
blackboard - stock.adobe.com
How to use the John the Ripper password cracker
Password crackers are essential tools in any pen tester's toolbox. This step-by-step tutorial explains how to use John the Ripper, an open source offline password-cracking tool.
What is John the Ripper?
John the Ripper is an offline password cracking tool that was developed in 1996 by Openwall Project. It is notable for supporting a diversity of password formats. This tool enables security practitioners to crack passwords, regardless of encrypted or hashed passwords, message authentication codes (MACs) and hash-based MACs (HMACs), or other artifacts of the authentication process.

The tool is also notable for its ubiquity and accessibility. It's included in the default repositories for many Linux distributions, including Debian and Ubuntu, and installed by default in most penetration testing distributions, including Kali and BlackArch. A snap install of it is available, along with multiple container options in Docker Hub.
Simply put, John cracks passwords. It attempts to replicate the password-handling functionality of a target storage mechanism so that numerous password values can be attempted without relying on password validation.
Consider this simple example: Take a system that stores passwords in hashed form -- meaning, using a cryptographic hash or message digest -- instead of storing the password value. (Note: In an actual production context, this wouldn't be prudent due to security concerns associated with this approach, but we're keeping it simple for example purposes.) In this scenario, if you obtained the password hash database, you wouldn't know – yet -- users' passwords. The most straightforward way to find out what the passwords are would be to hash many passwords using the same algorithm and compare them to the values stored in the database. Doing this requires you have the stored password list or database, but it has the advantage that you don't have to attempt logins against the system directly -- you can work offline at your leisure.
How to use John the Ripper
Before using John the Ripper, one important note: We're using VMs to illustrate usage. In the case of this tool specifically, performance is important. Consider the relative advantages and disadvantages of using virtualization and the context. For example, you might find an IaaS where paying for CPU time can be an expensive proposition. Or you might get better performance running the tool on a host OS rather than a guest.
That aside, John is simple to use. At a minimum, you need to specify the stored password values you want to crack. If you provide no information other than that, the tool tries to figure out what format the stored values are in and assumes a set of constraints about what you might want to do. That said, in most cases, you should provide more information to allow the tool to operate most effectively.
Cracking modes
Consider which "cracking mode" you intend to use. You can specify your own externally defined modes. John also has built-in modes:
- Single crack mode uses information about the user, such as username or full name, from the supplied password values, where present, to attempt to build a short, highly focused dictionary of targeted passwords to crack.
- Wordlist mode operates via a wordlist, either user-supplied or a built-in one, and tries all the values in the wordlist.
- Incremental mode attempts to iterate through all possible character combinations according to adjustable length and complexity criteria -- for example, all strings between five and eight alphanumeric characters.
If you do not specify a mode, the tool tries them sequentially in the order listed above.
Password formats
While not necessary in every case, it's helpful to know the format passwords are stored in. This is because applications might manipulate formats in ways John might not expect -- a web application, for example, might Base64- or URL-encode values before storing them. It's also helpful because the built-in mechanisms used by John to determine type and format can be wrong. Consider two similar-in-format but vastly different values: an MD5 hash and an MD5 keyed hash. The outputs are identical in format, but the processes that led to the outputs are anything but. John wouldn't know the difference, unless you provide the missing information.
Examples
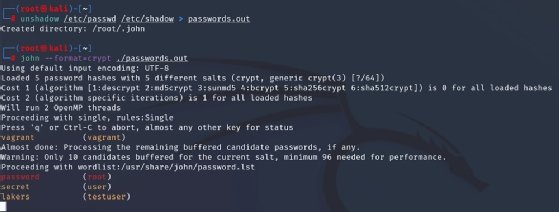
Figure 2 illustrates using the unshadow command. This is distributed with John the Ripper in most packages. It combines the contents of /etc/passwd and /etc/shadow on a Linux VM, in this case, Kali. Then, we used the john command and specified the format -- in this case, the crypt mechanism. Since we haven't told it what cracking mode to use, John begins with single crack and then proceeds to wordlist -- none was specified, so it used the default. Ultimately, it will move to incremental mode.
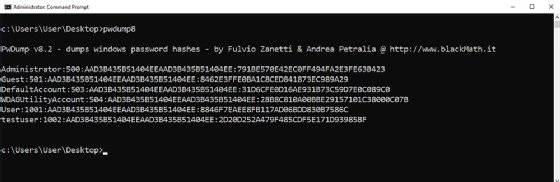
In a more complicated example, Figure 3 shows an attempt at cracking Microsoft Windows passwords. As with the Linux example, passwords must be put into a format John the Ripper can understand. To accomplish that, we used PwDump v8.2.
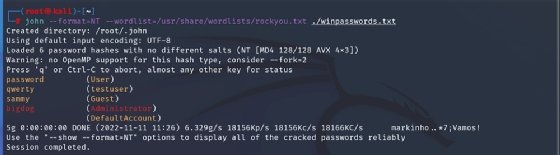
These values are fed into John the Ripper to crack in Figure 4. We specified wordlist mode and instructed it to use rockyou.txt, one of the built-in wordlists that comes by default with most security-focused Linux distributions. Note that you may need to extract the text file first. The passwords were set to weak values -- dictionary words in all cases -- to enable the cracking to complete quickly. These two examples demonstrate the most universally applicable and most basic usage of John the Ripper. For more advanced usage, you may need to get a little creative. Sometimes, the format of stored password values you can obtain are not in one of the formats supported by John out of the box. With a few clever modifications, however, you can convert to one of those with a little research.
At the end of the day, John the Ripper isn't the most complicated tool, but as you'll see with some experimentation, it is a true workhorse for red teamers, blue teamers and auditors alike.
Editor's note: It is possible to use John the Ripper -- and any password cracker -- lawfully and unlawfully. It is up to you to ensure your usage is lawful. Get the appropriate permission and approval before attempting to crack passwords, and handle the information obtained ethically. If you are unsure whether a given usage is lawful, do not proceed until you have confirmed that it is -- for example, by discussing and validating your planned usage with your organization's counsel.








