
alswart - stock.adobe.com
'Lives at stake': How ransomware impacts hospitals
Some ransomware gangs pledged to not target medical facilities during the COVID-19 pandemic, but hospitals are still getting hit. And the attacks affect more than just IT systems.
As COVID-19 spread across the globe in March, multiple ransomware operators stated that they would not target healthcare facilities like hospitals during the pandemic.
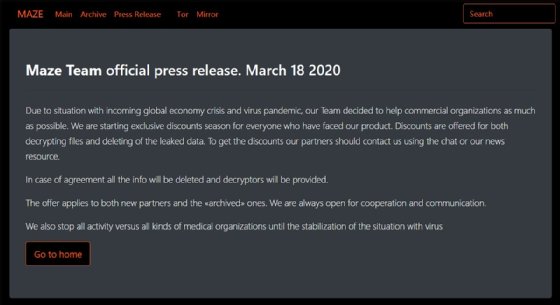
One such ransomware gang was Maze, which stated in a press release dated March 18 that "We also stop all activity versus all kinds of medical organizations until the stabilization of the situation with virus." Shortly after the organization had made its initial statements promising not to attack medical organizations, data for a London-based company, Hammersmith Medicines Research, was leaked by Maze operators who had hit the company days earlier. And in May, the operators published data from two separate plastic surgeons.
Mandiant senior vice president and strategic services CTO Charles Carmakal said the majority of healthcare organizations targeted by ransomware during the coronavirus pandemic do not include hospitals, but some are still being hit.
"As it comes to actively targeting hospitals, that's a line that most threat actors choose not to cross. Most people, most criminals, don't want to harm people -- they don't want to kill people in the process. A number of threat actors and groups have explicitly stated that they're not going to target hospitals, especially in the early COVID days," he said. "That said, we definitely know a few threat actors who have been actively targeting U.S.-based hospital organizations to attempt to make millions of dollars in extortion demands for ransom payments."
Carmakal stressed that when people talk about "healthcare" organizations being hit by ransomware, that does not refer only to hospitals. Healthcare organizations can include biotech companies, pharmaceutical companies, medical technology companies, and companies that provide business processing.
Research from Check Point showed that ransomware attacks on healthcare organizations globally have nearly doubled, from 2.3% of organizations in the second quarter of 2020 to 4% in the third quarter. In addition, in the United States, healthcare is the number one industry targeted.
The dangers of targeting hospitals
While hospitals represent a fraction of these attacks, Sophos senior security advisor John Shier noted that hospitals are "uniquely affected in that it's not just dollars that are being lost as with manufacturing or enterprise. Lives are potentially at stake."
This risk was demonstrated in the incident involving a 78-year-old woman in Germany last month who had to be diverted from Düsseldorf University Hospital, which had suffered a ransomware attack that shut down IT systems. The woman had to be taken to a different hospital in a neighboring city, where she was later pronounced dead, and German authorities launched a negligent homicide investigation as a result.
Düsseldorf University Hospital announced it had "deregistered from emergency care" because of the devastating ransomware attack. "This has far-reaching consequences for hospital operations, as activities in the computer system are necessary for many processes," the hospital said in a statement.
Shier explained how ransomware attacks cause hospitals to operate differently.
"It forces hospitals, or at least certain hospitals, to operate in a much different way than they're used to operating, and it forces them to do so very quickly to the point where it does result in some chaos and disarray in certain cases. Certain hospitals are reliant on electronic systems in order to do basic intake of patients into the emergency room, for example. Or, just looking up patient medical records. And if you don't have access to those, it can definitely either slow down or redirect some of these resources, and that is often at the expense of patient care," Shier said.
Hospitals also face greater cybersecurity risks due in part to the wide range of technology, both old and new hardware and software, that can be found within them.
Cyberattacks have caused hospitals to at least in part switch to more paper-based means of record keeping, and Carmakal explained that when computer systems go down and hospitals have to switch to paper, information like known allergies and medication lists can become much less immediately available.
How ransomware disrupts hospitals
Carmakal explained that the typical process for hospitals getting hit by ransomware follows multiple steps.
Initially, the threat actor finds a way into the organization -- commonly through email-based phishing or via vulnerabilities on internet-facing infrastructure -- and upon doing so, they create a backdoor and install malware on a user's computer. Because COVID-19 can cause work and personal computer use to blend more in a home office (employees are checking their personal emails on work computers), some phishing efforts will target personal emails without enterprise-level protections.
