
beebright - Fotolia
SentinelOne: More supply chain attacks are coming
At RSA Conference 2021, SentinelOne threat researcher Marco Figueroa discussed the implications of the SolarWinds attacks, which he called one of the biggest hacks ever.
Large-scale supply chain attacks are here to stay, according to Marco Figueroa, principal threat researcher at SentinelOne.
During an RSA Conference 2021 session Wednesday, Figueroa dissected Sunburst, the malware used to compromise SolarWinds' Orion platform that led to an extensive supply chain attack on dozens of organizations. High-profile customers, from the federal government to some of the biggest security vendors, used the Orion software and were affected.
Threat actors installed a backdoor, dubbed Sunburst by FireEye, that was activated when those customers updated the software -- a common practice that has always been advised. Based on the SolarWinds timeline released in February, Figueroa discussed the access those threat actors had in what he referred to as the "biggest hack ever."
By targeting SolarWinds, the nation-state actors had access to 17,000 organizations, though the software vendor believes less than 100 customers were actually breached. Figueroa said there were three steps the attackers took once the backdoor executed. First, they stole keys to the Orion platform, then they specifically targeted organizations' emails and documents. Lastly, they targeted the victims' source code and software tools, just as they had done with SolarWinds.
The initial timeline of the SolarWinds breach raised several questions for Figueroa, but one in particular stood out.
"In eight days, the threat actors penetrated the network and knew precisely where to inject test code in the Orion platform? That was very odd to me and immediately stuck out," he said during the session.
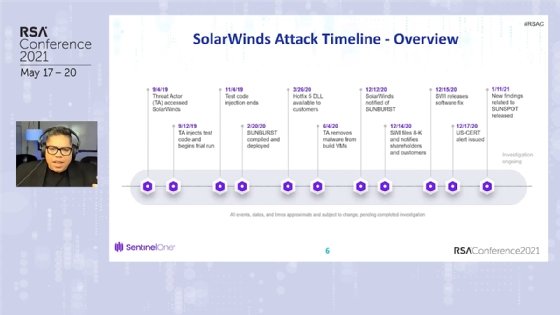
Figueroa said he believed the initial intrusion occurred much earlier than SolarWinds' previous timeline indicated, which placed the initial intrusion as early as September 2019. That belief was validated Wednesday morning during an RSA Conference keynote from SolarWinds president and CEO Sudhakar Ramakrishna, who said the company now believes the threat actors had access to the company network as far back as January 2019.
Other factors stood out as well, including the actors' ability to test the Sunburst code for two months to see if anyone detected it. Additionally, the code injected into the Orion platform blended in so perfectly no one knew about it.
Figueroa said it is likely the threat actors followed the same software development lifecycle that many enterprises -- including one of Figueroa's previous employers -- use, which includes stages for testing, security validation and quality assurance. Because SolarWinds was such a large environment to tackle, he said threat actors had to replicate everything. And he believes that patience may have been the most important factor in the success of the attack.
"The length of time it took -- it's practice, rehearse, practice, rehearse because you only have one shot. You can't mess this up," he said.
What surprised Figueroa the most was that no zero days were used. The attackers simply took advantage of a lot of low-hanging fruit, studied the SolarWinds environment and Orion product, and patiently tested their malware to ensure it didn't set off any alarms. Figueroa said that demonstrates that other threat actors could execute the same kind of supply chain attack on other targets, as long as they use similar levels of patience and preparation.
"As a researcher, I looked at this and appreciated the non-sophistication of this attack. We're not talking about the how, the when, we're just talking about what they did. That blew my mind," he said.
SolarWinds attack attribution
Last month, the Biden administration attributed the attack to the Russian Foreign Intelligence Service (SVR). During a White House press briefing, the administration said the U.S. intelligence community has high confidence in its assessment.
However, there is one attack Figueroa believed was not related to SVR: FireEye. And it was the one intrusion that led to the nation-state hackers being detected. FireEye was the first to disclose that a nation-state attack it suffered was part of the supply chain attack on SolarWinds. Figueroa said going after FireEye was a complete mistake -- and possibly not the work of the SVR.
"When they were going after them, they had to think to themselves, 'They're a security company; they're probably going to detect us.' I really don't think it was SVR going after them. I think it was one of the 10 companies that was sanctioned, because if you have a successful campaign, you want it to continue," he said.
Stopping future supply chain attacks
On the bright side, Figueroa said SentinelOne did not have a single customer breached by the SolarWinds attackers. The reason, he explained, was that a SentinelOne driver for its endpoint protection product was on the Sunburst block list because the agent for the product was tamper proof. As a result, Sunburst was programmed to not execute on any device where drivers were present.
Not only did Sunburst wait 14 days before initiating malicious activity, Figueroa said, the malware also checked developer tools and security services for any threat detection products and disabled the services through the system's registry.
While numerous reports and information have surfaced since the attack, Figueroa believes transparency is key to stopping future supply chain attacks. And to that end, there is far more information to be shared about SolarWinds, he said.
"You need hard facts. One of things that has limited researchers has been sharing of samples and artifacts by investigators. And I understand these companies have NDAs [non-disclosure agreements] and stuff like that, but this is bigger than just one company' NDA," he said. "You're talking about the biggest hack ever. Raindrop samples weren't initially shared due to legal reasons. Sunspot has yet to be released and Sibot samples have yet to be shared by Microsoft."
Additionally, Figueroa said it's hard to find something malicious if a binary blends into the environment, which further highlights the impending danger of supply chain attacks. "If there are no IOCs [indicators of compromise] or Yara rules do not detect it, how do you find it? Hunting is key," he said.
To hunt, security teams have to look for out-of-the-ordinary network activity or calls to different domains and cloud resources; but the threat actors used U.S.-based domains and cloud services that have not yet been named.
Figueroa commended FireEye's transparency, as the vendor continues to share its binaries. "I harp on transparency because I don't think this is a one-time thing. What happens if, through SolarWinds, they get into another company that didn't detect them?" he said.
To tackle supply chain security, Figueroa said safeguarding the software development lifecycle is a critical task. Enterprises should adopt firm practices for restricting access and employ security validation like fuzzing and diffing. He also recommended organizations create red teams and launch bug bounties.
Finally, Figueroa said, compromised victims should embrace DTA, or "don't trust anything"; immediately review every update, not just Orion software; and closely examine everything that was created after Sunburst was installed. To combat nation-state hackers that execute these attacks, he said, organizations should adopt the mindset of a threat actor rather than believing they dodged a bullet.






