessible to everyone on an internal or intranet site. The policy should clearly state the methods and practices used in the organization to track key generation, access and use.
Encryption key management standards
The best-known encryption key management standard is the Key Management Interoperability Protocol (KMIP), developed by vendors and submitted to OASIS, the Organization for the Advancement of Structured Information Standards. The goal of KMIP is to allow users to attach any encryption device to a key management system.
KMIP enables and simplifies key lifecycle management. It can be used by both legacy and new cryptographic applications and works with many types of keys, including symmetric and asymmetric keys, authentication tokens, and digital certificates.
Recent advancements in encryption key management
AWS Key Management Service enables users to create and manage cryptographic keys that protect data in the Amazon Web Services cloud. These keys can also be used in cryptographic operations, such as to sign and verify messages, generate hash-based message authentication codes, and generate random numbers for specific applications. Each key is protected and validated using HSMs. Organizations can track and audit their AWS keys for regulatory and compliance purposes via AWS CloudTrail.
AWS encryption keys are generally used in a single region. For example, data encrypted in one region would be encrypted with a different key than a replicated version of that data stored in a different region.
Learn more about how end-to-end encryption works to keep data secure. See how to use a public key and private key in digital signatures and how to use centralized encryption methods in large-scale IT environments. Explore our comprehensive guide to data security.






