What is an attack surface? Examples and best practices
An attack surface is the total number of possible entry points and attack vectors an organization or system has that are susceptible to unauthorized access. It includes all vulnerabilities and endpoints that can be exploited to carry out a security attack.
For most modern businesses, the attack surface is complex and massive. The large number of devices, web applications and network nodes creates many potential cybersecurity threats.
Despite their best efforts, IT leaders can only see a subset of the security risks their organizations face. However, they should consistently monitor their organization's attack surface to help identify potential threats.
An attack surface's size can change over time as new systems and devices are added or removed. For example, the attack surface of an application could include the following:
- Admin interfaces.
- Application programming interfaces (APIs).
- Authentication entry points.
- Data.
- Data pathways.
- Interfaces with other applications.
- Local storage.
- User interfaces.
What are the different types of attack surfaces?
Attack surfaces can be physical, digital or social:
- Physical attack surfaces. These comprise all endpoint devices, such as desktop systems, laptops, mobile devices, hard drives and USB ports. This type of attack surface includes all the devices that an attacker can physically access. Likewise, this also includes improperly discarded hardware that contains user data and login credentials, passwords on paper or physical break-ins.
- Digital attack surfaces. These encompass applications, code, ports, servers, websites and unauthorized system access points. They are all the hardware and software that connect to an organization's network. Vulnerabilities caused by poor coding, weak passwords, default operating system settings, exposed APIs, outdated software or misconfigurations are all part of the digital attack surface.
- Social engineering attack surfaces. These relate to human vulnerabilities as opposed to hardware or software vulnerabilities. Social engineering is the concept of manipulating a person with the goal of getting them to share and compromise personal or company data. Therefore, an organization's social engineering attack surface is the number of authorized users who are susceptible to social engineering attacks. Phishing attacks are a well-known example of social engineering attacks.
What is attack surface management?
Attack surface management refers to the continuous surveillance and vigilance required to mitigate all current and future cyberthreats. It includes all risk assessments, security controls and security measures that go into mapping and protecting the attack surface, mitigating the chances of a successful attack. Attack surface management plays an important role in creating and managing a good security posture.
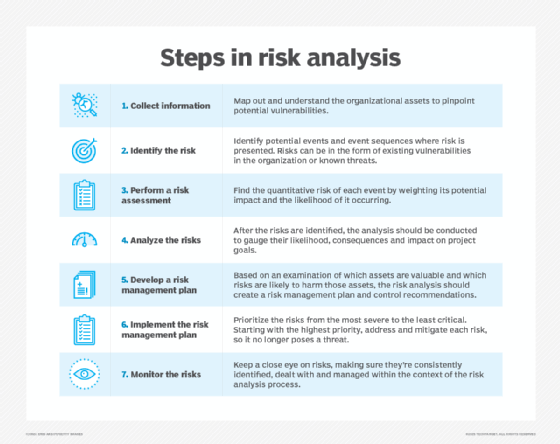
Key questions answered in attack surface management include the following:
- What are the high-risk areas and vulnerabilities in the system?
- Where can new attack vectors be created due to system changes?
- Who has access to each system?
- How can the system be protected from cyberattacks?
Organizations should continuously monitor attack surfaces for changes that could raise their risk of a potential attack. For example, an organization's internet-facing IT devices should be continually monitored for any changes and potential threats.
Attack surface management processes should also include risk assessments and prioritization, classifying risks according to their vulnerabilities and the real level of risk they pose.
Organizations can also use security methods, such as a zero-trust security policy, to manage and reduce their attack surface. Zero-trust policies -- such as continuous validation, continuous monitoring and least-privileged access -- can help reduce attack vectors.
Best practices to limit attack surfaces
Organizations can have information security experts conduct attack surface analysis and management. The following are some ideas for attack surface reduction:
- Control access. Organizations should limit access to sensitive data and resources, both internally and externally. They can use physical measures, such as locking access cards, biometric systems and multifactor authentication.
- Remove complexities. Unnecessary or unused software can result in policy mistakes, enabling bad actors to exploit these endpoints. All system functionalities must be assessed and maintained regularly.
- Scan regularly. Digital assets and data centers must be scanned regularly to spot potential vulnerabilities.
- Use network segmentation. Tools such as firewalls and strategies like microsegmentation can divide the network into smaller units.
- Remove impractical features. Removing unnecessary features reduces the number of potential attack surfaces.
- Train employees. Help employees avoid social engineering attacks, such as phishing, by training them.
- Prioritize risks. Assess and prioritize addressing risks based on their likelihood of attack and potential affect.
- Protect end users. Protect users on their devices using endpoint detection and response software.
- Implement zero-trust. To reduce attack vectors, implement a security model like zero-trust, where no users or devices are inherently trusted.
What is the difference between an attack surface and an attack vector?
