
Getty Images/iStockphoto
Months after the Accellion breach, more victims emerge
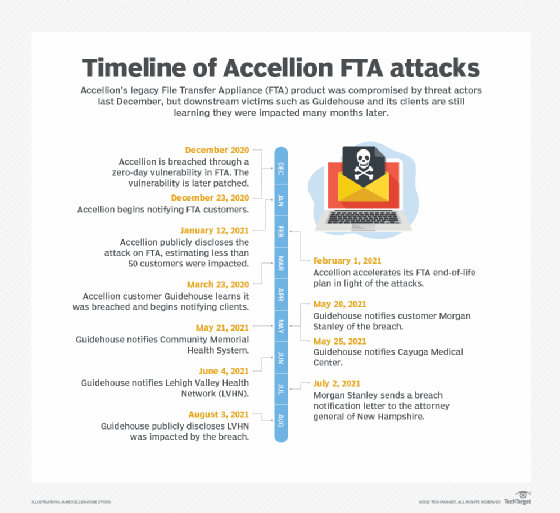
The Accellion breach occurred last December, but more victims have come to light in recent weeks as investigations, notifications and disclosures stretch on through the summer.
The effects from the Accellion breach continue to emerge as more downstream victims have come to light months after the initial attack.
The target of the attack was Accellion's legacy file-sharing product, File Transfer Appliance (FTA), which contained zero-day vulnerabilities. Threat actors exploited the zero-days in mid-December last year to gain control of FTA and used the access to send malicious updates to FTA customers. In some cases, targets were attacked by threat actors associated with the Clop ransomware group.
While patches were quickly released and Accellion later retired the 20-year-old software on April 30, several FTA customers disclosed attacks related to the breach, including Bombardier Inc., The Kroger Co. and the New South Wales Ministry of Health.
In some cases, the clients of FTA customers were impacted by the attacks. Fallout for one of those customers, consulting firm and managed service provider Guidehouse Inc., is ongoing as impacted clients continue to be revealed.
Guidehouse falls into the fray
Guidehouse's involvement in the FTA breach first emerged last month when its customer Morgan Stanley issued a data breach disclosure letter to the Office of the Attorney General of New Hampshire on July 2. According to the letter, Guidehouse notified the bank on May 20 that it had suffered an information security incident which impacted approximately 108 New Hampshire residents.
"Guidehouse advised us that data it maintained for Morgan Stanley had been accessed through the Accellion FTA vulnerability," the disclosure letter said.
SearchSecurity contacted Morgan Stanley for further details. A spokesperson referred to a statement from July 8 about the notification letter, which was first covered by Bleeping Computer.
"The protection of client data is of the utmost importance and is something we take very seriously. We are in close contact with the vendor involved and are taking steps to mitigate potential risks to clients," a Morgan Stanley spokesperson said in an email to SearchSecurity.
A Guidehouse spokesperson told SearchSecurity that after the company learned it had been the victim of a cyber attack related to the Accellion FTA breach in March (a separate notification letter from Guidehouse said the company learned it was impacted on March 23), it immediately discontinued use of the product and notified law enforcement. According to the spokesperson, there was no disruption to operations and its internal systems were not compromised.
"Guidehouse learned in late March 2021 that it had been the victim of a cyber-attack related to the Accellion File Transfer Appliance. We started notifying clients that same month. However, based on the sophisticated nature of the incident, for certain clients it took additional time to determine whether their data was impacted," a Guidehouse spokesperson said in an email to SearchSecurity.
It's unclear how Guidehouse learned it was affected by the FTA breach. Guidehouse did not respond to follow-up questions from SearchSecurity.
Reasons for the additional investigation time remain unclear, but many clients were not notified until recently.
Growing list of downstream victims
Three healthcare centers are among the Guidehouse customers affected through the FTA-related breach, two of which were notified at the end of May.
On May 21, Guidehouse informed Community Memorial Health System in Ventura, Calif., that its data had been impacted. Four days later, it notified Cayuga Medical Center in Ithaca, N.Y., which employs over 1,500 healthcare professionals and has a medical staff of more than 200 affiliated physicians.
The next healthcare center to be notified occurred on June 4, when Guidehouse alerted the Lehigh Valley Health Network (LVHN) that data had been stolen. Guidehouse provides consulting services to the health network, which serves the state of Pennsylvania. The LVHN data exposure wasn't publicly disclosed until earlier this month when Guidehouse announced the incident in a paid advertisement in The Morning Call, a news outlet in Pennsylvania.
LHVN provided a statement to SearchSecurity, which said a Guidehouse investigation determined that certain personal data including patients' medical record numbers, account numbers, dates of services, diagnosis and billing information may have been impacted.
"This incident did not involve any unauthorized access to any systems or files maintained by the LHVN information technology systems. We are not aware of any misuse of information," a LHVN spokesperson said in an email to SearchSecurity.
It's unclear if additional Guidehouse clients were affected and have yet to fully investigate and publicly disclose any impacts on customer data.
Delayed responses and notifications
Examining additional victims of the Accellion breach shows the long tail of the incident and its impact on customer data many months after the attack. Incident response investigations into possible breaches and notifications of exposed customer data have stretched on for weeks and months.
In a notice of breach disclosure from Arkansas Health and Wellness, the company said that on Jan. 25, Accellion informed them it was the victim of a cyber attack that compromised its file transfer platform. However, it wasn't until April 2 that an investigation by Arkansas Health and Wellness determined that the personally identifiable information of its members was involved in the incident.
On June 4, the New South Wales Ministry of Health said that it began notifying people whose data may have been accessed in the "global Accellion cyber-attack." According to the update, different types of information, including identity information and in some cases health-related personal information, were included in the attack.
"Following the NSW Government's advice earlier this year around a world-wide cyber-attack that included NSW Government agencies, NSW Health is notifying people whose data may have been accessed," the cyber attack update said. "Medical records in public hospitals were not affected and the software is no longer in use by NSW Health."
NSW Health said it has been working with NSW police and cyber security NSW and to date, there is no evidence any of the information has been misused.






