
kantver - Fotolia
Maze ransomware hit biggest target yet with LG breach
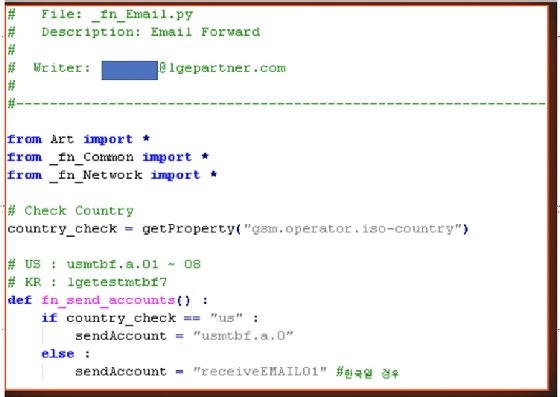
The operators of Maze ransomware claim to have breached LG, offering three screenshots as proof. One of those screenshots features LG product source code.
The operators of Maze ransomware claim to have breached its biggest victim yet, LG Electronics, which indicates a troubling trend for large enterprises.
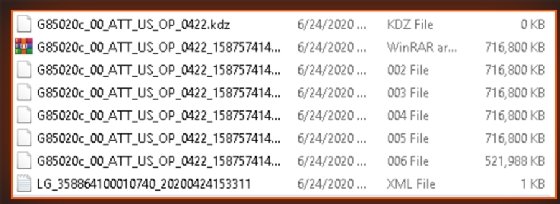
As proof of the breach, Maze released three screenshots. One of the screenshots appears to consist of LG Electronics official firmware or software update releases that assist their hardware, according to a blog post by Cyble, a cyber threat intelligence company.
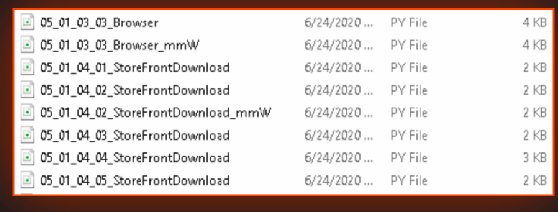
Another screenshot lists LG product source code, which was promised by Maze in their June 22 press release teasing the breach. The release was in large part a warning from the ransomware operators to victims regarding "the cost of non-cooperation." In other words, if a company doesn't pay up to Maze, there will be consequences.
Though some enterprises of note have been known victims of Maze, like Pitney Bowes and Cognizant, no known victim has come close in size to LG, which had a 2018 revenue of $54.398 billion. In Pitney Bowes' case, while hackers did breach and access data, they were stopped before the ransomware detonated. While most of Maze's victims consist of smaller organizations, LG's compromise (not to mention Pitney Bowes' and Cognizant's) indicates a trend that Maze's victims are getting larger and larger.
This is bad news, according to Cyble founder and CEO Beenu Arora, who also blogged about the breach. He said the ransomware group has funded themselves "quite well" recently, mainly due to successful ransomware attacks resulting from the growth of their affiliates and organizations "increasingly paying ransomware extortions." They're also able to acquire access and remote code execution vulnerabilities on the dark web for other potential enterprises. Even worse, they may be attracting more affiliates, which could lead to more attacks.
Arora said Maze's modus operandi is similar to other groups like REvil. For example, after Maze initially infiltrates a victim's network, often done so by obtaining information from other cybercriminal groups, "the group typically attempts to learn more about their victim's network and attempts to elevate its privileges to gain access to a large subset of the victim's systems."
Another key element is that if the victim fails to pay the ransom, Maze will leak and/or publish victim data on their websites to shame the victim.
Maze ransomware has been actively deployed since at least mid-2019.
LG did not respond to a request for comment.