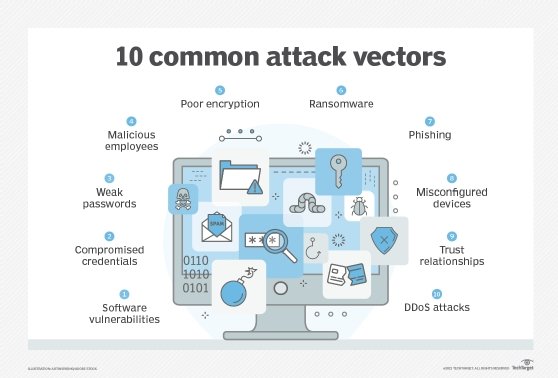
The term attack surface is often confused with the term attack vector, but they aren't the same thing. The surface is what's being attacked; the vector is how an intruder gains access. Some common attack vectors include the following:
- Cyberattacks. These are deliberate attacks cybercriminals use to gain unauthorized access to an organization's network. Examples include phishing attempts and malicious software, such as Trojans, viruses, ransomware or unethical malware.
- Network data interception. Network hackers might attempt to extract data such as passwords and other sensitive information directly from the network.
- Data breaches. Inside threats -- rogue employees, social engineering ploys such as phishing, and unauthorized users posing as service workers, for example -- can result in sensitive data being leaked to the public.
How to manage digital attack surfaces
Digital attack surfaces are all the hardware and software that connect to an organization's network. Managing these surfaces should include processes such as the following:
- Reducing the digital attack surface. To keep the network secure, network administrators must proactively seek ways to reduce the number and size of attack surfaces.
- Reducing the code being executed. A law of computing states that the more code running on a system, the greater the chance it will have an exploitable security vulnerability. One of the most important steps administrators can take to secure a system is to limit the amount of code being executed, which helps reduce the software attack surface.
- Using microsegmentation. Organizations can use microsegmentation to limit the size of attack surfaces. The data center is divided into logical units, each with its own unique security policies. The idea is to significantly reduce the surface available for malicious activity and restrict unwanted lateral -- east-west -- traffic once the perimeter has been penetrated. Policies are tied to logical segments, so any workload migration will also move the security policies. Network microsegmentation isn't new; however, its adoption has been sparked by software-defined networking and software-defined data center technologies. Traditional firewalls remain in place to maintain north-south defenses, while microsegmentation significantly limits unwanted communication between east-west workloads within the enterprise.
- Conducting regular security testing. Organizations should conduct regular security testing at potential attack surfaces and create an incident response plan to respond to any threat actors that might appear.
- Creating a policy for third-party risks. It's also important to create a policy for managing third-party risks that appear when another vendor has access to an organization's data. For example, a cloud storage provider should be able to meet an organization's specified security requirements, as using a cloud service or a multi-cloud environment increases the organization's attack surface. Similarly, internet of things devices also increase an organization's attack surface.

How to manage physical attack surfaces
A physical attack surface includes access to all endpoint devices, including desktop systems, laptops, mobile devices, USB ports and improperly discarded hard drives. Once an attacker has accessed a computing device physically, they look for digital attack surfaces left vulnerable by poor coding, default security settings or software that hasn't been updated or patched. Managing physical attack surfaces should include the following processes:
- Securing physical devices. Before walking away from an endpoint device, make sure it is locked. If in a public space, take the endpoint device with you.
- Monitoring physical locations. Organizations should monitor physical locations using surveillance cameras and notification systems, such as intrusion detection sensors, heat sensors and smoke detectors.
- Tightening physical security. Physical security includes three important components: access control, surveillance and disaster recovery (DR). Organizations should place obstacles in the way of potential attackers and harden physical sites against accidents, attacks or environmental disasters. Hardening measures include fencing, locks, access control cards, biometric access control systems and fire suppression systems.
- Testing DR processes regularly. Organizations should test DR policies and procedures regularly to ensure safety and to reduce recovery time from disruptive human-made or natural disasters.
- Educating employees on inside and external threats. Bad actors can exploit the physical attack surface through inside threats, including negligence and poor email hygiene. External threats include password retrieval from carelessly discarded hardware, passwords on sticky notes and physical break-ins.
What to consider when looking for an attack surface management tool
There are many available attack surface management tools, including Detectify, ManageEngine, Rapid7 and SentinelOne as a sampling. When choosing one of these tools, it's important to consider its features and the organization's requirements for risk reduction and integration with existing infrastructure.
Effective attack surface management tools should include the following:
- Automated asset discovery. Attack surface management tools should be able to continuously scan assets across cloud, on-premises and third-party environments for vulnerabilities.
- Compliance mapping. These tools should map findings with relevant compliance standards and frameworks.
- Integration with other tools. These tools should integrate well within an organization's existing systems and security tools.
- Real-time monitoring and alerting. These tools should feature continuous monitoring with real-time alerts attuned to detecting risks or vulnerabilities.
- Risk prioritization. These tools should be able to prioritize risks based on the likelihood of an attack, asset criticalness and potential exploitability.
Attack surface management programs should be set up as a continuous process. Learn how to implement an attack surface management program.