Secondly, the threat actor attempts to escalate privileges and move laterally until they have broad enough, high enough access to the environment, so that they can access backup systems, critical systems like domain controllers and Windows environments, as well as other systems and servers in the environment where, if they went offline, it would cause a large impact to the organization.
Finally, the threat actor encrypts every system they have access to, usually in the days leading up to a weekend when IT staff is typically lighter.
During the NotPetya cyberattacks of June 2017, Heritage Valley Health System hospitals in Pennsylvania were hit by ransomware as a result of one in-network computer being infected by a connected entity from outside the healthcare system's network. As the Sandworm indictment read, "By stealing and using Heritage Valley user credentials to self-propagate, the malware then spread from the initial infected Heritage Valley computer to other computers on Heritage Valley's computer network."
In addition to hard drives and workstations being locked, healthcare providers lost access to patient lists, patient medical records, prior laboratory records and a number of mission-critical computer systems (including, the indictment notes, those related to "cardiology, nuclear medicine, radiology, and surgery"). Outages ranged from about one week to one month.
Cybereason CISO Israel Barak said that the goal of ransomware has moved far beyond file encryption and into the territory of making full-capacity operation impossible.
"Modern ransomware attacks, where [many organizations] have been impacted by the same method of operation this year, are no longer merely about file encryption. Basically, when you think about these ransomware attacks, what these modern ransomware attacks are -- they're hacking operations, and they're designed to incapacitate and overwhelm their victims and gain maximum leverage by shutting down much of their victims' fundamental ability to operate," he said. "When you do that to a large enterprise, you can demand ransom sums of six and seven figures in exchange for, first and foremost, not the data, but the victim's ability to regain operational capability. And also in exchange for unlocking the data, and for guaranteeing not to disclose that trove of data that the attacker had stolen."
While ceasing operations may have been the modus operandi for ransomware operations lately, hospitals have also been facing such attacks since at least 2017 with the WannaCry attacks, as an article about ransomware published by the American Hospital Association (AHA) explained.
"The 2017 WannaCry ransomware attack infected 1,200 diagnostic devices, caused many others to be temporarily taken out of service to prevent the malware from spreading, and forced five United Kingdom hospital emergency departments to close and divert patients, according to an investigative report by the UK National Audit Office (NAO). The investigation also found the attack (which was launched against targets around the world) infected at least 81 of the 236 National Health System (NHS) hospitals in England plus 603 primary care and 595 medical practices, which caused more than 19,000 appointments to be canceled," author John Riggi, AHA's senior advisor for cybersecurity and risk, wrote.
Looking forward
Beyond the immediate effects of limiting or totally disrupting emergency care, ransomware attacks on hospitals can have lingering consequences. In a statement dated Oct. 12, Düsseldorf University Hospital said it was finally back up to normal patient numbers following the ransomware attack it suffered over a month prior on Sept. 10. The hospital said that emergency care was unavailable -- and ambulances could not be accepted -- until Sept. 23.
In a previous update, Düsseldorf University Hospital said the restoration of emergency services operations was performed in stages because of the different IT requirements. "An example of this is the delivery room, which has different IT network requirements than some specialized operation," the hospital said, adding that a critical prerequisite was restoring medical imaging systems for CT scans or X-ray images, which were impacted by the attack.
Mike McLellan, director of intelligence for the Secureworks Counter Threat Unit, told SearchSecurity that healthcare organizations, including hospitals, can face issues with cybersecurity investments.
"Healthcare organizations' primary focus is, quite rightly, on caring for people. However, they can suffer from a lack of investment in adequate security controls. In a climate of constrained resources and challenging priorities, the security of systems and sensitive data, while undoubtedly seen as important, may not get the attention that it needs -- until it's too late. This can leave organizations vulnerable, and an attractive target for unscrupulous criminals who have little regard for the real-world impact of their actions," McLellan said.
To help prevent ransomware in the future, McLellan said that organizations need to prioritize network hygiene.
"Trying to stop these attacks at the point where data is getting encrypted is futile. Most of the time, the perpetrators will have had access to the environment for days, possibly even weeks, before they deploy their ransomware," he said. "Hospitals -- and other organizations, because ransomware continues to be an indiscriminate and opportunistic threat -- need to focus on prevention through good network hygiene, and on protection and detection services that can identify the threat before it's too late."







